端口扫描
root@kali2 [/tmp] ➜ nmap -sV -A 192.168.56.19 -p21,25,53,80,88,110,135,139,143,389,445,464,587,593,636,3268,3269,5985,9389,47001,49664,49665,49670,49673,49674,49677,49685,49686,49689,49697,49703
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-06-06 14:46 CST
Nmap scan report for 192.168.56.19
Host is up (0.00030s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp?
| ftp-syst:
|_ SYST: UNIX emulated by FileZilla.
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, GenericLines, NULL, RPCCheck, SSLSessionReq, TLSSessionReq, TerminalServerCookie:
| 220-FileZilla Server 1.10.0
| Please visit https://filezilla-project.org/
| GetRequest:
| 220-FileZilla Server 1.10.0
| Please visit https://filezilla-project.org/
| What are you trying to do? Go away.
| HTTPOptions, RTSPRequest:
| 220-FileZilla Server 1.10.0
| Please visit https://filezilla-project.org/
| Wrong command.
| Help:
| 220-FileZilla Server 1.10.0
| Please visit https://filezilla-project.org/
| 214-The following commands are recognized.
| RNTO RNFR XPWD MDTM REST APPE MKD RMD DELE
| ALLO STOR SIZE CDUP CWD TYPE SYST MFMT MODE XRMD
| ADAT PROT PBSZ MLSD LIST XCWD NOOP AUTH OPTS EPRT
| PASS QUIT PWD RETR USER NLST CLNT FEAT ABOR HELP
| XMKD MLST STRU PASV EPSV PORT STAT
|_ Help ok.
|_ssl-date: TLS randomness does not represent time
|_ftp-anon: got code 503 "Use AUTH first.".
| ssl-cert: Subject: commonName=filezilla-server self signed certificate
| Not valid before: 2025-03-28T16:30:48
|_Not valid after: 2026-03-29T16:35:48
25/tcp open smtp hMailServer smtpd
| smtp-commands: CURIOSITY-DC, SIZE 20480000, AUTH LOGIN, HELP
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Nextech - Consultor\xC3\xADa Inform\xC3\xA1tica
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-06-06 06:46:16Z)
110/tcp open pop3 hMailServer pop3d
|_pop3-capabilities: TOP USER UIDL
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
143/tcp open imap hMailServer imapd
|_imap-capabilities: CAPABILITY IDLE SORT OK ACL RIGHTS=texkA0001 CHILDREN IMAP4rev1 IMAP4 QUOTA NAMESPACE completed
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: curiosity.thl0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
587/tcp open smtp hMailServer smtpd
| smtp-commands: CURIOSITY-DC, SIZE 20480000, AUTH LOGIN, HELP
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: curiosity.thl0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
49673/tcp open msrpc Microsoft Windows RPC
49674/tcp open msrpc Microsoft Windows RPC
49677/tcp open msrpc Microsoft Windows RPC
49685/tcp open msrpc Microsoft Windows RPC
49686/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49689/tcp open msrpc Microsoft Windows RPC
49697/tcp open msrpc Microsoft Windows RPC
49703/tcp open msrpc Microsoft Windows RPC域名curiosity.thl
root@kali2 [/tmp] ➜ dig any curiosity.thl @192.168.56.19 [15:24:49]
; <<>> DiG 9.19.21-1-Debian <<>> any curiosity.thl @192.168.56.19
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 24987
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 3, AUTHORITY: 0, ADDITIONAL: 2
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4000
;; QUESTION SECTION:
;curiosity.thl. IN ANY
;; ANSWER SECTION:
curiosity.thl. 600 IN A 192.168.56.19
curiosity.thl. 3600 IN NS curiosity-dc.curiosity.thl.
curiosity.thl. 3600 IN SOA curiosity-dc.curiosity.thl. hostmaster.curiosity.thl. 46 900 600 86400 3600
;; ADDITIONAL SECTION:
curiosity-dc.curiosity.thl. 3600 IN A 192.168.56.19
;; Query time: 0 msec
;; SERVER: 192.168.56.19#53(192.168.56.19) (TCP)
;; WHEN: Fri Jun 06 15:32:56 CST 2025
;; MSG SIZE rcvd: 148DC curiosity-dc.curiosity.thl 还有一个 hostmaster.curiosity.thl
80端口开了,先看下web
web
页面没什么信息,扫一下目录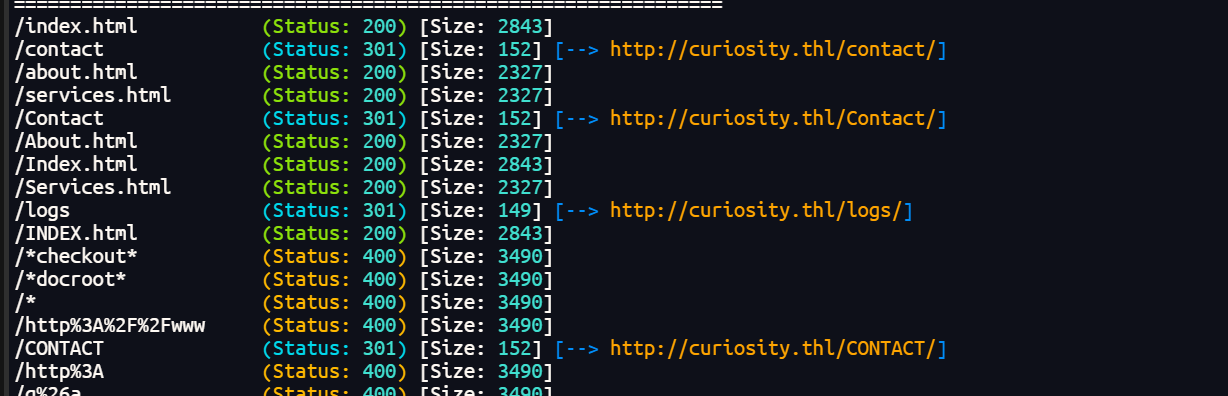
可以目录浏览,logs下面没东西,contact下面有东西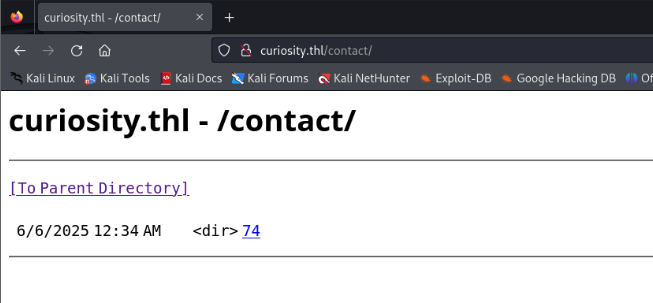
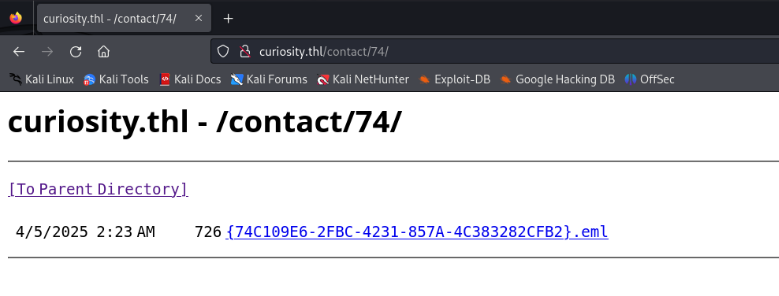
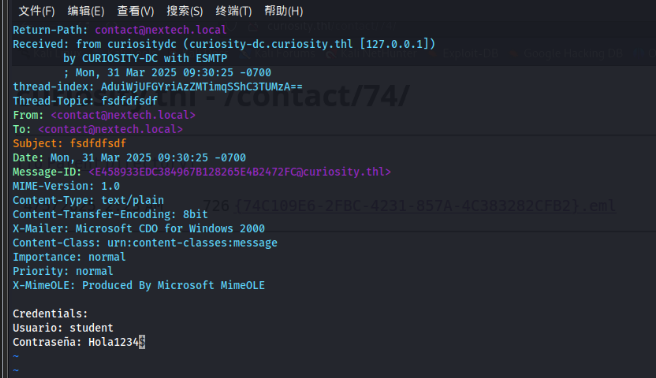
Return-Path: [email protected]
Received: from curiositydc (curiosity-dc.curiosity.thl [127.0.0.1])
by CURIOSITY-DC with ESMTP
; Mon, 31 Mar 2025 09:30:25 -0700
thread-index: AduiWjUFGYriAzZMTimqSShC3TUMzA==
Thread-Topic: fsdfdfsdf
From: <[email protected]>
To: <[email protected]>
Subject: fsdfdfsdf
Date: Mon, 31 Mar 2025 09:30:25 -0700
Message-ID: <[email protected]>
MIME-Version: 1.0
Content-Type: text/plain
Content-Transfer-Encoding: 8bit
X-Mailer: Microsoft CDO for Windows 2000
Content-Class: urn:content-classes:message
Importance: normal
Priority: normal
X-MimeOLE: Produced By Microsoft MimeOLE
Credentials:
Usuario: student
Contraseña: Hola1234$域控发来一个用户凭据student:Hola1234$,不过登不上去,随便发个邮件,发现contact目录下多一个
Return-Path: 2814928906@qq.com
Received: from curiositydc (curiosity-dc.curiosity.thl [127.0.0.1])
by CURIOSITY-DC with ESMTP
; Fri, 6 Jun 2025 02:24:01 -0700
thread-index: AdvWxL2CNVrlrvcyTQ6T5UXPFdxiYw==
Thread-Topic: abc
From: <2814928906@qq.com>
To: <[email protected]>
Subject: abc
Date: Fri, 6 Jun 2025 02:24:01 -0700
Message-ID: <[email protected]>
MIME-Version: 1.0
Content-Type: text/plain
Content-Transfer-Encoding: 8bit
X-Mailer: Microsoft CDO for Windows 2000
Content-Class: urn:content-classes:message
Importance: normal
Priority: normal
X-MimeOLE: Produced By Microsoft MimeOLE
Credentials:
Usuario: vicky.tale
Contraseña: Hola1234$拿到一个新的凭据vicky.tale:Hola1234$
WINRM 192.168.56.19 5985 CURIOSITY-DC [+] curiosity.thl\vicky.tale:Hola1234$ (Pwn3d!)拿下立足点
*Evil-WinRM* PS C:\Users> dir
Directory: C:\Users
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 4/5/2025 2:21 AM Administrator
d----- 4/5/2025 2:03 AM john.miller
d-r--- 3/28/2025 4:41 AM Public
d----- 6/6/2025 2:16 AM svcpool
d----- 4/1/2025 1:25 AM vicky.talevicky.tale这个用户没有flag
C:\windows\system32\tasks
TCP 127.0.0.1 14148 0.0.0.0 0 Listening 3044 filezilla-server
C:\Users\All Users\Microsoft\UEV\InboxTemplates\RoamingCredentialSettings.xml
C:\Program Files (x86)\hMailServer\PHPWebAdmin\config-dist.php
password=”[enc:IISWASOnlyCngProvider:FCD/44GP89zDEw2y34M3ScYkiMpvcL6VqBL/g6ePNauAkpBb1Lf1goaoahlqS3i91skdf3rKf+WRCBO7tw2HlFRUJTB5Zn5s1gAv/lWIjpA=:enc]” loadUserProfile=”true” />